71-VXLAN典型配置举例
本章节下载: 71-VXLAN典型配置举例 (320.81 KB)
H3C S6860产品VXLAN典型配置举例
Copyright © 2018 新华三技术有限公司 版权所有,保留一切权利。
非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本文档内容的部分或全部,并不得以任何形式传播。
除新华三技术有限公司的商标外,本手册中出现的其它公司的商标、产品标识及商品名称,由各自权利人拥有。
本文档中的信息可能变动,恕不另行通知。
本文档介绍VXLAN(Virtual eXtensible LAN,可扩展虚拟局域网络)的典型配置案例。VXLAN是基于IP网络、采用“MAC in UDP”封装形式的二层VPN技术。VXLAN可以基于已有的服务提供商或企业IP网络,为分散的物理站点提供二层互联,并能够为不同的租户提供业务隔离。VXLAN主要应用于数据中心网络。
本文档不严格与具体软、硬件版本对应,如果使用过程中与产品实际情况有差异,请以设备实际情况为准。
本文档中的配置均是在实验室环境下进行的配置和验证,配置前设备的所有参数均采用出厂时的缺省配置。如果您已经对设备进行了配置,为了保证配置效果,请确认现有配置和以下举例中的配置不冲突。
本文档假设您已了解VXLAN特性。
对于以太网服务实例的配置,S6860系列交换机具有如下使用限制:
· 在接口上创建以太网服务实例匹配当前接口接收的部分VLAN的报文后,以太网服务实例未匹配的其它VLAN内的组播流量将无法正常转发,请注意避免在上述情况下使用组播业务。
· 报文匹配规则为匹配带VLAN Tag的报文(encapsulation tagged)、匹配不带VLAN Tag的报文(encapsulation untagged)、缺省报文匹配规则(encapsulation default)时,AC的接入模式必须配置为Ethernet接入模式,否则设备向VM发送报文时无法判断为报文添加的VLAN tag。其他情况下,AC的接入模式既可以配置为Ethernet接入模式,也可以配置为VLAN接入模式。
· 以太网服务实例工作在VLAN接入模式时,如果从VXLAN隧道接收到的报文不携带VLAN tag,则发送报文时会添加s-vid或c-vid;如果从VXLAN隧道接收到的报文携带VLAN tag,则发送报文时不会添加VLAN tag。
· 在聚合接口上配置以太网服务实例后,该配置在聚合接口的成员端口上不会buildrun。
· 以太网服务实例所在的端口被STP协议阻塞时,以太网服务实例上的报文收发不受影响。
· 只有源端地址为本地接口地址、目的端地址存在对应路由时,VXLAN隧道接口才会up。多个VXLAN隧道接口的源和目的IP地址相同时,只会有一个VXLAN隧道接口up。
除此之外,S6860系列交换机还具有如下使用限制:
VTEP通过广播流量学习远端MAC地址,因此,不要执行flooding disable命令开启VSI的泛洪抑制功能。
Switch A、Switch B、Switch C为与服务器连接的VTEP设备。虚拟机VM 1、VM 2和VM 3同属于VXLAN 10。通过VXLAN实现不同站点间的二层互联,确保虚拟机在站点之间进行迁移时用户的访问流量不会中断。
图1 VXLAN二层转发配置举例
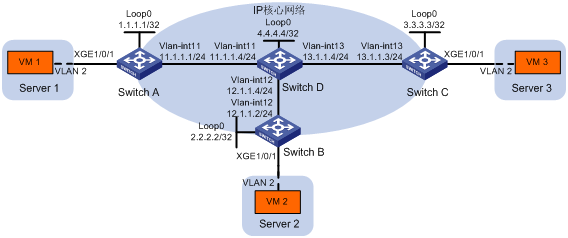
· 在IP核心网络上配置路由协议,使得各交换机的接口IP地址(包括Loopback接口IP地址)之间路由可达。本举例以OSPF路由协议为例。
· 在Switch A、Switch B和Switch C之间建立VXLAN隧道,并将VXLAN隧道与VXLAN关联,以便将虚拟机发送的二层报文封装为IP报文后在IP核心网络上转发。
· 在Switch A和Switch B的下行端口上配置以太网服务实例和相应的匹配规则,用来识别用户网络中的报文所属的VXLAN。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
# 配置Switch A的接口IP地址。
<SwitchA> system-view
[SwitchA] vlan 11
[SwitchA-vlan11] port ten-gigabitethernet 1/0/2
[SwitchA-vlan11] quit
[SwitchA] interface vlan-interface 11
[SwitchA-Vlan-interface11] ip address 11.1.1.1 24
[SwitchA-Vlan-interface11] quit
[SwitchA] interface loopback 0
[SwitchA-LoopBack0] ip address 1.1.1.1 32
# 请参考以上方法配置其它设备上的接口IP地址,配置步骤这里省略。
# 在Switch A上配置OSPF发布接口所在网段的路由。
[SwitchA] ospf 1 router-id 1.1.1.1
[SwitchA-ospf-1] area 0
[SwitchA-ospf-1-area-0.0.0.0] network 1.1.1.1 0.0.0.0
[SwitchA-ospf-1-area-0.0.0.0] network 11.1.1.0 0.0.0.255
[SwitchA-ospf-1-area-0.0.0.0] quit
[SwitchA-ospf-1] quit
# 在Switch B上配置OSPF发布接口所在网段的路由。
[SwitchB] ospf 1 router-id 2.2.2.2
[SwitchB-ospf-1] area 0
[SwitchB-ospf-1-area-0.0.0.0] network 2.2.2.2 0.0.0.0
[SwitchB-ospf-1-area-0.0.0.0] network 12.1.1.0 0.0.0.255
[SwitchB-ospf-1-area-0.0.0.0] quit
[SwitchB-ospf-1] quit
# 在Switch C上配置OSPF发布接口所在网段的路由。
[SwitchC] ospf 1 router-id 3.3.3.3
[SwitchC-ospf-1] area 0
[SwitchC-ospf-1-area-0.0.0.0] network 3.3.3.3 0.0.0.0
[SwitchC-ospf-1-area-0.0.0.0] network 13.1.1.0 0.0.0.255
[SwitchC-ospf-1-area-0.0.0.0] quit
[SwitchC-ospf-1] quit
# 在Switch D上配置OSPF发布接口所在网段的路由。
[SwitchD] ospf 1 router-id 4.4.4.4
[SwitchD-ospf-1] area 0
[SwitchD-ospf-1-area-0.0.0.0] network 4.4.4.4 0.0.0.0
[SwitchD-ospf-1-area-0.0.0.0] network 11.1.1.0 0.0.0.255
[SwitchD-ospf-1-area-0.0.0.0] network 12.1.1.0 0.0.0.255
[SwitchD-ospf-1-area-0.0.0.0] network 13.1.1.0 0.0.0.255
[SwitchD-ospf-1-area-0.0.0.0] quit
[SwitchD-ospf-1] quit
# 开启L2VPN功能。
[SwitchA] l2vpn enable
# 创建VXLAN 10。
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan10] quit
[SwitchA-vsi-vpna] quit
# 开启L2VPN功能。
[SwitchB] l2vpn enable
# 创建VXLAN 10。
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan10] quit
[SwitchB-vsi-vpna] quit
# 开启L2VPN功能。
[SwitchC] l2vpn enable
# 创建VXLAN 10。
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] vxlan 10
[SwitchC-vsi-vpna-vxlan10] quit
[SwitchC-vsi-vpna] quit
# 在Switch A上创建到达Switch B和Switch C的VXLAN隧道Tunnel1和Tunnel2。
[SwitchA] interface tunnel 1 mode vxlan
[SwitchA-Tunnel1] source 1.1.1.1
[SwitchA-Tunnel1] destination 2.2.2.2
[SwitchA-Tunnel1] quit
[SwitchA] interface tunnel 2 mode vxlan
[SwitchA-Tunnel2] source 1.1.1.1
[SwitchA-Tunnel2] destination 3.3.3.3
[SwitchA-Tunnel2] quit
# 在Switch B上创建到达Switch A和Switch C的VXLAN隧道Tunnel1和Tunnel2。
[SwitchB] interface tunnel 1 mode vxlan
[SwitchB-Tunnel1] source 2.2.2.2
[SwitchB-Tunnel1] destination 1.1.1.1
[SwitchB-Tunnel1] quit
[SwitchB] interface tunnel 2 mode vxlan
[SwitchB-Tunnel2] source 2.2.2.2
[SwitchB-Tunnel2] destination 3.3.3.3
[SwitchB-Tunnel2] quit
# 在Switch C上创建到达Switch A和Switch B的VXLAN隧道Tunnel1和Tunnel2。
[SwitchC] interface tunnel 1 mode vxlan
[SwitchC-Tunnel1] source 3.3.3.3
[SwitchC-Tunnel1] destination 1.1.1.1
[SwitchC-Tunnel1] quit
[SwitchC] interface tunnel 2 mode vxlan
[SwitchC-Tunnel2] source 3.3.3.3
[SwitchC-Tunnel2] destination 2.2.2.2
[SwitchC-Tunnel2] quit
# 在Switch A上将VXLAN隧道Tunnel1和Tunnel2均与VXLAN 10关联。
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan10] tunnel 1
[SwitchA-vsi-vpna-vxlan10] tunnel 2
[SwitchA-vsi-vpna-vxlan10] quit
[SwitchA-vsi-vpna] quit
# 在Switch B上将VXLAN隧道Tunnel1和Tunnel2均与VXLAN 10关联。
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan10] tunnel 1
[SwitchB-vsi-vpna-vxlan10] tunnel 2
[SwitchB-vsi-vpna-vxlan10] quit
[SwitchB-vsi-vpna] quit
# 在Switch C上将VXLAN隧道Tunnel1和Tunnel2均与VXLAN 10关联。
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] vxlan 10
[SwitchC-vsi-vpna-vxlan10] tunnel 1
[SwitchC-vsi-vpna-vxlan10] tunnel 2
[SwitchC-vsi-vpna-vxlan10] quit
[SwitchC-vsi-vpna] quit
# 在Switch A的接口Ten-GigabitEthernet1/0/1上创建以太网服务实例1000,该实例用来匹配VLAN 2(VM 1)的数据帧,将该服务实例与vpna(VXLAN 10)关联。
[SwitchA] interface ten-gigabitethernet 1/0/1
[SwitchA-Ten-GigabitEthernet1/0/1] service-instance 1000
[SwitchA-Ten-GigabitEthernet1/0/1-srv1000] encapsulation s-vid 2
[SwitchA-Ten-GigabitEthernet1/0/1-srv1000] xconnect vsi vpna
[SwitchA-Ten-GigabitEthernet1/0/1-srv1000] quit
[SwitchA-Ten-GigabitEthernet1/0/1] quit
# 在Switch B的接口Ten-GigabitEthernet1/0/1上创建以太网服务实例1000,该实例用来匹配VLAN 2(VM 2)的数据帧,将该服务实例与vpna(VXLAN 10)关联。
[SwitchB] interface ten-gigabitethernet 1/0/1
[SwitchB-Ten-GigabitEthernet1/0/1] service-instance 1000
[SwitchB-Ten-GigabitEthernet1/0/1-srv1000] encapsulation s-vid 2
[SwitchB-Ten-GigabitEthernet1/0/1-srv1000] xconnect vsi vpna
[SwitchB-Ten-GigabitEthernet1/0/1-srv1000] quit
[SwitchB-Ten-GigabitEthernet1/0/1] quit
# 在Switch C的接口Ten-GigabitEthernet1/0/1上创建以太网服务实例1000,该实例用来匹配VLAN 2(VM 3)的数据帧,将该服务实例与vpna(VXLAN 10)关联。
[SwitchC] interface ten-gigabitethernet 1/0/1
[SwitchC-Ten-GigabitEthernet1/0/1] service-instance 1000
[SwitchC-Ten-GigabitEthernet1/0/1-srv1000] encapsulation s-vid 2
[SwitchC-Ten-GigabitEthernet1/0/1-srv1000] xconnect vsi vpna
[SwitchC-Ten-GigabitEthernet1/0/1-srv1000] quit
[SwitchC-Ten-GigabitEthernet1/0/1] quit
# 以Switch A为例,查看Tunnel接口信息,可以看到VXLAN模式的Tunnel接口处于up状态。
[SwitchA] display interface tunnel
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 1.1.1.1, destination 2.2.2.2
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
Tunnel2
Current state: UP
Line protocol state: UP
Description: Tunnel2 Interface
Bandwidth: 64kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 1.1.1.1, destination 3.3.3.3
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# 以Switch A为例,查看VSI信息,可以看到与VXLAN关联的VXLAN隧道、与VSI关联的以太网服务实例均处于up状态。
[SwitchA] display l2vpn vsi verbose
VSI Name: vpna
VSI Index : 0
VSI State : Up
MTU : 1500
Bandwidth : Unlimited
Broadcast Restrain : Unlimited
Multicast Restrain : Unlimited
Unknown Unicast Restrain: Unlimited
MAC Learning : Enabled
MAC Table Limit : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
VXLAN ID : 10
Tunnels:
Tunnel Name Link ID State Type Flood proxy
Tunnel1 0x5000001 Up Manual Disabled
Tunnel2 0x5000002 Up Manual Disabled
ACs:
AC Link ID State Type
XGE1/0/1 srv1000 0 Up Manual
# 虚拟机VM 1、VM 2、VM 3之间可以互相ping通。
# 以Switch A为例,查看VSI的MAC地址表项信息,可以看到已学习到的MAC地址信息。
[SwitchA] display l2vpn mac-address
MAC Address State VSI Name Link ID/Name Aging
0010-9400-0002 Dynamic vpna Tunnel Aging
0010-9400-0003 Dynamic vpna XGE1/0/1 Aging
--- 2 mac address(es) found ---
· Switch A
#
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 11.1.1.0 0.0.0.255
#
vlan 11
#
l2vpn enable
#
vsi vpna
vxlan 10
tunnel 1
tunnel 2
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
interface Vlan-interface11
ip address 11.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
service-instance 1000
encapsulation s-vid 2
xconnect vsi vpna
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 11
#
interface Tunnel1 mode vxlan
source 1.1.1.1
destination 2.2.2.2
#
interface Tunnel2 mode vxlan
source 1.1.1.1
destination 3.3.3.3
#
return
· Switch B
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 2.2.2.2 0.0.0.0
network 12.1.1.0 0.0.0.255
#
vlan 12
#
l2vpn enable
#
vsi vpna
vxlan 10
tunnel 1
tunnel 2
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
#
interface Vlan-interface12
ip address 12.1.1.2 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
service-instance 1000
encapsulation s-vid 2
xconnect vsi vpna
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 12
#
interface Tunnel1 mode vxlan
source 2.2.2.2
destination 1.1.1.1
#
interface Tunnel2 mode vxlan
source 2.2.2.2
destination 3.3.3.3
#
return
· Switch C
#
ospf 1 router-id 3.3.3.3
area 0.0.0.0
network 3.3.3.3 0.0.0.0
network 13.1.1.0 0.0.0.255
#
vlan 13
#
l2vpn enable
#
vsi vpna
vxlan 10
tunnel 1
tunnel 2
#
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
interface Vlan-interface13
ip address 13.1.1.3 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
service-instance 1000
encapsulation s-vid 2
xconnect vsi vpna
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 13
#
interface Tunnel1 mode vxlan
source 3.3.3.3
destination 1.1.1.1
#
interface Tunnel2 mode vxlan
source 3.3.3.3
destination 2.2.2.2
#
return
· Switch D
#
ospf 1 router-id 4.4.4.4
area 0.0.0.0
network 4.4.4.4 0.0.0.0
network 11.1.1.0 0.0.0.255
network 12.1.1.0 0.0.0.255
network 13.1.1.0 0.0.0.255
#
vlan 11
#
vlan 12
#
vlan 13
#
interface LoopBack0
ip address 4.4.4.4 255.255.255.255
#
interface Vlan-interface11
ip address 11.1.1.4 255.255.255.0
#
interface Vlan-interface12
ip address 12.1.1.4 255.255.255.0
#
interface Vlan-interface13
ip address 13.1.1.4 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 11
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 12
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 13
#
return
如图2所示,虚拟机VM 1、VM 3属于VXLAN 10,VM 2和VM 4属于VXLAN 20。Switch A、Switch B为与服务器连接的VTEP设备,Switch C为与广域网连接的集中式VXLAN IP网关设备。通过VXLAN实现不同站点间的二层互联,并通过集中式VXLAN IP网关实现不同VXLAN之间、VXLAN与广域网之间的三层互联。
图2 集中式VXLAN IP网关配置组网图
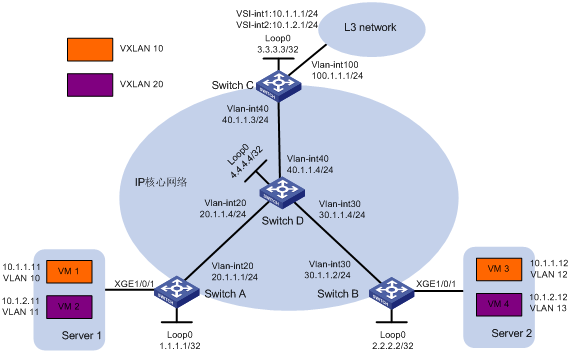
· 在IP核心网络上配置路由协议,使得各交换机的接口IP地址(包括Loopback接口IP地址)之间路由可达。本举例以OSPF路由协议为例。
· 在Switch A、Switch B和Switch C之间建立VXLAN隧道,并将VXLAN隧道与VXLAN关联,以便将虚拟机发送的二层报文封装为IP报文后在IP核心网络上转发。
· 在Switch A和Switch B的下行端口上配置以太网服务实例和相应的匹配规则,用来识别用户网络中的报文所属的VXLAN。
· 在集中式VXLAN IP网关Switch C上为每个VXLAN分别创建一个VSI虚接口,为其配置IP地址,该地址作为各自VXLAN内虚拟机的网关地址;在Switch C上配置路由协议将VSI虚接口、Vlan-interface100所在网段路由发布到L3 network,以便L3 network内的节点具有到达虚拟机的路由,本举例以OSPF路由协议为例。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
# 配置Switch A的接口IP地址。
<SwitchA> system-view
[SwitchA] vlan 20
[SwitchA-vlan20] port ten-gigabitethernet 1/0/2
[SwitchA-vlan20] quit
[SwitchA] interface vlan-interface 20
[SwitchA-Vlan-interface20] ip address 20.1.1.1 24
[SwitchA-Vlan-interface20] quit
[SwitchA] interface loopback 0
[SwitchA-LoopBack0] ip address 1.1.1.1 32
# 请参考以上方法配置其它设备上的接口IP地址,配置步骤这里省略。
# 在Switch A上配置OSPF发布接口所在网段的路由。
[SwitchA] ospf 1 router-id 1.1.1.1
[SwitchA-ospf-1] area 0
[SwitchA-ospf-1-area-0.0.0.0] network 1.1.1.1 0.0.0.0
[SwitchA-ospf-1-area-0.0.0.0] network 20.1.1.0 0.0.0.255
[SwitchA-ospf-1-area-0.0.0.0] quit
[SwitchA-ospf-1] quit
# 在Switch B上配置OSPF发布接口所在网段的路由。
[SwitchB] ospf 1 router-id 2.2.2.2
[SwitchB-ospf-1] area 0
[SwitchB-ospf-1-area-0.0.0.0] network 2.2.2.2 0.0.0.0
[SwitchB-ospf-1-area-0.0.0.0] network 30.1.1.0 0.0.0.255
[SwitchB-ospf-1-area-0.0.0.0] quit
[SwitchB-ospf-1] quit
# 在Switch C上配置OSPF发布接口所在网段的路由。
[SwitchC] ospf 1 router-id 3.3.3.3
[SwitchC-ospf-1] area 0
[SwitchC-ospf-1-area-0.0.0.0] network 3.3.3.3 0.0.0.0
[SwitchC-ospf-1-area-0.0.0.0] network 40.1.1.0 0.0.0.255
[SwitchC-ospf-1-area-0.0.0.0] quit
[SwitchC-ospf-1] quit
# 在Switch D上配置OSPF发布接口所在网段的路由。
[SwitchD] ospf 1 router-id 4.4.4.4
[SwitchD-ospf-1] area 0
[SwitchD-ospf-1-area-0.0.0.0] network 4.4.4.4 0.0.0.0
[SwitchD-ospf-1-area-0.0.0.0] network 20.1.1.0 0.0.0.255
[SwitchD-ospf-1-area-0.0.0.0] network 30.1.1.0 0.0.0.255
[SwitchD-ospf-1-area-0.0.0.0] network 40.1.1.0 0.0.0.255
[SwitchD-ospf-1-area-0.0.0.0] quit
[SwitchD-ospf-1] quit
# 开启L2VPN功能。
[SwitchA] l2vpn enable
# 创建VXLAN 10和VXLAN 20。
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan10] quit
[SwitchA-vsi-vpna] quit
[SwitchA] vsi vpnb
[SwitchA-vsi-vpnb] vxlan 20
[SwitchA-vsi-vpnb-vxlan10] quit
[SwitchA-vsi-vpnb] quit
# 开启L2VPN功能。
[SwitchB] l2vpn enable
# 创建VXLAN 10和VXLAN 20。
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan10] quit
[SwitchB-vsi-vpna] quit
[SwitchB] vsi vpnb
[SwitchB-vsi-vpnb] vxlan 20
[SwitchB-vsi-vpnb-vxlan10] quit
[SwitchB-vsi-vpnb] quit
# 开启L2VPN功能。
[SwitchC] l2vpn enable
# 配置VXLAN的硬件资源模式(该配置需要保存并重启设备才能生效,重启设备的具体配置步骤这里省略)。
[SwitchC] hardware-resource vxlan l3gw8k
# 创建VXLAN 10和VXLAN 20。
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] vxlan 10
[SwitchC-vsi-vpna-vxlan10] quit
[SwitchC-vsi-vpna] quit
[SwitchC] vsi vpnb
[SwitchC-vsi-vpnb] vxlan 20
[SwitchC-vsi-vpnb-vxlan10] quit
[SwitchC-vsi-vpnb] quit
# 在Switch A上创建到达Switch B和Switch C的VXLAN隧道Tunnel1和Tunnel2。
[SwitchA] interface tunnel 1 mode vxlan
[SwitchA-Tunnel1] source 1.1.1.1
[SwitchA-Tunnel1] destination 2.2.2.2
[SwitchA-Tunnel1] quit
[SwitchA] interface tunnel 2 mode vxlan
[SwitchA-Tunnel2] source 1.1.1.1
[SwitchA-Tunnel2] destination 3.3.3.3
[SwitchA-Tunnel2] quit
# 在Switch B上创建到达Switch A和Switch C的VXLAN隧道Tunnel1和Tunnel2。
[SwitchB] interface tunnel 1 mode vxlan
[SwitchB-Tunnel1] source 2.2.2.2
[SwitchB-Tunnel1] destination 1.1.1.1
[SwitchB-Tunnel1] quit
[SwitchB] interface tunnel 2 mode vxlan
[SwitchB-Tunnel2] source 2.2.2.2
[SwitchB-Tunnel2] destination 3.3.3.3
[SwitchB-Tunnel2] quit
# 在Switch C上创建到达Switch A和Switch B的VXLAN隧道Tunnel1和Tunnel2。
[SwitchC] interface tunnel 1 mode vxlan
[SwitchC-Tunnel1] source 3.3.3.3
[SwitchC-Tunnel1] destination 1.1.1.1
[SwitchC-Tunnel1] quit
[SwitchC] interface tunnel 2 mode vxlan
[SwitchC-Tunnel2] source 3.3.3.3
[SwitchC-Tunnel2] destination 2.2.2.2
[SwitchC-Tunnel2] quit
# 在Switch A上将VXLAN隧道Tunnel1和Tunnel2均与VXLAN 10、VXLAN 20关联。
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan10] tunnel 1
[SwitchA-vsi-vpna-vxlan10] tunnel 2
[SwitchA-vsi-vpna-vxlan10] quit
[SwitchA-vsi-vpna] quit
[SwitchA] vsi vpnb
[SwitchA-vsi-vpnb] vxlan 20
[SwitchA-vsi-vpnb-vxlan20] tunnel 1
[SwitchA-vsi-vpnb-vxlan20] tunnel 2
[SwitchA-vsi-vpnb-vxlan20] quit
[SwitchA-vsi-vpnb] quit
# 在Switch B上将VXLAN隧道Tunnel1和Tunnel2均与VXLAN 10、VXLAN 20关联。
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan10] tunnel 1
[SwitchB-vsi-vpna-vxlan10] tunnel 2
[SwitchB-vsi-vpna-vxlan10] quit
[SwitchB-vsi-vpna] quit
[SwitchB] vsi vpnb
[SwitchB-vsi-vpnb] vxlan 20
[SwitchB-vsi-vpnb-vxlan20] tunnel 1
[SwitchB-vsi-vpnb-vxlan20] tunnel 2
[SwitchB-vsi-vpnb-vxlan20] quit
[SwitchB-vsi-vpnb] quit
# 在Switch C上将VXLAN隧道Tunnel1和Tunnel2均与VXLAN 10、VXLAN 20关联。
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] vxlan 10
[SwitchC-vsi-vpna-vxlan10] tunnel 1
[SwitchC-vsi-vpna-vxlan10] tunnel 2
[SwitchC-vsi-vpna-vxlan10] quit
[SwitchC-vsi-vpna] quit
[SwitchC] vsi vpnb
[SwitchC-vsi-vpnb] vxlan 20
[SwitchC-vsi-vpnb-vxlan20] tunnel 1
[SwitchC-vsi-vpnb-vxlan20] tunnel 2
[SwitchC-vsi-vpnb-vxlan20] quit
[SwitchC-vsi-vpnb] quit
# 在接口Ten-GigabitEthernet1/0/1上创建以太网服务实例1000,该实例用来匹配VLAN 10(VM 1)的数据帧,将该服务实例与vpna(VXLAN 10)关联。
[SwitchA] interface ten-gigabitethernet 1/0/1
[SwitchA-Ten-GigabitEthernet1/0/1] service-instance 1000
[SwitchA-Ten-GigabitEthernet1/0/1-srv1000] encapsulation s-vid 10
[SwitchA-Ten-GigabitEthernet1/0/1-srv1000] xconnect vsi vpna
[SwitchA-Ten-GigabitEthernet1/0/1-srv1000] quit
# 在接口Ten-GigabitEthernet1/0/1上创建以太网服务实例2000,该实例用来匹配VLAN 11(VM 2)的数据帧,将该服务实例与vpnb(VXLAN 20)关联。
[SwitchA-Ten-GigabitEthernet1/0/1] service-instance 2000
[SwitchA-Ten-GigabitEthernet1/0/1-srv2000] encapsulation s-vid 11
[SwitchA-Ten-GigabitEthernet1/0/1-srv2000] xconnect vsi vpnb
[SwitchA-Ten-GigabitEthernet1/0/1-srv2000] quit
[SwitchA-Ten-GigabitEthernet1/0/1] quit
# 在接口Ten-GigabitEthernet1/0/1上创建以太网服务实例1000,该实例用来匹配VLAN 12(VM 3)的数据帧,将该服务实例与vpna(VXLAN 10)关联。
[SwitchB] interface ten-gigabitethernet 1/0/1
[SwitchB-Ten-GigabitEthernet1/0/1] service-instance 1000
[SwitchB-Ten-GigabitEthernet1/0/1-srv1000] encapsulation s-vid 12
[SwitchB-Ten-GigabitEthernet1/0/1-srv1000] xconnect vsi vpna
[SwitchB-Ten-GigabitEthernet1/0/1-srv1000] quit
# 在接口Ten-GigabitEthernet1/0/1上创建以太网服务实例2000,该实例用来匹配VLAN 13(VM 4)的数据帧,将该服务实例与vpnb(VXLAN 20)关联。
[SwitchB-Ten-GigabitEthernet1/0/1] service-instance 2000
[SwitchB-Ten-GigabitEthernet1/0/1-srv2000] encapsulation s-vid 13
[SwitchB-Ten-GigabitEthernet1/0/1-srv2000] xconnect vsi vpnb
[SwitchB-Ten-GigabitEthernet1/0/1-srv2000] quit
[SwitchB-Ten-GigabitEthernet1/0/1] quit
# 创建VSI虚接口VSI-interface1,并为其配置IP地址,该IP地址作为VXLAN 10内虚拟机的网关地址。
[SwitchC] interface vsi-interface 1
[SwitchC-Vsi-interface1] ip address 10.1.1.1 255.255.255.0
[SwitchC-Vsi-interface1] quit
# 配置VXLAN 10所在的VSI实例与接口VSI-interface1关联。
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] gateway vsi-interface 1
[SwitchC-vsi-vpna] quit
# 创建VSI虚接口VSI-interface2,并为其配置IP地址,该IP地址作为VXLAN 20内虚拟机的网关地址。
[SwitchC] interface vsi-interface 2
[SwitchC-Vsi-interface2] ip address 10.1.2.1 255.255.255.0
[SwitchC-Vsi-interface2] quit
# 配置VXLAN 20所在的VSI实例与接口VSI-interface2关联。
[SwitchC] vsi vpnb
[SwitchC-vsi-vpnb] gateway vsi-interface 2
[SwitchC-vsi-vpnb] quit
# 配置OSPF发布VSI虚接口、Vlan-interface100接口所在网段的路由。(与SwitchC相连的公网设备上也需要配置OSPF,发布自己的网段路由)
[SwitchC] ospf 2 router-id 3.3.3.3
[SwitchC-ospf-2] area 0
[SwitchC-ospf-2-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[SwitchC-ospf-2-area-0.0.0.0] network 10.1.2.0 0.0.0.255
[SwitchC-ospf-2-area-0.0.0.0] network 100.1.1.0 0.0.0.255
[SwitchC-ospf-2-area-0.0.0.0] quit
[SwitchC-ospf-2] quit
# 以Switch A为例,在VTEP上查看Tunnel接口信息,可以看到VXLAN模式的Tunnel接口处于up状态。
[SwitchA] display interface tunnel
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 1.1.1.1, destination 2.2.2.2
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
Tunnel2
Current state: UP
Line protocol state: UP
Description: Tunnel2 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 1.1.1.1, destination 3.3.3.3
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# 在集中式VXLAN IP网关Switch C上,查看Tunnel接口信息,可以看到VXLAN模式的Tunnel接口处于up状态。
[SwitchC] display interface tunnel
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 3.3.3.3, destination 1.1.1.1
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
Tunnel2
Current state: UP
Line protocol state: UP
Description: Tunnel2 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 3.3.3.3, destination 2.2.2.2
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# 在Switch C上,查看VSI虚接口信息,可以看到VSI虚接口处于up状态。
[SwitchC] display interface vsi-interface
Vsi-interface1
Current state: UP
Line protocol state: UP
Description: Vsi-interface1 Interface
Bandwidth: 1000000 kbps
Maximum transmission unit: 1444
Internet Address: 10.1.1.1/24 (primary)
IP packet frame type: Ethernet II, hardware address: 0000-fc00-458d
IPv6 packet frame type: Ethernet II, hardware address: 0000-fc00-458d
Physical: Unknown, baudrate: 1000000 kbps
Last clearing of counters: Never
Input (total): 0 packets, 0 bytes
Output (total): 0 packets, 0 bytes
Vsi-interface2
Current state: UP
Line protocol state: UP
Description: Vsi-interface2 Interface
Bandwidth: 1000000 kbps
Maximum transmission unit: 1500
Internet Address: 10.1.2.1/24 (primary)
IP packet frame type: Ethernet II, hardware address: 0000-fc00-458d
IPv6 packet frame type: Ethernet II, hardware address: 0000-fc00-458d
Physical: Unknown, baudrate: 1000000 kbps
Last clearing of counters: Never
Input (total): 0 packets, 0 bytes
Output (total): 0 packets, 0 bytes
# 以Switch A为例,在VTEP上查看VSI信息,可以看到VSI内创建的VXLAN、与VXLAN关联的VXLAN隧道、与VSI关联的以太网服务实例等信息。
[SwitchA] display l2vpn vsi verbose
VSI Name: vpna
VSI Index : 0
VSI State : Up
MTU : 1500
Bandwidth : Unlimited
Broadcast Restrain : Unlimited
Multicast Restrain : Unlimited
Unknown Unicast Restrain: Unlimited
MAC Learning : Enabled
MAC Table Limit : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
VXLAN ID : 10
Tunnels:
Tunnel Name Link ID State Type Flood proxy
Tunnel1 0x5000001 Up Manual Disabled
Tunnel2 0x5000002 Up Manual Disabled
ACs:
AC Link ID State Type
XGE1/0/1 srv1000 0 Up Manual
VSI Name: vpnb
VSI Index : 1
VSI State : Up
MTU : 1500
Bandwidth : Unlimited
Broadcast Restrain : Unlimited
Multicast Restrain : Unlimited
Unknown Unicast Restrain: Unlimited
MAC Learning : Enabled
MAC Table Limit : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
VXLAN ID : 20
Tunnels:
Tunnel Name Link ID State Type Flood proxy
Tunnel1 0x5000001 Up Manual Disabled
Tunnel2 0x5000002 Up Manual Disabled
ACs:
AC Link ID State Type
XGE1/0/1 srv2000 0 Up Manual
# 在Switch C上查看VSI信息,可以看到VSI内创建的VXLAN、与VXLAN关联的VXLAN隧道、与VSI关联的VSI虚接口等信息。
[SwitchC] display l2vpn vsi verbose
VSI Name: vpna
VSI Index : 0
VSI State : Up
MTU : 1500
Bandwidth : Unlimited
Broadcast Restrain : Unlimited
Multicast Restrain : Unlimited
Unknown Unicast Restrain: Unlimited
MAC Learning : Enabled
MAC Table Limit : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
Gateway interface : VSI-interface 1
VXLAN ID : 10
Tunnels:
Tunnel Name Link ID State Type Flooding proxy
Tunnel1 0x5000002 Up Manual Disabled
Tunnel2 0x5000003 Up Manual Disabled
VSI Name: vpnb
VSI Index : 1
VSI State : Up
MTU : 1500
Bandwidth : Unlimited
Broadcast Restrain : Unlimited
Multicast Restrain : Unlimited
Unknown Unicast Restrain: Unlimited
MAC Learning : Enabled
MAC Table Limit : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
Gateway interface : VSI-interface 2
VXLAN ID : 20
Tunnels:
Tunnel Name Link ID State Type Flooding proxy
Tunnel1 0x5000002 Up Manual Disabled
Tunnel2 0x5000003 Up Manual Disabled
# 虚拟机VM 1、VM 2、VM3、VM4之间均可以互访,且可以ping通100.1.1.1。
# 查看Switch C上VSI的ARP表项信息,可以看到已学习到了虚拟机的ARP信息。
[SwitchC] display arp
Type: S-Static D-Dynamic O-Openflow R-Rule M-Multiport I-Invalid
IP address MAC address VLAN/VSI Interface/Link ID Aging Type
10.1.1.11 0000-1234-0001 N/A Tunnel1 20 D
10.1.1.12 0000-1234-0002 N/A Tunnel2 19 D
# 查看Switch C上FIB表项信息,可以看到已学习到了虚拟机的转发表项信息。
[SwitchC] display fib 10.1.1.11
Destination count: 1 FIB entry count: 1
Flag:
U:Useable G:Gateway H:Host B:Blackhole D:Dynamic S:Static
R:Relay F:FRR
Destination/Mask Nexthop Flag OutInterface/Token Label
10.1.1.11/32 10.1.1.11 UH Vsi1 Null
· Switch A
#
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 20.1.1.0 0.0.0.255
#
vlan 20
#
l2vpn enable
#
vsi vpna
vxlan 10
tunnel 1
tunnel 2
#
vsi vpnb
vxlan 20
tunnel 1
tunnel 2
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
interface Vlan-interface20
ip address 20.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
service-instance 1000
encapsulation s-vid 10
xconnect vsi vpna
service-instance 2000
encapsulation s-vid 11
xconnect vsi vpnb
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 20
#
interface Tunnel1 mode vxlan
source 1.1.1.1
destination 2.2.2.2
#
interface Tunnel2 mode vxlan
source 1.1.1.1
destination 3.3.3.3
· Switch B
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 2.2.2.2 0.0.0.0
network 30.1.1.0 0.0.0.255
#
vlan 30
#
l2vpn enable
#
vsi vpna
vxlan 10
tunnel 1
tunnel 2
#
vsi vpnb
vxlan 20
tunnel 1
tunnel 2
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
#
interface Vlan-interface30
ip address 30.1.1.2 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
service-instance 1000
encapsulation s-vid 12
xconnect vsi vpna
service-instance 2000
encapsulation s-vid 13
xconnect vsi vpnb
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
interface Tunnel1 mode vxlan
source 2.2.2.2
destination 1.1.1.1
#
interface Tunnel2 mode vxlan
source 2.2.2.2
destination 3.3.3.3
· Switch C
#
ospf 1 router-id 3.3.3.3
area 0.0.0.0
network 3.3.3.3 0.0.0.0
network 40.1.1.0 0.0.0.255
#
ospf 2 router-id 3.3.3.3
area 0.0.0.0
network 10.1.1.0 0.0.0.255
network 10.1.2.0 0.0.0.255
network 100.1.1.0 0.0.0.255
#
hardware-resource vxlan l3gw8k
#
vlan 40
#
vlan 100
#
l2vpn enable
#
vsi vpna
gateway vsi-interface 1
vxlan 10
tunnel 1
tunnel 2
#
vsi vpnb
gateway vsi-interface 2
vxlan 20
tunnel 1
tunnel 2
#
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
interface Vlan-interface40
ip address 40.1.1.3 255.255.255.0
#
interface Vlan-interface100
ip address 100.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 40
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 100
#
interface Vsi-interface1
ip address 10.1.1.1 255.255.255.0
#
interface Vsi-interface2
ip address 10.1.2.1 255.255.255.0
#
interface Tunnel1 mode vxlan
source 3.3.3.3
destination 1.1.1.1
#
interface Tunnel2 mode vxlan
source 3.3.3.3
destination 2.2.2.2
#
return
· Switch D
#
ospf 1 router-id 4.4.4.4
area 0.0.0.0
network 4.4.4.4 0.0.0.0
network 20.1.1.0 0.0.0.255
network 30.1.1.0 0.0.0.255
network 40.1.1.0 0.0.0.255
#
vlan 20
#
vlan 30
#
vlan 40
#
interface LoopBack0
ip address 4.4.4.4 255.255.255.255
#
interface Vlan-interface20
ip address 20.1.1.4 255.255.255.0
#
interface Vlan-interface30
ip address 30.1.1.4 255.255.255.0
#
interface Vlan-interface40
ip address 40.1.1.4 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 20
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 40
#
return
Switch A、Switch B为与服务器连接的VTEP设备,Switch C和Switch D为与广域网连接的集中式VXLAN IP网关设备。虚拟机VM 1、VM 3属于VXLAN 10,虚拟机VM 2、VM 4属于VXLAN 20。通过VXLAN IP网关保护组实现Switch C和Switch D能够同时对虚拟机的跨网络报文进行三层转发,同时实现网关设备的备份。
图3 集中式VXLAN IP网关保护组配置组网图
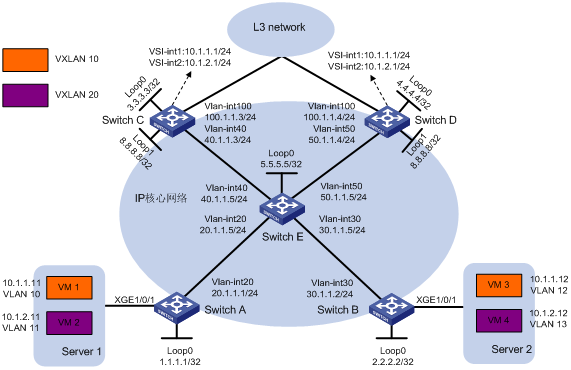
· 在IP核心网络上配置路由协议,使得各交换机的接口IP地址(包括Loopback接口IP地址)之间路由可达。本举例以OSPF路由协议为例。
· 在Switch A、Switch B、Switch C和Switch D之间建立VXLAN隧道,并将VXLAN隧道与VXLAN关联,以便将虚拟机发送的二层报文封装为IP报文后在IP核心网络上转发。
· 在Switch A和Switch B的下行端口上配置以太网服务实例和相应的匹配规则,用来识别用户网络中的报文所属的VXLAN。
· 在集中式VXLAN IP网关Switch C和Switch D上为每个VXLAN分别创建一个VSI虚接口,并为其配置IP地址,该地址作为各自VXLAN内虚拟机的网关地址;在Switch C和Switch D上配置路由协议将VSI虚接口、Vlan-interface100所在网段路由发布到L3 network,以便L3 network内的节点具有到达虚拟机的路由,本举例以OSPF路由协议为例。
· 将Switch C和Switch D加入集中式VXLAN IP网关保护组,实现网关设备的备份。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
· 集中式VXLAN IP网关保护组的所有成员设备上必须创建相同的VSI虚接口,并为该接口配置相同的IP地址和MAC地址。
· VSI虚接口上配置的MAC地址只用于应答ARP请求。网关对报文进行三层转发时,报文的源MAC地址替换为设备的桥MAC地址,而不是VSI虚接口上配置的MAC地址。因此,为了避免虚拟机上的ARP表项超时老化,需要配置VSI虚接口定时发送免费ARP报文。
· 保护组中的每台成员设备上都要执行vtep group group-ip member local member-ip命令。member-ip为当前设备的成员地址,该地址必须是设备上已经存在的IP地址,并且需要通过路由协议发布到IP网络。
· 保护组中的每台成员设备上都要执行vtep group group-ip member remote member-ip&<1-8>命令,且执行该命令时必须输入保护组中所有其它成员设备的成员地址。
· 同一个保护组中不同成员设备的成员地址不能相同。
# 配置Switch A的接口IP地址。
<SwitchA> system-view
[SwitchA] vlan 20
[SwitchA-vlan20] port ten-gigabitethernet 1/0/2
[SwitchA-vlan20] quit
[SwitchA] interface vlan-interface 20
[SwitchA-Vlan-interface20] ip address 20.1.1.1 24
[SwitchA-Vlan-interface20] quit
[SwitchA] interface loopback 0
[SwitchA-LoopBack0] ip address 1.1.1.1 32
# 请参考以上方法配置其它设备上的接口IP地址,配置步骤这里省略。
# 在Switch A上配置OSPF发布接口所在网段的路由。
[SwitchA] ospf 1 router-id 1.1.1.1
[SwitchA-ospf-1] area 0
[SwitchA-ospf-1-area-0.0.0.0] network 1.1.1.1 0.0.0.0
[SwitchA-ospf-1-area-0.0.0.0] network 20.1.1.0 0.0.0.255
[SwitchA-ospf-1-area-0.0.0.0] quit
[SwitchA-ospf-1] quit
# 在Switch B上配置OSPF发布接口所在网段的路由。
[SwitchB] ospf 1 router-id 2.2.2.2
[SwitchB-ospf-1] area 0
[SwitchB-ospf-1-area-0.0.0.0] network 2.2.2.2 0.0.0.0
[SwitchB-ospf-1-area-0.0.0.0] network 30.1.1.0 0.0.0.255
[SwitchB-ospf-1-area-0.0.0.0] quit
[SwitchB-ospf-1] quit
# 在Switch C上配置OSPF发布接口所在网段的路由。
[SwitchC] ospf 1 router-id 3.3.3.3
[SwitchC-ospf-1] area 0
[SwitchC-ospf-1-area-0.0.0.0] network 3.3.3.3 0.0.0.0
[SwitchC-ospf-1-area-0.0.0.0] network 8.8.8.8 0.0.0.0
[SwitchC-ospf-1-area-0.0.0.0] network 40.1.1.0 0.0.0.255
[SwitchC-ospf-1-area-0.0.0.0] quit
[SwitchC-ospf-1] quit
# 在Switch D上配置OSPF发布接口所在网段的路由。
[SwitchD] ospf 1 router-id 4.4.4.4
[SwitchD-ospf-1] area 0
[SwitchD-ospf-1-area-0.0.0.0] network 4.4.4.4 0.0.0.0
[SwitchD-ospf-1-area-0.0.0.0] network 8.8.8.8 0.0.0.0
[SwitchD-ospf-1-area-0.0.0.0] network 50.1.1.0 0.0.0.255
[SwitchD-ospf-1-area-0.0.0.0] quit
[SwitchD-ospf-1] quit
# 在Switch E上配置OSPF发布接口所在网段的路由。
[SwitchE] ospf 1 router-id 5.5.5.5
[SwitchE-ospf-1] area 0
[SwitchE-ospf-1-area-0.0.0.0] network 5.5.5.5 0.0.0.0
[SwitchE-ospf-1-area-0.0.0.0] network 20.1.1.0 0.0.0.255
[SwitchE-ospf-1-area-0.0.0.0] network 30.1.1.0 0.0.0.255
[SwitchE-ospf-1-area-0.0.0.0] network 40.1.1.0 0.0.0.255
[SwitchE-ospf-1-area-0.0.0.0] network 50.1.1.0 0.0.0.255
[SwitchE-ospf-1-area-0.0.0.0] quit
[SwitchE-ospf-1] quit
# 开启L2VPN功能。
[SwitchA] l2vpn enable
# 创建VXLAN 10和VXLAN 20。
[SwitchA] l2vpn enable
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan10] quit
[SwitchA-vsi-vpna] quit
[SwitchA] vsi vpnb
[SwitchA-vsi-vpnb] vxlan 20
[SwitchA-vsi-vpnb-vxlan10] quit
[SwitchA-vsi-vpnb] quit
# 开启L2VPN功能。
[SwitchB] l2vpn enable
# 创建VXLAN 10和VXLAN 20。
[SwitchB] l2vpn enable
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan10] quit
[SwitchB-vsi-vpna] quit
[SwitchB] vsi vpnb
[SwitchB-vsi-vpnb] vxlan 20
[SwitchB-vsi-vpnb-vxlan10] quit
[SwitchB-vsi-vpnb] quit
# 开启L2VPN功能。
[SwitchC] l2vpn enable
# 配置VXLAN的硬件资源模式(该配置需要保存并重启设备才能生效,重启设备的具体配置步骤这里省略)。
[SwitchC] hardware-resource vxlan l3gw8k
# 创建VXLAN 10和VXLAN 20。
[SwitchC] l2vpn enable
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] vxlan 10
[SwitchC-vsi-vpna-vxlan10] quit
[SwitchC-vsi-vpna] quit
[SwitchC] vsi vpnb
[SwitchC-vsi-vpnb] vxlan 20
[SwitchC-vsi-vpnb-vxlan10] quit
[SwitchC-vsi-vpnb] quit
# 开启L2VPN功能。
[SwitchD] l2vpn enable
# 配置VXLAN的硬件资源模式(该配置需要保存并重启设备才能生效,重启设备的具体配置步骤这里省略)。
[SwitchD] hardware-resource vxlan l3gw8k
# 创建VXLAN 10和VXLAN 20。
[SwitchD] l2vpn enable
[SwitchD] vsi vpna
[SwitchD-vsi-vpna] vxlan 10
[SwitchD-vsi-vpna-vxlan10] quit
[SwitchD-vsi-vpna] quit
[SwitchD] vsi vpnb
[SwitchD-vsi-vpnb] vxlan 20
[SwitchD-vsi-vpnb-vxlan10] quit
[SwitchD-vsi-vpnb] quit
# 在Switch A和VXLAN IP保护组之间建立VXLAN隧道Tunnel1,隧道的目的端地址为保护组的VTEP IP(8.8.8.8)。
[SwitchA] interface tunnel 1 mode vxlan
[SwitchA-Tunnel1] source 1.1.1.1
[SwitchA-Tunnel1] destination 8.8.8.8
[SwitchA-Tunnel1] quit
# 创建到达Switch B的VXLAN隧道Tunnel2。
[SwitchA] interface tunnel 2 mode vxlan
[SwitchA-Tunnel2] source 1.1.1.1
[SwitchA-Tunnel2] destination 2.2.2.2
[SwitchA-Tunnel2] quit
# 在Switch B和VXLAN IP保护组之间建立VXLAN隧道Tunnel1,隧道的目的端地址为保护组的VTEP IP(8.8.8.8)。
[SwitchB] interface tunnel 1 mode vxlan
[SwitchB-Tunnel1] source 2.2.2.2
[SwitchB-Tunnel1] destination 8.8.8.8
[SwitchB-Tunnel1] quit
# 创建到达Switch A的VXLAN隧道Tunnel2。
[SwitchB] interface tunnel 2 mode vxlan
[SwitchB-Tunnel2] source 2.2.2.2
[SwitchB-Tunnel2] destination 1.1.1.1
[SwitchB-Tunnel2] quit
# 创建VXLAN IP保护组到达Switch A和Switch B的VXLAN隧道Tunnel1和Tunnel2,隧道的源端地址为保护组的VTEP IP(8.8.8.8)。
[SwitchC] interface tunnel 1 mode vxlan
[SwitchC-Tunnel1] source 8.8.8.8
[SwitchC-Tunnel1] destination 1.1.1.1
[SwitchC-Tunnel1] quit
[SwitchC] interface tunnel 2 mode vxlan
[SwitchC-Tunnel2] source 8.8.8.8
[SwitchC-Tunnel2] destination 2.2.2.2
[SwitchC-Tunnel2] quit
# 创建VXLAN IP保护组到达Switch A和Switch B的VXLAN隧道Tunnel1和Tunnel2,隧道的源端地址为保护组的VTEP IP(8.8.8.8)。
[SwitchD] interface tunnel 1 mode vxlan
[SwitchD-Tunnel1] source 8.8.8.8
[SwitchD-Tunnel1] destination 1.1.1.1
[SwitchD-Tunnel1] quit
[SwitchD] interface tunnel 2 mode vxlan
[SwitchD-Tunnel2] source 8.8.8.8
[SwitchD-Tunnel2] destination 2.2.2.2
[SwitchD-Tunnel2] quit
# 在Switch A上将VXLAN隧道Tunnel1和Tunnel2均与VXLAN 10、VXLAN 20关联。
[SwitchA] vsi vpna
[SwitchA-vsi-vpna] vxlan 10
[SwitchA-vsi-vpna-vxlan10] tunnel 1
[SwitchA-vsi-vpna-vxlan10] tunnel 2
[SwitchA-vsi-vpna-vxlan10] quit
[SwitchA-vsi-vpna] quit
[SwitchA] vsi vpnb
[SwitchA-vsi-vpnb] vxlan 20
[SwitchA-vsi-vpnb-vxlan20] tunnel 1
[SwitchA-vsi-vpnb-vxlan20] tunnel 2
[SwitchA-vsi-vpnb-vxlan20] quit
[SwitchA-vsi-vpnb] quit
# 在Switch B上将VXLAN隧道Tunnel1和Tunnel2均与VXLAN 10、VXLAN 20关联。
[SwitchB] vsi vpna
[SwitchB-vsi-vpna] vxlan 10
[SwitchB-vsi-vpna-vxlan10] tunnel 1
[SwitchB-vsi-vpna-vxlan10] tunnel 2
[SwitchB-vsi-vpna-vxlan10] quit
[SwitchB-vsi-vpna] quit
[SwitchB] vsi vpnb
[SwitchB-vsi-vpnb] vxlan 20
[SwitchB-vsi-vpnb-vxlan20] tunnel 1
[SwitchB-vsi-vpnb-vxlan20] tunnel 2
[SwitchB-vsi-vpnb-vxlan20] quit
[SwitchB-vsi-vpnb] quit
# 在Switch C上将VXLAN隧道Tunnel1和Tunnel2均与VXLAN 10、VXLAN 20关联。
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] vxlan 10
[SwitchC-vsi-vpna-vxlan10] tunnel 1
[SwitchC-vsi-vpna-vxlan10] tunnel 2
[SwitchC-vsi-vpna-vxlan10] quit
[SwitchC-vsi-vpna] quit
[SwitchC] vsi vpnb
[SwitchC-vsi-vpnb] vxlan 20
[SwitchC-vsi-vpnb-vxlan20] tunnel 1
[SwitchC-vsi-vpnb-vxlan20] tunnel 2
[SwitchC-vsi-vpnb-vxlan20] quit
[SwitchC-vsi-vpnb] quit
# 在Switch D上将VXLAN隧道Tunnel1和Tunnel2均与VXLAN 10、VXLAN 20关联。
[SwitchD] vsi vpna
[SwitchD-vsi-vpna] vxlan 10
[SwitchD-vsi-vpna-vxlan10] tunnel 1
[SwitchD-vsi-vpna-vxlan10] tunnel 2
[SwitchD-vsi-vpna-vxlan10] quit
[SwitchD-vsi-vpna] quit
[SwitchD] vsi vpnb
[SwitchD-vsi-vpnb] vxlan 20
[SwitchD-vsi-vpnb-vxlan20] tunnel 1
[SwitchD-vsi-vpnb-vxlan20] tunnel 2
[SwitchD-vsi-vpnb-vxlan20] quit
[SwitchD-vsi-vpnb] quit
# 在接口Ten-GigabitEthernet1/0/1上创建以太网服务实例1000,该实例用来匹配VLAN 10(VM 1)的数据帧,将该服务实例与vpna(VXLAN 10)关联。
[SwitchA] interface ten-gigabitethernet 1/0/1
[SwitchA-Ten-GigabitEthernet1/0/1] service-instance 1000
[SwitchA-Ten-GigabitEthernet1/0/1-srv1000] encapsulation s-vid 10
[SwitchA-Ten-GigabitEthernet1/0/1-srv1000] xconnect vsi vpna
[SwitchA-Ten-GigabitEthernet1/0/1-srv1000] quit
# 在接口Ten-GigabitEthernet1/0/1上创建以太网服务实例2000,该实例用来匹配VLAN 11(VM 2)的数据帧,将该服务实例与vpnb(VXLAN 20)关联。
[SwitchA-Ten-GigabitEthernet1/0/1] service-instance 2000
[SwitchA-Ten-GigabitEthernet1/0/1-srv2000] encapsulation s-vid 11
[SwitchA-Ten-GigabitEthernet1/0/1-srv2000] xconnect vsi vpnb
[SwitchA-Ten-GigabitEthernet1/0/1-srv2000] quit
[SwitchA-Ten-GigabitEthernet1/0/1] quit
# 在接口Ten-GigabitEthernet1/0/1上创建以太网服务实例1000,该实例用来匹配VLAN 12(VM 3)的数据帧,将该服务实例与vpna(VXLAN 10)关联。
[SwitchB] interface ten-gigabitethernet 1/0/1
[SwitchB-Ten-GigabitEthernet1/0/1] service-instance 1000
[SwitchB-Ten-GigabitEthernet1/0/1-srv1000] encapsulation s-vid 12
[SwitchB-Ten-GigabitEthernet1/0/1-srv1000] xconnect vsi vpna
[SwitchB-Ten-GigabitEthernet1/0/1-srv1000] quit
# 在接口Ten-GigabitEthernet1/0/1上创建以太网服务实例2000,该实例用来匹配VLAN 13(VM 4)的数据帧,将该服务实例与vpnb(VXLAN 20)关联。
[SwitchB-Ten-GigabitEthernet1/0/1] service-instance 2000
[SwitchB-Ten-GigabitEthernet1/0/1-srv2000] encapsulation s-vid 13
[SwitchB-Ten-GigabitEthernet1/0/1-srv2000] xconnect vsi vpnb
[SwitchB-Ten-GigabitEthernet1/0/1-srv2000] quit
[SwitchB-Ten-GigabitEthernet1/0/1] quit
# 创建VSI虚接口VSI-interface1,为其配置IP地址,该IP地址作为VXLAN 10内虚拟机的网关地址,指定该接口的MAC地址,并配置该接口定时发送免费ARP报文。
[SwitchC] interface vsi-interface 1
[SwitchC-Vsi-interface1] ip address 10.1.1.1 255.255.255.0
[SwitchC-Vsi-interface1] mac-address 1-1-1
[SwitchC-Vsi-interface1] arp send-gratuitous-arp interval 200000
[SwitchC-Vsi-interface1] quit
# 配置VXLAN 10所在的VSI实例与接口VSI-interface1关联。
[SwitchC] vsi vpna
[SwitchC-vsi-vpna] gateway vsi-interface 1
[SwitchC-vsi-vpna] quit
# 创建VSI虚接口VSI-interface2,为其配置IP地址,该IP地址作为VXLAN 20内虚拟机的网关地址,指定该接口的MAC地址,并配置该接口定时发送免费ARP报文。
[SwitchC] interface vsi-interface 2
[SwitchC-Vsi-interface2] ip address 10.1.2.1 255.255.255.0
[SwitchC-Vsi-interface2] mac-address 2-2-2
[SwitchC-Vsi-interface2] arp send-gratuitous-arp interval 200000
[SwitchC-Vsi-interface2] quit
# 配置VXLAN 20所在的VSI实例与接口VSI-interface2关联。
[SwitchC] vsi vpnb
[SwitchC-vsi-vpnb] gateway vsi-interface 2
[SwitchC-vsi-vpnb] quit
# 配置OSPF发布VSI虚接口、Vlan-interface100接口所在网段的路由。(与SwitchC相连的公网设备上也需要配置OSPF,发布自己的网段路由)
[SwitchC] ospf 2 router-id 3.3.3.3
[SwitchC-ospf-2] area 0
[SwitchC-ospf-2-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[SwitchC-ospf-2-area-0.0.0.0] network 10.1.2.0 0.0.0.255
[SwitchC-ospf-2-area-0.0.0.0] network 100.1.1.0 0.0.0.255
[SwitchC-ospf-2-area-0.0.0.0] quit
[SwitchC-ospf-2] quit
# 创建VSI虚接口VSI-interface1,为其配置IP地址,该IP地址作为VXLAN 10内虚拟机的网关地址,指定该接口的MAC地址,并配置该接口定时发送免费ARP报文。
[SwitchD] interface vsi-interface 1
[SwitchD-Vsi-interface1] ip address 10.1.1.1 255.255.255.0
[SwitchD-Vsi-interface1] mac-address 1-1-1
[SwitchD-Vsi-interface1] arp send-gratuitous-arp interval 200000
[SwitchD-Vsi-interface1] quit
# 配置VXLAN 10所在的VSI实例与接口VSI-interface1关联。
[SwitchD] vsi vpna
[SwitchD-vsi-vpna] gateway vsi-interface 1
[SwitchD-vsi-vpna] quit
# 创建VSI虚接口VSI-interface2,为其配置IP地址,该IP地址作为VXLAN 20内虚拟机的网关地址,指定该接口的MAC地址,并配置该接口定时发送免费ARP报文。
[SwitchD] interface vsi-interface 2
[SwitchD-Vsi-interface2] ip address 10.1.2.1 255.255.255.0
[SwitchD-Vsi-interface2] mac-address 2-2-2
[SwitchD-Vsi-interface2] arp send-gratuitous-arp interval 200000
[SwitchD-Vsi-interface2] quit
# 配置VXLAN 20所在的VSI实例与接口VSI-interface2关联。
[SwitchD] vsi vpnb
[SwitchD-vsi-vpnb] gateway vsi-interface 2
[SwitchD-vsi-vpnb] quit
# 配置OSPF发布VSI虚接口、Vlan-interface100接口所在网段的路由。(与SwitchD相连的公网设备上也需要配置OSPF,发布自己的网段路由)
[SwitchD] ospf 2 router-id 4.4.4.4
[SwitchD-ospf-2] area 0
[SwitchD-ospf-2-area-0.0.0.0] network 10.1.1.0 0.0.0.255
[SwitchD-ospf-2-area-0.0.0.0] network 10.1.2.0 0.0.0.255
[SwitchD-ospf-2-area-0.0.0.0] network 100.1.1.0 0.0.0.255
[SwitchD-ospf-2-area-0.0.0.0] quit
[SwitchD-ospf-2] quit
# 指定VXLAN IP网关保护组及其成员。
[SwitchA] vtep group 8.8.8.8 member remote 3.3.3.3 4.4.4.4
# 指定VXLAN IP网关保护组及其成员。
[SwitchB] vtep group 8.8.8.8 member remote 3.3.3.3 4.4.4.4
# 配置VXLAN IP网关保护组,并配置本地成员地址。
[SwitchC] vtep group 8.8.8.8 member local 3.3.3.3
# 配置VXLAN IP网关保护组的其它成员地址。
[SwitchC] vtep group 8.8.8.8 member remote 4.4.4.4
# 配置VXLAN IP网关保护组,并配置本地成员地址。
[SwitchD] vtep group 8.8.8.8 member local 4.4.4.4
# 配置VXLAN IP网关保护组的其它成员地址。
[SwitchD] vtep group 8.8.8.8 member remote 3.3.3.3
# 以Switch A为例,在VTEP上查看Tunnel接口信息,可以看到VXLAN模式的Tunnel接口处于up状态。其中,Tunnel1和Tunnel2为手工创建的VXLAN隧道,Tunne3和Tunnel4为VTEP与VXLAN IP网关保护组成员设备之间自动建立的VXLAN隧道。
[SwitchA] display interface tunnel
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 1.1.1.1, destination 8.8.8.8
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
Tunnel2
Current state: UP
Line protocol state: UP
Description: Tunnel2 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 1.1.1.1, destination 2.2.2.2
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
Tunnel3
Current state: UP
Line protocol state: UP
Description: Tunnel3 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 1.1.1.1, destination 3.3.3.3
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
Tunnel4
Current state: UP
Line protocol state: UP
Description: Tunnel4 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 1.1.1.1, destination 4.4.4.4
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# 以Switch C为例,在集中式VXLAN IP网关上查看Tunnel接口信息,可以看到VXLAN模式的Tunnel接口处于up状态。
[SwitchC] display interface tunnel
Tunnel1
Current state: UP
Line protocol state: UP
Description: Tunnel1 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 8.8.8.8, destination 1.1.1.1
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
Tunnel2
Current state: UP
Line protocol state: UP
Description: Tunnel2 Interface
Bandwidth: 64 kbps
Maximum transmission unit: 1464
Internet protocol processing: Disabled
Last clearing of counters: Never
Tunnel source 8.8.8.8, destination 2.2.2.2
Tunnel protocol/transport UDP_VXLAN/IP
Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec
Input: 0 packets, 0 bytes, 0 drops
Output: 0 packets, 0 bytes, 0 drops
# 以Switch C为例,在集中式VXLAN IP网关上查看VSI虚接口信息,可以看到VSI虚接口处于up状态。
[SwitchC] display interface vsi-interface
Vsi-interface1
Current state: UP
Line protocol state: UP
Description: Vsi-interface1 Interface
Bandwidth: 1000000 kbps
Maximum transmission unit: 1444
Internet Address: 10.1.1.1/24 (primary)
IP packet frame type: Ethernet II, hardware address: 0001-0001-0001
IPv6 packet frame type: Ethernet II, hardware address: 0001-0001-0001
Physical: Unknown, baudrate: 1000000 kbps
Last clearing of counters: Never
Input (total): 0 packets, 0 bytes
Output (total): 0 packets, 0 bytes
Vsi-interface2
Current state: UP
Line protocol state: UP
Description: Vsi-interface2 Interface
Bandwidth: 1000000 kbps
Maximum transmission unit: 1444
Internet Address: 10.1.2.1/24 (primary)
IP packet frame type: Ethernet II, hardware address: 0002-0002-0002
IPv6 packet frame type: Ethernet II, hardware address: 0002-0002-0002
Physical: Unknown, baudrate: 1000000 kbps
Last clearing of counters: Never
Input (total): 0 packets, 0 bytes
Output (total): 0 packets, 0 bytes
# 以Switch A为例,在VTEP上查看VSI信息,可以看到VSI内创建的VXLAN、与VXLAN关联的VXLAN隧道、与VSI关联的以太网服务实例等信息。
[SwitchA] display l2vpn vsi verbose
VSI Name: vpna
VSI Index : 0
VSI State : Up
MTU : 1500
Bandwidth : Unlimited
Broadcast Restrain : Unlimited
Multicast Restrain : Unlimited
Unknown Unicast Restrain: Unlimited
MAC Learning : Enabled
MAC Table Limit : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
VXLAN ID : 10
Tunnels:
Tunnel Name Link ID State Type Flood proxy
Tunnel1 0x5000001 Up Manual Disabled
Tunnel2 0x5000002 Up Manual Disabled
Tunnel3 0x5000003 Up Auto Disabled
Tunnel4 0x5000004 Up Auto Disabled
ACs:
AC Link ID State Type
XGE1/0/1 srv1000 0 Up Manual
VSI Name: vpnb
VSI Index : 1
VSI State : Up
MTU : 1500
Bandwidth : Unlimited
Broadcast Restrain : Unlimited
Multicast Restrain : Unlimited
Unknown Unicast Restrain: Unlimited
MAC Learning : Enabled
MAC Table Limit : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
VXLAN ID : 20
Tunnels:
Tunnel Name Link ID State Type Flood proxy
Tunnel1 0x5000001 Up Manual Disabled
Tunnel2 0x5000002 Up Manual Disabled
Tunnel3 0x5000003 Up Auto Disabled
Tunnel4 0x5000004 Up Auto Disabled
ACs:
AC Link ID State Type
XGE1/0/1 srv2000 0 Up Manual
# 以Switch C为例,在集中式VXLAN IP网关上查看VSI信息,可以看到VSI内创建的VXLAN、与VXLAN关联的VXLAN隧道、与VSI关联的VSI虚接口等信息。
[SwitchC] display l2vpn vsi verbose
VSI Name: vpna
VSI Index : 0
VSI State : Up
MTU : 1500
Bandwidth : Unlimited
Broadcast Restrain : Unlimited
Multicast Restrain : Unlimited
Unknown Unicast Restrain: Unlimited
MAC Learning : Enabled
MAC Table Limit : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
Gateway interface : VSI-interface 1
VXLAN ID : 10
Tunnels:
Tunnel Name Link ID State Type Flooding proxy
Tunnel1 0x5000002 Up Manual Disabled
Tunnel2 0x5000003 Up Manual Disabled
VSI Name: vpnb
VSI Index : 1
VSI State : Up
MTU : 1500
Bandwidth : Unlimited
Broadcast Restrain : Unlimited
Multicast Restrain : Unlimited
Unknown Unicast Restrain: Unlimited
MAC Learning : Enabled
MAC Table Limit : -
Drop Unknown : -
Flooding : Enabled
Statistics : Disabled
Gateway interface : VSI-interface 2
VXLAN ID : 20
Tunnels:
Tunnel Name Link ID State Type Flooding proxy
Tunnel1 0x5000002 Up Manual Disabled
Tunnel2 0x5000003 Up Manual Disabled
# 虚拟机VM 1、VM 2、VM3、VM4之间均可以互访,且可以ping通100.1.1.0/24网段内的地址。
# 在Switch C上查看VSI的ARP表项信息,可以看到已学习到了虚拟机的ARP信息。
[SwitchC] display arp
Type: S-Static D-Dynamic O-Openflow R-Rule M-Multiport I-Invalid
IP address MAC address VLAN/VSI Interface/Link ID Aging Type
10.1.1.11 0000-1234-0001 N/A Tunnel1 20 D
10.1.1.12 0000-1234-0002 N/A Tunnel2 19 D
# 在Switch C上查看FIB表项信息,可以看到已学习到了虚拟机的转发表项信息。
[SwitchC] display fib 10.1.1.11
Destination count: 1 FIB entry count: 1
Flag:
U:Useable G:Gateway H:Host B:Blackhole D:Dynamic S:Static
R:Relay F:FRR
Destination/Mask Nexthop Flag OutInterface/Token Label
10.1.1.11/32 10.1.1.11 UH Vsi1 Null
# 在Switch D上查看VSI的ARP表项信息和FIB表项信息,可以看到该信息与Switch C上的信息一致。
[SwitchD] display arp
Type: S-Static D-Dynamic O-Openflow R-Rule M-Multiport I-Invalid
IP address MAC address VLAN/VSI Interface/Link ID Aging Type
10.1.1.11 0000-1234-0001 N/A Tunnel1 20 D
10.1.1.12 0000-1234-0002 N/A Tunnel2 19 D
[SwitchD] display fib 10.1.1.11
Destination count: 1 FIB entry count: 1
Flag:
U:Useable G:Gateway H:Host B:Blackhole D:Dynamic S:Static
R:Relay F:FRR
Destination/Mask Nexthop Flag OutInterface/Token Label
10.1.1.11/32 10.1.1.11 UH Vsi1 Null
· Switch A
#
ospf 1 router-id 1.1.1.1
area 0.0.0.0
network 1.1.1.1 0.0.0.0
network 20.1.1.0 0.0.0.255
#
vlan 20
#
l2vpn enable
#
vsi vpna
vxlan 10
tunnel 1
tunnel 2
#
vsi vpnb
vxlan 20
tunnel 1
tunnel 2
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
interface Vlan-interface20
ip address 20.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
service-instance 1000
encapsulation s-vid 10
xconnect vsi vpna
service-instance 2000
encapsulation s-vid 11
xconnect vsi vpnb
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 20
#
interface Tunnel1 mode vxlan
source 1.1.1.1
destination 8.8.8.8
#
interface Tunnel2 mode vxlan
source 1.1.1.1
destination 2.2.2.2
#
vtep group 8.8.8.8 member remote 3.3.3.3 4.4.4.4
#
· Switch B
#
ospf 1 router-id 2.2.2.2
area 0.0.0.0
network 2.2.2.2 0.0.0.0
network 30.1.1.0 0.0.0.255
#
vlan 30
#
l2vpn enable
#
vsi vpna
vxlan 10
tunnel 1
tunnel 2
#
vsi vpnb
vxlan 20
tunnel 1
tunnel 2
#
interface LoopBack0
ip address 2.2.2.2 255.255.255.255
#
interface Vlan-interface30
ip address 30.1.1.2 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
service-instance 1000
encapsulation s-vid 12
xconnect vsi vpna
service-instance 2000
encapsulation s-vid 13
xconnect vsi vpnb
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
interface Tunnel1 mode vxlan
source 2.2.2.2
destination 8.8.8.8
#
interface Tunnel2 mode vxlan
source 2.2.2.2
destination 1.1.1.1
#
vtep group 8.8.8.8 member remote 3.3.3.3 4.4.4.4
#
· Switch C
#
ospf 1 router-id 3.3.3.3
area 0.0.0.0
network 3.3.3.3 0.0.0.0
network 8.8.8.8 0.0.0.0
network 40.1.1.0 0.0.0.255
#
ospf 2 router-id 3.3.3.3
area 0.0.0.0
network 10.1.1.0 0.0.0.255
network 10.1.2.0 0.0.0.255
network 100.1.1.0 0.0.0.255
#
hardware-resource vxlan l3gw8k
#
vlan 40
#
vlan 100
#
l2vpn enable
#
vsi vpna
gateway vsi-interface 1
vxlan 10
tunnel 1
tunnel 2
#
vsi vpnb
gateway vsi-interface 2
vxlan 20
tunnel 1
tunnel 2
#
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
interface LoopBack1
ip address 8.8.8.8 255.255.255.255
#
interface Vlan-interface40
ip address 40.1.1.3 255.255.255.0
#
interface Vlan-interface100
ip address 100.1.1.3 255.255.255.0
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 40
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 100
#
interface Vsi-interface1
ip address 10.1.1.1 255.255.255.0
mac-address 0001-0001-0001
arp send-gratuitous-arp interval 200000
#
interface Vsi-interface2
ip address 10.1.2.1 255.255.255.0
mac-address 0002-0002-0002
arp send-gratuitous-arp interval 200000
#
interface Tunnel1 mode vxlan
source 8.8.8.8
destination 1.1.1.1
#
interface Tunnel2 mode vxlan
source 8.8.8.8
destination 2.2.2.2
#
vtep group 8.8.8.8 member local 3.3.3.3
#
vtep group 8.8.8.8 member remote 4.4.4.4
#
return
· Switch D
#
ospf 1 router-id 4.4.4.4
area 0.0.0.0
network 4.4.4.4 0.0.0.0
network 8.8.8.8 0.0.0.0
network 50.1.1.0 0.0.0.255
#
ospf 2 router-id 4.4.4.4
area 0.0.0.0
network 10.1.1.0 0.0.0.255
network 10.1.2.0 0.0.0.255
network 100.1.1.0 0.0.0.255
#
hardware-resource vxlan l3gw8k
#
vlan 50
#
vlan 100
#
l2vpn enable
#
vsi vpna
gateway vsi-interface 1
vxlan 10
tunnel 1
tunnel 2
#
vsi vpnb
gateway vsi-interface 2
vxlan 20
tunnel 1
tunnel 2
#
interface LoopBack0
ip address 4.4.4.4 255.255.255.255
#
interface LoopBack1
ip address 8.8.8.8 255.255.255.255
#
interface Vlan-interface50
ip address 50.1.1.4 255.255.255.0
#
interface Vlan-interface100
ip address 100.1.1.4 255.255.255.0
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 50
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 100
#
interface Vsi-interface1
ip address 10.1.1.1 255.255.255.0
mac-address 0001-0001-0001
arp send-gratuitous-arp interval 200000
#
interface Vsi-interface2
ip address 10.1.2.1 255.255.255.0
mac-address 0002-0002-0002
arp send-gratuitous-arp interval 200000
#
interface Tunnel1 mode vxlan
source 8.8.8.8
destination 1.1.1.1
#
interface Tunnel2 mode vxlan
source 8.8.8.8
destination 2.2.2.2
#
vtep group 8.8.8.8 member local 4.4.4.4
#
vtep group 8.8.8.8 member remote 3.3.3.3
#
return
· Switch E
#
ospf 1 router-id 5.5.5.5
area 0.0.0.0
network 5.5.5.5 0.0.0.0
network 20.1.1.0 0.0.0.255
network 30.1.1.0 0.0.0.255
network 40.1.1.0 0.0.0.255
network 50.1.1.0 0.0.0.255
#
vlan 20
#
vlan 30
#
vlan 40
#
vlan 50
#
interface LoopBack0
ip address 5.5.5.5 255.255.255.255
#
interface Vlan-interface20
ip address 20.1.1.5 255.255.255.0
#
interface Vlan-interface30
ip address 30.1.1.5 255.255.255.0
#
interface Vlan-interface40
ip address 40.1.1.5 255.255.255.0
#
interface Vlan-interface50
ip address 50.1.1.5 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 20
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 40
#
interface Ten-GigabitEthernet1/0/4
port link-mode bridge
port access vlan 50
#
return
· H3C S6860系列以太网交换机 VXLAN配置指导-Release 26xx系列
· H3C S6860系列以太网交换机 VXLAN命令参考-Release 26xx系列
不同款型规格的资料略有差异, 详细信息请向具体销售和400咨询。H3C保留在没有任何通知或提示的情况下对资料内容进行修改的权利!
