10-添加或修改报文的VLAN Tag典型配置举例
本章节下载: 10-添加或修改报文的VLAN Tag典型配置举例 (765.21 KB)
H3C S6860产品添加或修改报文的VLAN Tag配置举例
Copyright © 2018 新华三技术有限公司 版权所有,保留一切权利。
非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本文档内容的部分或全部,并不得以任何形式传播。
除新华三技术有限公司的商标外,本手册中出现的其它公司的商标、产品标识及商品名称,由各自权利人拥有。
本文档中的信息可能变动,恕不另行通知。
本文档介绍了使用QinQ功能、VLAN映射功能、QoS功能添加或修改报文的VLAN Tag的配置方式。
由于802.1Q定义的VLAN ID域只有12个比特,最多只能提供4094个VLAN,不能满足运营商网络对VLAN个数的需求。因此,用户网络报文在进入运营商网络时,运营商网络可以为用户网络报文添加一层VLAN Tag,使运营商网络可以利用一个VLAN为用户网络的多个VLAN的报文提供服务。
根据应用需求的不同,添加报文的VLAN Tag可以采用下面方法:
· QinQ:如果运营商网络不需要区分用户网络不同VLAN的报文,可以在运营商网络设备连接用户网络的端口上配置QinQ功能。端口上配置了QinQ功能后,不论从该端口收到的报文是否带有VLAN Tag,设备都会为该报文封装本端口缺省VLAN的Tag。
· 1:2 VLAN映射:如果运营商网络需要区分用户网络不同VLAN的报文,可以在运营商网络设备连接用户网络的端口上配置1:2 VLAN映射功能,使端口可以为用户网络不同VLAN的报文添加不同的外层VLAN Tag。
· QoS策略:如果运营商网络需要使用VLAN ID之外的匹配条件更灵活的匹配用户网络报文,或在为报文添加外层VLAN Tag时,需要同时配置其它流行为,例如重标记报文外层VLAN Tag的优先级,可以通过配置QoS策略实现。
上述添加报文VLAN Tag的方法,在满足需求的情况下,建议依次考虑QinQ、1:2 VLAN映射、QoS策略。例如,需求是为用户网络不同业务类型的VLAN添加不同的外层VLAN Tag,使用1:2 VLAN映射和QoS策略均可以满足需求,建议采用1:2 VLAN映射,如果在为用户网络不同业务类型的VLAN添加不同的外层VLAN Tag的同时还需要重标记报文外层VLAN Tag的优先级,则需要使用QoS策略。
用户网络和运营商网络各自有不同的VLAN划分策略,因此用户网络和运营商网络互联,以及不同运营商网络之间互联时可能需要进行VLAN Tag的修改,从而在不修改原有配置的情况下实现互通。
根据应用需求的不同,修改报文的VLAN Tag可以采用下面方法:
· 1:1 VLAN映射:将来自某一特定VLAN的报文所携带的VLAN Tag替换为新的VLAN Tag。
· N:1 VLAN映射:将来自多个VLAN的报文所携带的不同VLAN Tag替换为相同的VLAN Tag。
· 2:2 VLAN映射:将携带有两层VLAN Tag的报文的内、外层VLAN Tag都替换为新的VLAN Tag。
· QoS策略:通过定义流分类的匹配规则,可以更灵活的匹配用户网络报文;通过使用流行为的remark customer-vlan-id或remark service-vlan-id动作可以为匹配不同流分类的报文修改内层或外层VLAN Tag。
上述修改报文VLAN Tag的方法,在满足需求的情况下,建议优先采用VLAN映射。
![]()
端口配置添加或修改报文的VLAN Tag功能后,设备会将用户网络的MAC地址学习到SVLAN中。
本文档中的配置均是在实验室环境下进行的配置和验证,配置前设备的所有参数均采用出厂时的缺省配置。如果您已经对设备进行了配置,为了保证配置效果,请确认现有配置和以下举例中的配置不冲突。
本文档假设您已了解QinQ特性、VLAN映射特性、QoS Nest特性和QoS重标记特性。
添加或修改报文的VLAN Tag与EVB功能互斥,请勿同时配置。
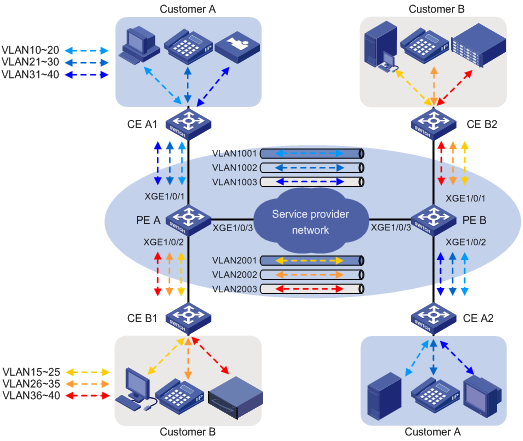
如图1所示,Customer A和Customer B各有两个分支机构需要通过运营商网络进行通信。运营商网络中可用的VLAN资源包括VLAN 1000和VLAN 2000。现要求通过配置QinQ功能,运营商网络能够利用VLAN 1000传输Customer A的数据,利用VLAN 2000传输Customer B的数据。
图1 QinQ组网示意图
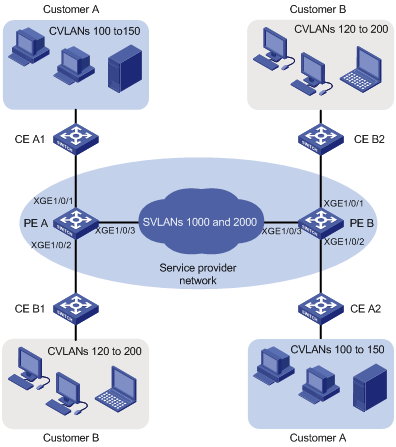
· 请在PE A和PE B连接用户网络的端口上配置QinQ功能。
· 为了保证用户网络接收的数据中不会包含运营商网络的VLAN信息,需要配置开启QinQ功能的端口发送PVID的报文时不带VLAN Tag。开启QinQ功能的端口的链路类型可以是Access,Hybrid或Trunk。如果配置为Hybrid类型,需要配置该端口允许PVID的报文不带VLAN Tag通过。如果配置为Trunk类型,需要配置该端口允许PVID的报文通过。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
· 开启QinQ的端口,需要配置端口的缺省VLAN为QinQ封装的外层VLAN(SVLAN)。
· 需要保证QinQ报文传输路径上,报文的外层VLAN Tag不被修改或移除。
· QinQ为报文加上外层VLAN Tag后,内层VLAN Tag将被当作报文的数据部分进行传输,报文长度将增加4个字节。因此建议用户适当增加QinQ报文传输路径上各接口的MTU值(至少为1504字节)。
# 创建VLAN 1000和VLAN 2000。
<PE_A> system-view
[PE_A] vlan 1000
[PE_A-vlan1000] quit
[PE_A] vlan 2000
[PE_A-vlan2000] quit
# 配置端口Ten-GigabitEthernet 1/0/1为Access端口,允许VLAN 1000的报文通过。
[PE_A] interface ten-gigabitethernet 1/0/1
[PE_A-Ten-GigabitEthernet1/0/1] port access vlan 1000
# 开启端口Ten-GigabitEthernet 1/0/1的QinQ功能。
[PE_A-Ten-GigabitEthernet1/0/1] qinq enable
[PE_A-Ten-GigabitEthernet1/0/1] quit
# 配置端口Ten-GigabitEthernet1/0/2为Access端口,允许VLAN 2000的报文通过。
[PE_A] interface ten-gigabitethernet 1/0/2
[PE_A-Ten-GigabitEthernet1/0/2] port access vlan 2000
# 开启端口Ten-GigabitEthernet1/0/2的QinQ功能。
[PE_A-Ten-GigabitEthernet1/0/2] qinq enable
[PE_A-Ten-GigabitEthernet1/0/2] quit
# 配置端口Ten-GigabitEthernet1/0/3为Trunk端口,且允许VLAN 1000和VLAN 2000的报文通过,取消允许VLAN 1通过。
[PE_A] interface ten-gigabitethernet 1/0/3
[PE_A-Ten-GigabitEthernet1/0/3] port link-type trunk
[PE_A-Ten-GigabitEthernet1/0/3] port trunk permit vlan 1000 2000
[PE_A-Ten-GigabitEthernet1/0/3] undo port trunk permit vlan 1
[PE_A-Ten-GigabitEthernet1/0/3] quit
# 创建VLAN 1000和VLAN 2000。
<PE_B> system-view
[PE_B] vlan 1000
[PE_B-vlan1000] quit
[PE_B] vlan 2000
[PE_B-vlan2000] quit
# 配置端口Ten-GigabitEthernet1/0/1为Access端口,允许VLAN 2000的报文通过。
[PE_B] interface ten-gigabitethernet 1/0/1
[PE_B-Ten-GigabitEthernet1/0/1] port access vlan 2000
# 开启端口Ten-GigabitEthernet1/0/1的QinQ功能。
[PE_B-Ten-GigabitEthernet1/0/1] qinq enable
[PE_B-Ten-GigabitEthernet1/0/1] quit
# 配置端口Ten-GigabitEthernet1/0/2为Access端口,允许VLAN 1000的报文通过。
[PE_B] interface ten-gigabitethernet 1/0/2
[PE_B-Ten-GigabitEthernet1/0/2] port access vlan 1000
# 开启Ten-GigabitEthernet1/0/2端口的QinQ功能。
[PE_B-Ten-GigabitEthernet1/0/2] qinq enable
[PE_B-Ten-GigabitEthernet1/0/2] quit
# 配置端口Ten-GigabitEthernet1/0/3为Trunk端口,且允许VLAN 1000和VLAN 2000的报文通过,取消允许VLAN 1通过。
[PE_B] interface ten-gigabitethernet 1/0/3
[PE_B-Ten-GigabitEthernet1/0/3] port link-type trunk
[PE_B-Ten-GigabitEthernet1/0/3] port trunk permit vlan 1000 2000
[PE_B-Ten-GigabitEthernet1/0/3] undo port trunk permit vlan 1
[PE_B-Ten-GigabitEthernet1/0/3] quit
配置运营商网络中PE A到PE B之间的路径上的设备端口都允许VLAN 1000和VLAN 2000的报文携带VLAN Tag通过,且这些端口的MTU值至少为1504字节。
(1) 同一个公司跨越运营商网络的两个分支机构中处于同一CVLAN的两台PC互相进行Ping操作,可以Ping通,且这两台PC能够互相学习到对方的MAC地址。可见CVLAN信息能够跨越运营商网络进行透明传输。
(2) Customer A和Customer B中处于同一CVLAN(例如VLAN 130)中的两台PC互相进行Ping操作。在其中一台PC上查看ARP表项,发现它没有学到对方的MAC地址。可见不同公司中同一CVLAN的流量被二层隔离。
· PE A
#
vlan 1000
#
vlan 2000
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 1000
qinq enable
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 2000
qinq enable
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 1000 2000
#
· PE B
#
vlan 1000
#
vlan 2000
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 2000
qinq enable
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 1000
qinq enable
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 1000 2000
#
如图2所示,Customer A和Customer B各有两个分支机构需要通过运营商网络进行通信。Customer A和Customer B的网络中各有三种不同业务类型的数据,这三种业务类型的数据需要通过运营商网络提供的三个VLAN分开传输,以便运营商网络针对不同业务类型的数据配置不同的传输策略。
现要求通过配置1:2 VLAN映射功能实现:
· 用户不同业务类型的数据使用不同的外层VLAN Tag在运营商网络中传输;
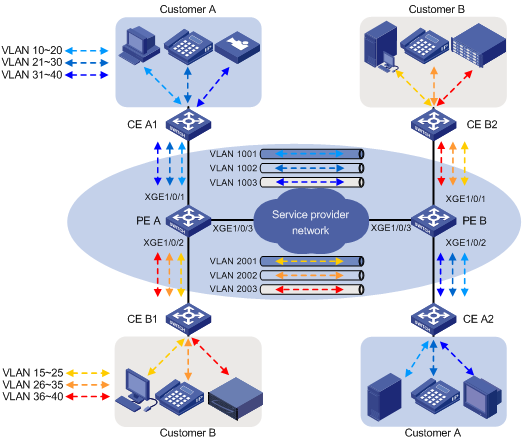
· 外层VLAN Tag的添加策略如表1所示,传输效果如图3所示;
· 添加外层VLAN Tag时,设备复制内层VLAN Tag的802.1p优先级作为外层VLAN Tag的802.1p优先级。
图2 1:2 VLAN映射组网图
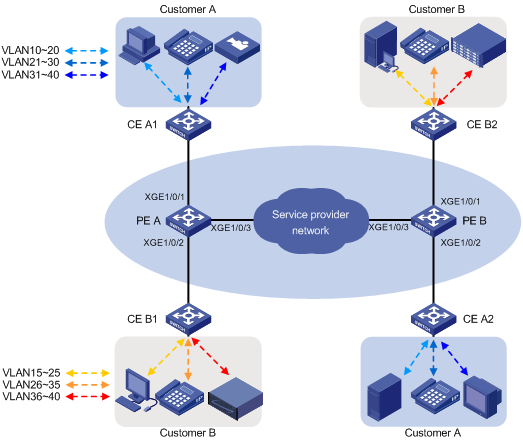
表1 外层VLAN Tag添加策略
|
用户的业务类型 |
用户网络VLAN |
运营商网络VLAN |
|
|
Customer A |
Video |
31 to 40 |
1003 |
|
Voice |
21 to 30 |
1002 |
|
|
Data |
10 to 20 |
1001 |
|
|
Customer B |
Storage |
36 to 40 |
2003 |
|
Voice |
26 to 35 |
2002 |
|
|
Data |
15 to 25 |
2001 |
|
· 请在PE A和PE B连接用户网络的端口上配置1:2 VLAN映射功能,为用户不同业务类型的数据报文添加不同的外层VLAN Tag。
· 为了保证用户网络接收的数据中不会包含运营商网络的VLAN信息,需要将PE A和PE B连接用户网络的端口的链路类型配置为Hybrid,并允许运营商封装的外层VLAN的报文不带VLAN Tag通过。
· 为了使设备在添加外层VLAN Tag时复制内层VLAN Tag的802.1p优先级做为外层VLAN Tag的802.1p优先级,配置端口信任报文的802.1p优先级。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
· 在携带两层VLAN Tag的报文的传输路径上,配置各端口的MTU值至少为1504字节。
· 在PE A和PE B的上行端口以及运营商网络的中间设备上,需要保证1:2 VLAN映射封装的外层VLAN Tag不被修改或移除。
# 创建CVLAN 10~40。
<PE_A> system-view
[PE_A] vlan 10 to 40
# 创建SVLAN 1001~1003和SVLAN 2001~2003。
[PE_A] vlan 1001 to 1003
[PE_A] vlan 2001 to 2003
(1) Ten-GigabitEthernet1/0/1端口的配置
# 配置端口为Hybrid端口。
[PE_A] interface ten-gigabitethernet 1/0/1
[PE_A-Ten-GigabitEthernet1/0/1] port link-type hybrid
# 配置端口允许CVLAN 10~40的报文携带VLAN Tag通过。
[PE_A-Ten-GigabitEthernet1/0/1] port hybrid vlan 10 to 40 tagged
# 配置端口允许SVLAN 1001~1003的报文通过,并且在发送时去掉外层Tag。
[PE_A-Ten-GigabitEthernet1/0/1] port hybrid vlan 1001 to 1003 untagged
# 配置端口取消允许VLAN 1通过。
[PE_A-Ten-GigabitEthernet1/0/1] undo port hybrid vlan 1
# 配置1:2 VLAN映射功能,为用户网络VLAN 10~20的报文封装VLAN 1001的外层VLAN Tag,为用户网络VLAN 21~30的报文封装VLAN 1002的外层VLAN Tag,为用户网络VLAN 31~40的报文封装VLAN 1003的外层VLAN Tag。
[PE_A-Ten-GigabitEthernet1/0/1] vlan mapping nest range 10 to 20 nested-vlan 1001
[PE_A-Ten-GigabitEthernet1/0/1] vlan mapping nest range 21 to 30 nested-vlan 1002
[PE_A-Ten-GigabitEthernet1/0/1] vlan mapping nest range 31 to 40 nested-vlan 1003
# 配置端口信任报文的802.1p优先级。
[PE_A-Ten-GigabitEthernet1/0/1] qos trust dot1p
[PE_A-Ten-GigabitEthernet1/0/1] quit
(2) Ten-GigabitEthernet1/0/2端口的配置
# 配置端口为Hybrid端口。
[PE_A] interface ten-gigabitethernet 1/0/2
[PE_A-Ten-GigabitEthernet1/0/2] port link-type hybrid
# 配置端口允许CVLAN 15~40的报文携带VLAN Tag通过。
[PE_A-Ten-GigabitEthernet1/0/2] port hybrid vlan 15 to 40 tagged
# 配置端口允许SVLAN 2001~2003的报文通过,并且在发送时去掉外层Tag。
[PE_A-Ten-GigabitEthernet1/0/2] port hybrid vlan 2001 to 2003 untagged
# 配置端口取消允许VLAN 1通过。
[PE_A-Ten-GigabitEthernet1/0/2] undo port hybrid vlan 1
# 配置1:2 VLAN映射功能,为用户网络VLAN 15~25的报文封装VLAN 2001的外层VLAN Tag,为用户网络VLAN 26~35的报文封装VLAN 2002的外层VLAN Tag,为用户网络VLAN 36~40的报文封装VLAN 2003的外层VLAN Tag。
[PE_A-Ten-GigabitEthernet1/0/2] vlan mapping nest range 15 to 25 nested-vlan 2001
[PE_A-Ten-GigabitEthernet1/0/2] vlan mapping nest range 26 to 35 nested-vlan 2002
[PE_A-Ten-GigabitEthernet1/0/2] vlan mapping nest range 36 to 40 nested-vlan 2003
# 配置端口信任报文的802.1p优先级。
[PE_A-Ten-GigabitEthernet1/0/2] qos trust dot1p
[PE_A-Ten-GigabitEthernet1/0/2] quit
(3) Ten-GigabitEthernet1/0/3端口的配置
# 配置端口为Trunk端口,且允许VLAN 1001~1003和VLAN 2001~2003的报文通过,取消允许VLAN 1通过。
[PE_A] interface ten-gigabitethernet 1/0/3
[PE_A-Ten-GigabitEthernet1/0/3] port link-type trunk
[PE_A-Ten-GigabitEthernet1/0/3] undo port trunk permit vlan 1
[PE_A-Ten-GigabitEthernet1/0/3] port trunk permit vlan 1001 to 1003 2001 to 2003
[PE_A-Ten-GigabitEthernet1/0/3] quit
# 创建CVLAN 10~40。
<PE_B> system-view
[PE_B] vlan 10 to 40
# 创建SVLAN 1001~1003、SVLAN 2001~2003。
[PE_B] vlan 1001 to 1003
[PE_B] vlan 2001 to 2003
(1) Ten-GigabitEthernet1/0/1端口的配置
# 配置端口为Hybrid端口。
[PE_B] interface ten-gigabitethernet 1/0/1
[PE_B-Ten-GigabitEthernet1/0/1] port link-type hybrid
# 配置端口允许CVLAN 15~40的报文携带VLAN Tag通过。
[PE_B-Ten-GigabitEthernet1/0/1] port hybrid vlan 15 to 40 tagged
# 配置端口允许SVLAN 2001~2003的报文通过,并且在发送时去掉外层Tag。
[PE_B-Ten-GigabitEthernet1/0/1] port hybrid vlan 2001 to 2003 untagged
# 配置端口取消允许VLAN 1通过。
[PE_B-Ten-GigabitEthernet1/0/1] undo port hybrid vlan 1
# 配置1:2 VLAN映射功能,为用户网络VLAN 15~25的报文封装VLAN 2001的外层VLAN Tag,为用户网络VLAN 26~35的报文封装VLAN 2002的外层VLAN Tag,为用户网络VLAN 36~40的报文封装VLAN 2003的外层VLAN Tag。
[PE_B-Ten-GigabitEthernet1/0/1] vlan mapping nest range 15 to 25 nested-vlan 2001
[PE_B-Ten-GigabitEthernet1/0/1] vlan mapping nest range 26 to 35 nested-vlan 2002
[PE_B-Ten-GigabitEthernet1/0/1] vlan mapping nest range 36 to 40 nested-vlan 2003
# 配置端口信任报文的802.1p优先级。
[PE_B-Ten-GigabitEthernet1/0/1] qos trust dot1p
[PE_B-Ten-GigabitEthernet1/0/1] quit
(2) Ten-GigabitEthernet1/0/2端口的配置
# 配置端口为Hybrid端口。
[PE_B] interface ten-gigabitethernet 1/0/2
[PE_B-Ten-GigabitEthernet1/0/2] port link-type hybrid
# 配置端口允许CVLAN 10~40的报文携带VLAN Tag通过。
[PE_B-Ten-GigabitEthernet1/0/2] port hybrid vlan 10 to 40 tagged
# 配置端口允许SVLAN 1001~1003的报文通过,并且在发送时去掉外层Tag。
[PE_B-Ten-GigabitEthernet1/0/2] port hybrid vlan 1001 to 1003 untagged
# 配置端口取消允许VLAN 1通过。
[PE_B-Ten-GigabitEthernet1/0/2] undo port hybrid vlan 1
# 配置1:2 VLAN映射功能,为用户网络VLAN 10~20的报文封装VLAN 1001的外层VLAN Tag,为用户网络VLAN 21~30的报文封装VLAN 1002的外层VLAN Tag,为用户网络VLAN 31~40的报文封装VLAN 1003的外层VLAN Tag。
[PE_B-Ten-GigabitEthernet1/0/2] vlan mapping nest range 10 to 20 nested-vlan 1001
[PE_B-Ten-GigabitEthernet1/0/2] vlan mapping nest range 21 to 30 nested-vlan 1002
[PE_B-Ten-GigabitEthernet1/0/2] vlan mapping nest range 31 to 40 nested-vlan 1003
# 配置端口信任报文的802.1p优先级。
[PE_B-Ten-GigabitEthernet1/0/2] qos trust dot1p
[PE_B-Ten-GigabitEthernet1/0/2] quit
(3) Ten-GigabitEthernet1/0/3端口的配置
# 配置端口为Trunk端口,且允许VLAN 1001~1003和VLAN 2001~2003的报文通过,取消允许VLAN 1通过。
[PE_B] interface ten-gigabitethernet 1/0/3
[PE_B-Ten-GigabitEthernet1/0/3] port link-type trunk
[PE_B-Ten-GigabitEthernet1/0/3] undo port trunk permit vlan 1
[PE_B-Ten-GigabitEthernet1/0/3] port trunk permit vlan 1001 to 1003 2001 to 2003
[PE_B-Ten-GigabitEthernet1/0/3] quit
配置运营商网络中PE A到PE B之间的路径上的设备端口都允许VLAN 1001~1003和VLAN 2001~2003的报文携带VLAN Tag通过,并配置各端口的MTU值至少为1504字节。
(1) 查看PE A上和PE B上VLAN映射的配置信息。
[PE_A] display vlan mapping
Interface Ten-GigabitEthernet1/0/1:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
10-20 N/A 1001 10-20
21-30 N/A 1002 21-30
31-40 N/A 1003 31-40
Interface Ten-GigabitEthernet1/0/2:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
15-25 N/A 2001 15-25
26-35 N/A 2002 26-35
36-40 N/A 2003 36-40
[PE_B] display vlan mapping
Interface Ten-GigabitEthernet1/0/1:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
15-25 N/A 2001 15-25
26-35 N/A 2002 26-35
36-40 N/A 2003 36-40
Interface Ten-GigabitEthernet1/0/2:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
10-20 N/A 1001 10-20
21-30 N/A 1002 21-30
31-40 N/A 1003 31-40
显示信息表明1:2 VLAN映射的配置正确。
(2) Customer A中跨越运营商网络的两个分支机构中处于同一CVLAN的两台PC互相进行Ping操作,可以Ping通,且这两台PC能够互相学习到对方的MAC地址。可见CVLAN信息能够跨越运营商网络进行透明传输。Customer B中的情况同理。
(3) Customer A和Customer B中处于同一CVLAN(例如VLAN 30)中的两台PC互相进行Ping操作。在其中一台PC上查看ARP表项,发现它没有学到对方的MAC地址。可见不同公司中同一CVLAN的流量被二层隔离。
· PE A
#
vlan 10 to 40
#
vlan 1001 to 1003
#
vlan 2001 to 2003
#
interface Ten-GigabitEthernet1/0/1
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 10 to 40 tagged
port hybrid vlan 1001 to 1003 untagged
vlan mapping nest range 10 to 20 nested-vlan 1001
vlan mapping nest range 21 to 30 nested-vlan 1002
vlan mapping nest range 31 to 40 nested-vlan 1003
qos trust dot1p
#
interface Ten-GigabitEthernet1/0/2
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 15 to 40 tagged
port hybrid vlan 2001 to 2003 untagged
vlan mapping nest range 15 to 25 nested-vlan 2001
vlan mapping nest range 26 to 35 nested-vlan 2002
vlan mapping nest range 36 to 40 nested-vlan 2003
qos trust dot1p
#
interface Ten-GigabitEthernet1/0/3
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 1001 to 1003 2001 to 2003
#
· PE B
#
vlan 10 to 40
#
vlan 1001 to 1003
#
vlan 2001 to 2003
#
interface Ten-GigabitEthernet1/0/1
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 15 to 40 tagged
port hybrid vlan 2001 to 2003 untagged
vlan mapping nest range 15 to 25 nested-vlan 2001
vlan mapping nest range 26 to 35 nested-vlan 2002
vlan mapping nest range 36 to 40 nested-vlan 2003
qos trust dot1p
#
interface Ten-GigabitEthernet1/0/2
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 10 to 40 tagged
port hybrid vlan 1001 to 1003 untagged
vlan mapping nest range 10 to 20 nested-vlan 1001
vlan mapping nest range 21 to 30 nested-vlan 1002
vlan mapping nest range 31 to 40 nested-vlan 1003
qos trust dot1p
#
interface Ten-GigabitEthernet1/0/3
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 1001 to 1003 2001 to 2003
#
如图4所示,Customer A和Customer B各有两个分支机构需要通过运营商网络进行通信。Customer A和Customer B的网络中各有三种不同业务类型的数据,且这三种业务类型的数据需要不同的传输优先级。
现要求通过在运营商网络中配置QoS策略使用户不同业务类型的数据使用不同的外层VLAN Tag在运营商网络中传输,并使优先级高的业务得到优先传输。外层VLAN Tag的添加策略如表2所示,传输效果如图5所示。
图4 QoS Nest&重标记优先级配置组网图
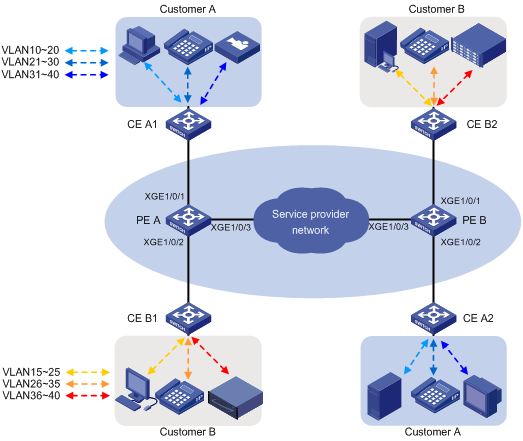
表2 外层VLAN Tag添加策略
|
用户的业务类型 |
用户网络VLAN |
运营商网络VLAN |
传输优先级 |
|
|
Customer A: |
Video |
31~40 |
1003 |
高 |
|
Voice |
21~30 |
1002 |
中 |
|
|
Data |
10~20 |
1001 |
低 |
|
|
Customer B: |
Storage |
36~40 |
2003 |
高 |
|
Voice |
26~35 |
2002 |
中 |
|
|
Data |
15~25 |
2001 |
低 |
|
· 请在PE A和PE B连接用户网络的端口上配置QoS策略为用户不同业务类型的数据报文添加不同的外层VLAN Tag并修改外层VLAN Tag的802.1p优先级。
· 为了保证用户网络接收的数据中不会包含运营商网络的VLAN信息,需要将PE A和PE B连接用户网络的端口的链路类型配置为Hybrid,并允许运营商封装的外层VLAN的报文不带VLAN Tag通过。
· 本举例中通过配置QoS策略为用户不同业务类型的数据报文添加不同的外层VLAN Tag并修改报文外层VLAN Tag的802.1p优先级,您也可以使用1:2 VLAN映射功能为用户不同业务类型的数据报文添加不同的外层VLAN Tag,同时配置QoS策略修改报文外层VLAN Tag的802.1p优先级。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
· 在端口上应用含有nest命令的策略时,只能应用到端口的入方向(inbound),并且需要在端口上开启QinQ功能,否则策略将不能成功应用。
· 当端口同时配置了QinQ功能和添加报文外层VLAN Tag的QoS策略时,匹配QoS策略流分类的报文将按QoS策略定义的流行为处理,不匹配QoS策略流分类的报文将按QinQ处理。
· 缺省情况下,端口为报文封装外层VLAN Tag时,如果端口信任报文的802.1p优先级,会将内层VLAN Tag的802.1p优先级复制到外层VLAN Tag的802.1p优先级,如果端口不信任报文的802.1p优先级或入报文没有携带VLAN Tag,会将接收报文的端口的端口优先级作为外层VLAN Tag的802.1p优先级。
· 需要保证QinQ报文传输路径上,报文的外层VLAN Tag不被修改或移除。
· QinQ为报文加上外层VLAN Tag后,内层VLAN Tag将被当作报文的数据部分进行传输,报文长度将增加4个字节。因此建议用户适当增加QinQ报文传输路径上各接口的MTU值(至少为1504字节)。
# 创建为用户数据分配的VLAN,即VLAN 1001~VLAN 1003、VLAN 2001~VLAN 2003。
<PE_A> system-view
[PE_A] vlan 1001 to 1003
[PE_A] vlan 2001 to 2003
(1) 配置端口Ten-GigabitEthernet1/0/1
# 配置端口为Hybrid端口,允许VLAN 1001~VLAN 1003的报文通过,并且在发送时去掉外层Tag,取消允许VLAN 1通过。
[PE_A] interface ten-gigabitethernet 1/0/1
[PE_A-Ten-GigabitEthernet1/0/1] port link-type hybrid
[PE_A-Ten-GigabitEthernet1/0/1] undo port hybrid vlan 1
[PE_A-Ten-GigabitEthernet1/0/1] port hybrid vlan 1001 to 1003 untagged
# 开启端口的QinQ功能。
[PE_A-Ten-GigabitEthernet1/0/1] qinq enable
# 配置端口信任报文的802.1p优先级。
[PE_A-Ten-GigabitEthernet1/0/1] qos trust dot1p
[PE_A-Ten-GigabitEthernet1/0/1] quit
(2) 配置端口Ten-GigabitEthernet1/0/2
# 配置端口为Hybrid端口,允许VLAN 2001~VLAN 2003的报文通过,并且在发送时去掉外层Tag,取消允许VLAN 1通过。
[PE_A] interface ten-gigabitethernet 1/0/2
[PE_A-Ten-GigabitEthernet1/0/2] port link-type hybrid
[PE_A-Ten-GigabitEthernet1/0/2] undo port hybrid vlan 1
[PE_A-Ten-GigabitEthernet1/0/2] port hybrid vlan 2001 to 2003 untagged
# 开启端口的QinQ功能。
[PE_A-Ten-GigabitEthernet1/0/2] qinq enable
# 配置端口信任报文的802.1p优先级。
[PE_A-Ten-GigabitEthernet1/0/2] qos trust dot1p
[PE_A-Ten-GigabitEthernet1/0/2] quit
(3) 配置端口Ten-GigabitEthernet1/0/3
# 配置端口为Trunk端口,且允许VLAN 1001~VLAN 1003和VLAN 2001~VLAN 2003的报文通过,取消允许VLAN 1通过。
[PE_A] interface ten-gigabitethernet 1/0/3
[PE_A-Ten-GigabitEthernet1/0/3] port link-type trunk
[PE_A-Ten-GigabitEthernet1/0/3] undo port trunk permit vlan 1
[PE_A-Ten-GigabitEthernet1/0/3] port trunk permit vlan 1001 to 1003 2001 to 2003
[PE_A-Ten-GigabitEthernet1/0/3] quit
(4) 配置QoS策略
# 为Customer A创建一个流分类,匹配规则为用户网络中普通业务数据对应的VLAN。
[PE_A] traffic classifier customer_A_pc
[PE_A-classifier-customer_A_pc] if-match customer-vlan-id 10 to 20
[PE_A-classifier-customer_A_pc] quit
# 按同样方法创建匹配Customer A网络中语音数据和视频数据的流分类。
[PE_A] traffic classifier customer_A_voice
[PE_A-classifier-customer_A_voice] if-match customer-vlan-id 21 to 30
[PE_A-classifier-customer_A_voice] quit
[PE_A] traffic classifier customer_A_video
[PE_A-classifier-customer_A_video] if-match customer-vlan-id 31 to 40
[PE_A-classifier-customer_A_video] quit
# 为Customer A的三种业务数据创建三个流行为,动作为封装相应的外层VLAN Tag和重标记报文外层VLAN Tag的802.1p优先级。
[PE_A] traffic behavior customer_A_pc
[PE_A-behavior-customer_A_pc] nest top-most vlan 1001
[PE_A-behavior-customer_A_pc] remark dot1p 3
[PE_A-behavior-customer_A_pc] quit
[PE_A] traffic behavior customer_A_voice
[PE_A-behavior-customer_A_voice] nest top-most vlan 1002
[PE_A-behavior-customer_A_voice] remark dot1p 5
[PE_A-behavior-customer_A_voice] quit
[PE_A] traffic behavior customer_A_video
[PE_A-behavior-customer_A_video] nest top-most vlan 1003
[PE_A-behavior-customer_A_video] remark dot1p 7
[PE_A-behavior-customer_A_video] quit
# 创建用于Customer A的QoS策略,将匹配用户业务数据的流分类与封装相应外层VLAN Tag和重标记报文外层VLAN Tag优先级的流行为进行一一关联。
[PE_A] qos policy customer_A
[PE_A-qospolicy-customer_A] classifier customer_A_pc behavior customer_A_pc
[PE_A-qospolicy-customer_A] classifier customer_A_voice behavior customer_A_voice
[PE_A-qospolicy-customer_A] classifier customer_A_video behavior customer_A_video
[PE_A-qospolicy-customer_A] quit
# 将上面创建的策略应用到Ten-GigabitEthernet 1/0/1端口的入方向。
[PE_A] interface ten-gigabitethernet 1/0/1
[PE_A-Ten-GigabitEthernet1/0/1] qos apply policy customer_A inbound
[PE_A-Ten-GigabitEthernet1/0/1] quit
# 使用类似方法为Customer B的三种业务数据创建流分类。
[PE_A] traffic classifier customer_B_pc
[PE_A-classifier-customer_B_pc] if-match customer-vlan-id 15 to 25
[PE_A-classifier-customer_B_pc] quit
[PE_A] traffic classifier customer_B_voice
[PE_A-classifier-customer_B_voice] if-match customer-vlan-id 26 to 35
[PE_A-classifier-customer_B_voice] quit
[PE_A] traffic classifier customer_B_storage
[PE_A-classifier-customer_B_storage] if-match customer-vlan-id 36 to 40
[PE_A-classifier-customer_B_storage] quit
# 为Customer B的三种业务数据创建三个流行为,动作为封装相应的外层VLAN Tag和重标记报文外层VLAN Tag的802.1p优先级。
[PE_A] traffic behavior customer_B_pc
[PE_A-behavior-customer_B_pc] nest top-most vlan 2001
[PE_A-behavior-customer_B_pc] remark dot1p 3
[PE_A-behavior-customer_B_pc] quit
[PE_A] traffic behavior customer_B_voice
[PE_A-behavior-customer_B_voice] nest top-most vlan 2002
[PE_A-behavior-customer_B_voice] remark dot1p 5
[PE_A-behavior-customer_B_voice] quit
[PE_A] traffic behavior customer_B_storage
[PE_A-behavior-customer_B_storage] nest top-most vlan 2003
[PE_A-behavior-customer_B_storage] remark dot1p 7
[PE_A-behavior-customer_B_storage] quit
# 创建用于Customer B的QoS策略,将匹配用户业务数据的流分类与封装相应外层VLAN Tag和重标记报文外层VLAN Tag优先级的流行为进行一一关联。
[PE_A] qos policy customer_B
[PE_A-qospolicy-customer_B] classifier customer_B_pc behavior customer_B_pc
[PE_A-qospolicy-customer_B] classifier customer_B_voice behavior customer_B_voice
[PE_A-qospolicy-customer_B] classifier customer_B_storage behavior customer_B_storage
[PE_A-qospolicy-customer_B] quit
# 将上面创建的策略应用到Ten-GigabitEthernet 1/0/2端口的入方向。
[PE_A] interface ten-gigabitethernet 1/0/2
[PE_A-Ten-GigabitEthernet1/0/2] qos apply policy customer_B inbound
[PE_A-Ten-GigabitEthernet1/0/2] quit
# 创建为用户数据分配的VLAN,即VLAN 1001~VLAN 1003、VLAN 2001~VLAN 2003。
<PE_B> system-view
[PE_B] vlan 1001 to 1003
[PE_B] vlan 2001 to 2003
(1) 配置端口Ten-GigabitEthernet1/0/1
# 配置端口为Hybrid端口,允许VLAN 2001~VLAN 2003的报文通过,并且在发送时去掉外层Tag,取消允许VLAN 1通过。
[PE_B] interface ten-gigabitethernet 1/0/1
[PE_B-Ten-GigabitEthernet1/0/1] port link-type hybrid
[PE_B-Ten-GigabitEthernet1/0/1] undo port hybrid vlan 1
[PE_B-Ten-GigabitEthernet1/0/1] port hybrid vlan 2001 to 2003 untagged
# 开启端口的QinQ功能。
[PE_B-Ten-GigabitEthernet1/0/1] qinq enable
# 配置端口信任报文的802.1p优先级。
[PE_B-Ten-GigabitEthernet1/0/1] qos trust dot1p
[PE_B-Ten-GigabitEthernet1/0/1] quit
(2) 配置端口Ten-GigabitEthernet1/0/2
# 配置端口为Hybrid端口,允许VLAN 1001~VLAN 1003的报文通过,并且在发送时去掉外层Tag,取消允许VLAN 1通过。
[PE_B] interface ten-gigabitethernet 1/0/2
[PE_B-Ten-GigabitEthernet1/0/2] port link-type hybrid
[PE_B-Ten-GigabitEthernet1/0/2] undo port hybrid vlan 1
[PE_B-Ten-GigabitEthernet1/0/2] port hybrid vlan 1001 to 1003 untagged
# 开启端口的QinQ功能。
[PE_B-Ten-GigabitEthernet1/0/2] qinq enable
# 配置端口信任报文的802.1p优先级。
[PE_B-Ten-GigabitEthernet1/0/2] qos trust dot1p
[PE_B-Ten-GigabitEthernet1/0/2] quit
(3) 配置端口Ten-GigabitEthernet1/0/3
# 配置端口为Trunk端口,且允许VLAN 1001~VLAN 1003和VLAN 2001~VLAN 2003的报文通过,取消允许VLAN 1通过。
[PE_B] interface ten-gigabitethernet 1/0/3
[PE_B-Ten-GigabitEthernet1/0/3] port link-type trunk
[PE_B-Ten-GigabitEthernet1/0/3] undo port trunk permit vlan 1
[PE_B-Ten-GigabitEthernet1/0/3] port trunk permit vlan 1001 to 1003 2001 to 2003
[PE_B-Ten-GigabitEthernet1/0/3] quit
(4) 配置QoS策略
# 按PE A设备的配置方法,为Customer A的业务数据配置流分类。
[PE_B] traffic classifier customer_A_pc
[PE_B-classifier-customer_A_pc] if-match customer-vlan-id 10 to 20
[PE_B-classifier-customer_A_pc] quit
[PE_B] traffic classifier customer_A_voice
[PE_B-classifier-customer_A_voice] if-match customer-vlan-id 21 to 30
[PE_B-classifier-customer_A_voice] quit
[PE_B] traffic classifier customer_A_video
[PE_B-classifier-customer_A_video] if-match customer-vlan-id 31 to 40
[PE_B-classifier-customer_A_video] quit
# 为Customer A的三种业务数据创建三个流行为,动作为封装相应的外层VLAN Tag和重标记报文外层VLAN Tag的802.1p优先级。
[PE_B] traffic behavior customer_A_pc
[PE_B-behavior-customer_A_pc] nest top-most vlan 1001
[PE_B-behavior-customer_A_pc] remark dot1p 3
[PE_B-behavior-customer_A_pc] quit
[PE_B] traffic behavior customer_A_voice
[PE_B-behavior-customer_A_voice] nest top-most vlan 1002
[PE_B-behavior-customer_A_voice] remark dot1p 5
[PE_B-behavior-customer_A_voice] quit
[PE_B] traffic behavior customer_A_video
[PE_B-behavior-customer_A_video] nest top-most vlan 1003
[PE_B-behavior-customer_A_video] remark dot1p 7
[PE_B-behavior-customer_A_video] quit
# 创建用于Customer A的QoS策略,将匹配用户业务数据的流分类与封装相应外层VLAN Tag和重标记报文外层VLAN Tag优先级的流行为进行一一关联。
[PE_B] qos policy customer_A
[PE_B-qospolicy-customer_A] classifier customer_A_pc behavior customer_A_pc
[PE_B-qospolicy-customer_A] classifier customer_A_voice behavior customer_A_voice
[PE_B-qospolicy-customer_A] classifier customer_A_video behavior customer_A_video
[PE_B-qospolicy-customer_A] quit
# 将上面创建的策略应用到Ten-GigabitEthernet 1/0/2端口的入方向。
[PE_B] interface ten-gigabitethernet 1/0/2
[PE_B-Ten-GigabitEthernet1/0/2] qos apply policy customer_A inbound
[PE_B-Ten-GigabitEthernet1/0/2] quit
# 使用类似方法为Customer B的三种业务数据创建流分类。
[PE_B] traffic classifier customer_B_pc
[PE_B-classifier-customer_B_pc] if-match customer-vlan-id 15 to 25
[PE_B-classifier-customer_B_pc] quit
[PE_B] traffic classifier customer_B_voice
[PE_B-classifier-customer_B_voice] if-match customer-vlan-id 26 to 35
[PE_B-classifier-customer_B_voice] quit
[PE_B] traffic classifier customer_B_storage
[PE_B-classifier-customer_B_storage] if-match customer-vlan-id 36 to 40
[PE_B-classifier-customer_B_storage] quit
# 为Customer B的三种业务数据创建三个流行为,动作为封装相应的外层VLAN Tag和重标记报文外层VLAN Tag的802.1p优先级。
[PE_B] traffic behavior customer_B_pc
[PE_B-behavior-customer_B_pc] nest top-most vlan 2001
[PE_B-behavior-customer_B_pc] remark dot1p 3
[PE_B-behavior-customer_B_pc] quit
[PE_B] traffic behavior customer_B_voice
[PE_B-behavior-customer_B_voice] nest top-most vlan 2002
[PE_B-behavior-customer_B_voice] remark dot1p 5
[PE_B-behavior-customer_B_voice] quit
[PE_B] traffic behavior customer_B_storage
[PE_B-behavior-customer_B_storage] nest top-most vlan 2003
[PE_B-behavior-customer_B_storage] remark dot1p 7
[PE_B-behavior-customer_B_storage] quit
# 创建用于Customer B的QoS策略,将匹配用户业务数据的流分类与封装相应外层VLAN Tag和重标记报文外层VLAN Tag优先级的流行为进行一一关联。
[PE_B] qos policy customer_B
[PE_B-qospolicy-customer_B] classifier customer_B_pc behavior customer_B_pc
[PE_B-qospolicy-customer_B] classifier customer_B_voice behavior customer_B_voice
[PE_B-qospolicy-customer_B] classifier customer_B_storage behavior customer_B_storage
[PE_B-qospolicy-customer_B] quit
# 将上面创建的策略应用到Ten-GigabitEthernet 1/0/1端口的入方向。
[PE_B] interface ten-gigabitethernet 1/0/1
[PE_B-Ten-GigabitEthernet1/0/1] qos apply policy customer_B inbound
[PE_B-Ten-GigabitEthernet1/0/1] quit
配置运营商网络中PE A到PE B之间的路径上的设备端口都允许VLAN 1001~VLAN 1003和VLAN 2001~VLAN 2003的报文携带VLAN Tag通过,并配置各端口的MTU值为至少1504字节。
(1) 使用display this命令查看端口的配置,例如:
# 查看PE A上端口Ten-GigabitEthernet1/0/1的配置。
[PE_A] interface ten-gigabitethernet 1/0/1
[PE_A-Ten-GigabitEthernet1/0/1] display this
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 1001 to 1003 untagged
qinq enable
qos trust dot1p
qos apply policy customer_A inbound
#
Return
[PE_A-Ten-GigabitEthernet1/0/1] quit
(2) 查看配置的策略是否正确下发到端口,例如:
# 查看PE A上端口Ten-GigabitEthernet 1/0/1上应用的策略。
[PE_A] display qos policy interface ten-gigabitethernet 1/0/1
Interface: Ten-GigabitEthernet1/0/1
Direction: Inbound
Policy: customer_A
Classifier: customer_A_pc
Operator: AND
Rule(s) :
If-match customer-vlan-id 10 to 20
Behavior: customer_A_pc
Nesting:
Nest top-most vlan-id 1001
Marking:
Remark dot1p 3
Classifier: customer_A_voice
Operator: AND
Rule(s) :
If-match customer-vlan-id 21 to 30
Behavior: customer_A_voice
Nesting:
Nest top-most vlan-id 1002
Marking:
Remark dot1p 5
Classifier: customer_A_video
Operator: AND
Rule(s) :
If-match customer-vlan-id 31 to 40
Behavior: customer_A_video
Nesting:
Nest top-most vlan-id 1003
Marking:
Remark dot1p 7
· PE A
#
vlan 1001 to 1003
#
vlan 2001 to 2003
#
traffic classifier customer_A_pc operator and
if-match customer-vlan-id 10 to 20
#
traffic classifier customer_A_voice operator and
if-match customer-vlan-id 21 to 30
#
traffic classifier customer_A_video operator and
if-match customer-vlan-id 31 to 40
#
traffic classifier customer_B_pc operator and
if-match customer-vlan-id 15 to 25
#
traffic classifier customer_B_voice operator and
if-match customer-vlan-id 26 to 35
#
traffic classifier customer_B_storage operator and
if-match customer-vlan-id 36 to 40
#
traffic behavior customer_A_pc
nest top-most vlan 1001
remark dot1p 3
#
traffic behavior customer_A_voice
nest top-most vlan 1002
remark dot1p 5
#
traffic behavior customer_A_video
nest top-most vlan 1003
remark dot1p 7
#
traffic behavior customer_B_pc
nest top-most vlan 2001
remark dot1p 3
#
traffic behavior customer_B_voice
nest top-most vlan 2002
remark dot1p 5
#
traffic behavior customer_B_storage
nest top-most vlan 2003
remark dot1p 7
#
qos policy customer_A
classifier customer_A_pc behavior customer_A_pc
classifier customer_A_voice behavior customer_A_voice
classifier customer_A_video behavior customer_A_video
#
qos policy customer_B
classifier customer_B_pc behavior customer_B_pc
classifier customer_B_voice behavior customer_B_voice
classifier customer_B_storage behavior customer_B_storage
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 1001 to 1003 untagged
qinq enable
qos trust dot1p
qos apply policy customer_A inbound
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 2001 to 2003 untagged
qinq enable
qos trust dot1p
qos apply policy customer_B inbound
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 1001 to 1003 2001 to 2003
#
· ProviderB的配置
#
vlan 1001 to 1003
#
vlan 2001 to 2003
#
traffic classifier customer_A_pc operator and
if-match customer-vlan-id 10 to 20
#
traffic classifier customer_A_voice operator and
if-match customer-vlan-id 21 to 30
#
traffic classifier customer_A_video operator and
if-match customer-vlan-id 31 to 40
#
traffic classifier customer_B_pc operator and
if-match customer-vlan-id 15 to 25
#
traffic classifier customer_B_voice operator and
if-match customer-vlan-id 26 to 35
#
traffic classifier customer_B_storage operator and
if-match customer-vlan-id 36 to 40
#
traffic behavior customer_A_pc
nest top-most vlan 1001
remark dot1p 3
#
traffic behavior customer_A_voice
nest top-most vlan 1002
remark dot1p 5
#
traffic behavior customer_A_video
nest top-most vlan 1003
remark dot1p 7
#
traffic behavior customer_B_pc
nest top-most vlan 2001
remark dot1p 3
#
traffic behavior customer_B_voice
nest top-most vlan 2002
remark dot1p 5
#
traffic behavior customer_B_storage
nest top-most vlan 2003
remark dot1p 7
#
qos policy customer_A
classifier customer_A_pc behavior customer_A_pc
classifier customer_A_voice behavior customer_A_voice
classifier customer_A_video behavior customer_A_video
#
qos policy customer_B
classifier customer_B_pc behavior customer_B_pc
classifier customer_B_voice behavior customer_B_voice
classifier customer_B_storage behavior customer_B_storage
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 2001 to 2003 untagged
qinq enable
qos trust dot1p
qos apply policy customer_B inbound
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 1001 to 1003 untagged
qinq enable
qos trust dot1p
qos apply policy customer_A inbound
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 1001 to 1003 2001 to 2003
#
如图6所示:在某小区,服务提供商为每个家庭都提供了PC、VoD和VoIP这三种数据服务,每个家庭都通过各自的家庭网关接入楼道交换机,并通过DHCP方式自动获取IP地址。每个家庭网关都分别将PC、VoD和VoIP业务依次划分到VLAN 1~3。
现要求通过配置1:1和N:1 VLAN映射功能实现以下功能:
· 在楼道交换机上,为了隔离不同家庭的同类业务,将每个家庭的每种业务都划分到不同的VLAN;
· 在园区交换机上,为了节省VLAN资源,将所有家庭的同类业务都划分到相同的VLAN,即分别将PC、VoD和VoIP业务依次划分到VLAN 501~503。
图6 1:1和N:1 VLAN映射组网示意图
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
# 创建原始VLAN——VLAN 2~ 3(原始VLAN 1设备缺省已创建)。
<SwitchA> system-view
[SwitchA] vlan 2 to 3
# 创建转换后VLAN——VLAN 101~102、VLAN 201~202和VLAN 301~302。
[SwitchA] vlan 101 to 102
[SwitchA] vlan 201 to 202
[SwitchA] vlan 301 to 302
# 配置下行端口Ten-GigabitEthernet1/0/1为Trunk端口且允许原始VLAN及转换后VLAN通过。
[SwitchA] interface ten-gigabitethernet 1/0/1
[SwitchA-Ten-GigabitEthernet1/0/1] port link-type trunk
[SwitchA-Ten-GigabitEthernet1/0/1] port trunk permit vlan 1 2 3 101 201 301
# 在端口Ten-GigabitEthernet1/0/1上配置1:1 VLAN映射功能,将VLAN 1的Tag替换为VLAN 101的Tag,将VLAN 2的Tag替换为VLAN 201的Tag,将VLAN 3的Tag替换为VLAN 301的Tag。
[SwitchA-Ten-GigabitEthernet1/0/1] vlan mapping 1 translated-vlan 101
[SwitchA-Ten-GigabitEthernet1/0/1] vlan mapping 2 translated-vlan 201
[SwitchA-Ten-GigabitEthernet1/0/1] vlan mapping 3 translated-vlan 301
[SwitchA-Ten-GigabitEthernet1/0/1] quit
# 配置下行端口Ten-GigabitEthernet1/0/2为Trunk端口且允许原始VLAN及转换后VLAN通过。
[SwitchA] interface ten-gigabitethernet 1/0/2
[SwitchA-Ten-GigabitEthernet1/0/2] port link-type trunk
[SwitchA-Ten-GigabitEthernet1/0/2] port trunk permit vlan 1 2 3 102 202 302
# 在端口Ten-GigabitEthernet1/0/2上配置1:1 VLAN映射功能,将VLAN 1的Tag替换为VLAN 102的Tag,将VLAN 2的Tag替换为VLAN 202的Tag,将VLAN 3的Tag替换为VLAN 302的Tag。
[SwitchA-Ten-GigabitEthernet1/0/2] vlan mapping 1 translated-vlan 102
[SwitchA-Ten-GigabitEthernet1/0/2] vlan mapping 2 translated-vlan 202
[SwitchA-Ten-GigabitEthernet1/0/2] vlan mapping 3 translated-vlan 302
[SwitchA-Ten-GigabitEthernet1/0/2] quit
# 配置上行端口Ten-GigabitEthernet1/0/3为Trunk端口,且允许转换后VLAN通过。
[SwitchA] interface ten-gigabitethernet 1/0/3
[SwitchA-Ten-GigabitEthernet1/0/3] port link-type trunk
[SwitchA-Ten-GigabitEthernet1/0/3] port trunk permit vlan 101 201 301 102 202 302
[SwitchA-Ten-GigabitEthernet1/0/3] quit
Switch B的配置与Switch A相似,配置过程略。
# 使能DHCP Snooping功能。
<SwitchC> system-view
[SwitchC] dhcp snooping enable
# 创建原始VLAN和转换后VLAN,并在这些VLAN上分别使能ARP Detection功能。
[SwitchC] vlan 101
[SwitchC-vlan101] arp detection enable
[SwitchC-vlan101] vlan 201
[SwitchC-vlan201] arp detection enable
[SwitchC-vlan201] vlan 301
[SwitchC-vlan301] arp detection enable
[SwitchC-vlan301] vlan 102
[SwitchC-vlan102] arp detection enable
[SwitchC-vlan102] vlan 202
[SwitchC-vlan202] arp detection enable
[SwitchC-vlan202] vlan 302
[SwitchC-vlan302] arp detection enable
[SwitchC-vlan302] vlan 103
[SwitchC-vlan103] arp detection enable
[SwitchC-vlan103] vlan 203
[SwitchC-vlan203] arp detection enable
[SwitchC-vlan203] vlan 303
[SwitchC-vlan303] arp detection enable
[SwitchC-vlan303] vlan 104
[SwitchC-vlan104] arp detection enable
[SwitchC-vlan104] vlan 204
[SwitchC-vlan204] arp detection enable
[SwitchC-vlan204] vlan 304
[SwitchC-vlan304] arp detection enable
[SwitchC-vlan304] vlan 501
[SwitchC-vlan501] arp detection enable
[SwitchC-vlan501] vlan 502
[SwitchC-vlan502] arp detection enable
[SwitchC-vlan502] vlan 503
[SwitchC-vlan503] arp detection enable
[SwitchC-vlan503] quit
# 配置下行端口Ten-GigabitEthernet1/0/1为Trunk端口且允许原始VLAN及转换后VLAN通过。
[SwitchC] interface ten-gigabitethernet 1/0/1
[SwitchC-Ten-GigabitEthernet1/0/1] port link-type trunk
[SwitchC-Ten-GigabitEthernet1/0/1] port trunk permit vlan 101 102 201 202 301 302 501 to 503
# 在端口Ten-GigabitEthernet1/0/1上配置N:1 VLAN映射,将VLAN 101~102的Tag替换为VLAN 501的Tag,将VLAN 201~202的Tag替换为VLAN 502的Tag,将VLAN 301~302的Tag替换为VLAN 503的Tag。
[SwitchC-Ten-GigabitEthernet1/0/1] vlan mapping uni range 101 to 102 translated-vlan 501
[SwitchC-Ten-GigabitEthernet1/0/1] vlan mapping uni range 201 to 202 translated-vlan 502
[SwitchC-Ten-GigabitEthernet1/0/1] vlan mapping uni range 301 to 302 translated-vlan 503
# 在端口Ten-GigabitEthernet1/0/1上启用DHCP Snooping表项记录功能,以记录原始VLAN及转换后VLAN的对应关系。
[SwitchC-Ten-GigabitEthernet1/0/1] dhcp snooping binding record
[SwitchC-Ten-GigabitEthernet1/0/1] quit
# 配置下行端口Ten-GigabitEthernet1/0/2为Trunk端口且允许原始VLAN及转换后VLAN通过。
[SwitchC] interface ten-gigabitethernet 1/0/2
[SwitchC-Ten-GigabitEthernet1/0/2] port link-type trunk
[SwitchC-Ten-GigabitEthernet1/0/2] port trunk permit vlan 103 104 203 204 303 304 501 to 503
# 在端口Ten-GigabitEthernet1/0/2上配置N:1 VLAN映射,将VLAN 103~104的Tag替换为VLAN 501的Tag,将VLAN 203~204的Tag替换为VLAN 502的Tag,将VLAN 303~304的Tag替换为VLAN 503的Tag。
[SwitchC-Ten-GigabitEthernet1/0/2] vlan mapping uni range 103 to 104 translated-vlan 501
[SwitchC-Ten-GigabitEthernet1/0/2] vlan mapping uni range 203 to 204 translated-vlan 502
[SwitchC-Ten-GigabitEthernet1/0/2] vlan mapping uni range 303 to 304 translated-vlan 503
# 在端口Ten-GigabitEthernet1/0/2上启用DHCP Snooping表项记录功能,以记录原始VLAN及转换后VLAN的对应关系。
[SwitchC-Ten-GigabitEthernet1/0/2] dhcp snooping binding record
[SwitchC-Ten-GigabitEthernet1/0/2] quit
# 在上行端口Ten-GigabitEthernet1/0/3上配置网络侧N:1 VLAN映射。
[SwitchC] interface ten-gigabitethernet 1/0/3
[SwitchC-Ten-GigabitEthernet1/0/3] vlan mapping nni
# 配置端口Ten-GigabitEthernet1/0/3为Trunk端口且允许转换后VLAN通过,并配置该端口为DHCP Snooping信任端口和ARP信任端口。
[SwitchC-Ten-GigabitEthernet1/0/3] port link-type trunk
[SwitchC-Ten-GigabitEthernet1/0/3] port trunk permit vlan 501 to 503
[SwitchC-Ten-GigabitEthernet1/0/3] dhcp snooping trust
[SwitchC-Ten-GigabitEthernet1/0/3] arp detection trust
[SwitchC-Ten-GigabitEthernet1/0/3] quit
# 创建转换后VLAN——VLAN 501~503。
<SwitchD> system-view
[SwitchD] vlan 501 to 503
# 配置端口Ten-GigabitEthernet1/0/1为Trunk端口且允许转换后VLAN通过。
[SwitchD] interface ten-gigabitethernet 1/0/1
[SwitchD-Ten-GigabitEthernet1/0/1] port link-type trunk
[SwitchD-Ten-GigabitEthernet1/0/1] port trunk permit vlan 501 to 503
[SwitchD-Ten-GigabitEthernet1/0/1] quit
(1) 查看Switch A上的VLAN映射配置信息
[SwitchA] display vlan mapping
Interface Ten-GigabitEthernet1/0/1:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
1 N/A 101 N/A
2 N/A 201 N/A
3 N/A 301 N/A
Interface Ten-GigabitEthernet1/0/2:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
1 N/A 102 N/A
2 N/A 202 N/A
3 N/A 302 N/A
(2) 查看Switch B上的VLAN映射配置信息
Switch B上的VLAN映射配置信息与Switch A相似,显示信息略。
(3) 查看Switch C上的VLAN映射配置信息
[SwitchC] display vlan mapping
Interface Ten-GigabitEthernet1/0/1:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
101-102 N/A 501 N/A
201-202 N/A 502 N/A
301-302 N/A 503 N/A
Interface Ten-GigabitEthernet1/0/2:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
103-104 N/A 501 N/A
203-204 N/A 502 N/A
303-304 N/A 503 N/A
以上信息表明,Switch A和Switch B上的1:1 VLAN映射,以及Switch C上的N:1 VLAN映射配置成功。
· Switch A
#
vlan 1
#
vlan 2 to 3
#
vlan 101 to 102
#
vlan 201 to 202
#
vlan 301 to 302
#
interface Ten-GigabitEthernet1/0/1
port link-type trunk
port trunk permit vlan 1 to 3 101 201 301
vlan mapping 1 translated-vlan 101
vlan mapping 2 translated-vlan 201
vlan mapping 3 translated-vlan 301
#
interface Ten-GigabitEthernet1/0/2
port link-type trunk
port trunk permit vlan 1 to 3 102 202 302
vlan mapping 1 translated-vlan 102
vlan mapping 2 translated-vlan 202
vlan mapping 3 translated-vlan 302
#
interface Ten-GigabitEthernet1/0/3
port link-type trunk
port trunk permit vlan 1 101 to 102 201 to 202 301 to 302
#
· Switch B
#
vlan 1
#
vlan 2 to 3
#
vlan 103 to 104
#
vlan 203 to 204
#
vlan 303 to 304
#
interface Ten-GigabitEthernet1/0/1
port link-type trunk
port trunk permit vlan 1 to 3 103 203 303
vlan mapping 1 translated-vlan 103
vlan mapping 2 translated-vlan 203
vlan mapping 3 translated-vlan 303
#
interface Ten-GigabitEthernet1/0/2
port link-type trunk
port trunk permit vlan 1 to 3 104 204 304
vlan mapping 1 translated-vlan 104
vlan mapping 2 translated-vlan 204
vlan mapping 3 translated-vlan 304
#
interface Ten-GigabitEthernet1/0/3
port link-type trunk
port trunk permit vlan 1 103 to 104 203 to 204 303 to 304
#
· Switch C
#
dhcp snooping enable
#
vlan 101
arp detection enable
#
vlan 102
arp detection enable
#
vlan 103
arp detection enable
#
vlan 104
arp detection enable
#
vlan 201
arp detection enable
#
vlan 202
arp detection enable
#
vlan 203
arp detection enable
#
vlan 204
arp detection enable
#
vlan 301
arp detection enable
#
vlan 302
arp detection enable
#
vlan 303
arp detection enable
#
vlan 304
arp detection enable
#
vlan 501
arp detection enable
#
vlan 502
arp detection enable
#
vlan 503
arp detection enable
#
interface Ten-GigabitEthernet1/0/1
port link-type trunk
port trunk permit vlan 101 to 102 201 to 202 301 to 302 501 to 503
vlan mapping uni range 101 to 102 translated-vlan 501
vlan mapping uni range 201 to 202 translated-vlan 502
vlan mapping uni range 301 to 302 translated-vlan 503
dhcp snooping binding record
#
interface Ten-GigabitEthernet1/0/2
port link-type trunk
port trunk permit vlan 103 to 104 203 to 204 303 to 304 501 to 503
vlan mapping uni range 103 to 104 translated-vlan 501
vlan mapping uni range 203 to 204 translated-vlan 502
vlan mapping uni range 303 to 304 translated-vlan 503
dhcp snooping binding record
#
interface Ten-GigabitEthernet1/0/3
port link-type trunk
port trunk permit vlan 501 to 503
vlan mapping nni
arp detection trust
dhcp snooping trust
#
· Switch D
#
vlan 501 to 503
#
interface Ten-GigabitEthernet1/0/1
port link-type trunk
port trunk permit vlan 1 501 to 503
#
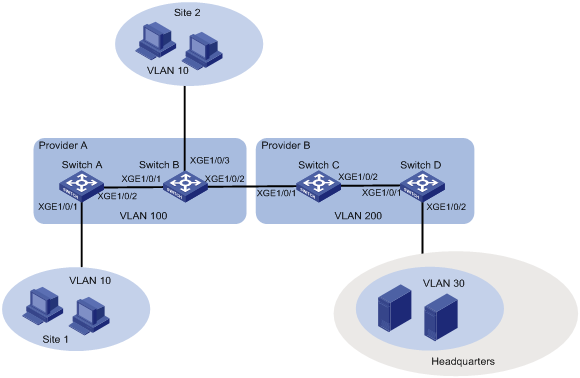
如图7所示,Site 1和Site 2是同一家公司的两个分支机构,同属于VLAN 10,通过运营商A提供的VPN接入服务,外层VLAN Tag为VLAN 100。当该公司被另一家公司收购之后,需要Site 1和Site 2接入新公司的网络。新公司的VPN服务由运营商B提供,外层VLAN Tag为VLAN 200,总部中能够为Site 1和Site 2提供服务的业务VLAN为VLAN 30。
现要求通过配置2:2 VLAN映射功能,在不改变Site 1、Site 2和运营商网络VLAN的配置的情况下,使Site 1和Site 2能够访问总部(Headquarts)VLAN 30的资源。
图7 2:2 VLAN映射典型配置组网示意图
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
2:2 VLAN映射功能只需要在两个运营商的边缘设备中的其中一台上配置即可,本例中我们以在Switch C上配置为例进行介绍。
# 创建VLAN 10和VLAN 100。
<SwitchA> system-view
[SwitchA] vlan 10
[SwitchA-vlan10] quit
[SwitchA] vlan 100
[SwitchA-vlan100] quit
# 在下行端口Ten-GigabitEthernet1/0/1上配置1:2 VLAN映射,为VLAN 10报文添加VLAN 100的外层VLAN Tag。
[SwitchA] interface ten-gigabitethernet 1/0/1
[SwitchA-Ten-GigabitEthernet1/0/1] vlan mapping nest single 10 nested-vlan 100
# 配置Ten-GigabitEthernet1/0/1为Hybrid端口且允许VLAN 10的报文携带VLAN Tag通过、VLAN 100的报文不携带VLAN Tag通过,取消允许VLAN 1通过。
[SwitchA-Ten-GigabitEthernet1/0/1] port link-type hybrid
[SwitchA-Ten-GigabitEthernet1/0/1] port hybrid vlan 10 tagged
[SwitchA-Ten-GigabitEthernet1/0/1] port hybrid vlan 100 untagged
[SwitchA-Ten-GigabitEthernet1/0/1] undo port hybrid vlan 1
[SwitchA-Ten-GigabitEthernet1/0/1] quit
# 配置上行端口Ten-GigabitEthernet1/0/2允许VLAN 100的报文通过,取消允许VLAN 1通过。
[SwitchA] interface ten-gigabitethernet 1/0/2
[SwitchA-Ten-GigabitEthernet1/0/2] port link-type trunk
[SwitchA-Ten-GigabitEthernet1/0/2] port trunk permit vlan 100
[SwitchA-Ten-GigabitEthernet1/0/2] undo port trunk permit vlan 1
[SwitchA-Ten-GigabitEthernet1/0/2] quit
# 创建VLAN 10和VLAN 100。
<SwitchB> system-view
[SwitchB] vlan 10
[SwitchB-vlan10] quit
[SwitchB] vlan 100
[SwitchB-vlan100] quit
# 在下行端口Ten-GigabitEthernet1/0/3上配置1:2 VLAN映射,为VLAN 10报文添加VLAN 100的外层VLAN Tag。
[SwitchB] interface ten-gigabitethernet 1/0/3
[SwitchB-Ten-GigabitEthernet1/0/3] vlan mapping nest single 10 nested-vlan 100
# 配置Ten-GigabitEthernet1/0/3为Hybrid端口且允许VLAN 10的报文携带VLAN Tag通过、VLAN100的报文不携带VLAN Tag通过,取消允许VLAN 1通过。
[SwitchB-Ten-GigabitEthernet1/0/3] port link-type hybrid
[SwitchB-Ten-GigabitEthernet1/0/3] port hybrid vlan 10 tagged
[SwitchB-Ten-GigabitEthernet1/0/3] port hybrid vlan 100 untagged
[SwitchB-Ten-GigabitEthernet1/0/3] undo port hybrid vlan 1
[SwitchB-Ten-GigabitEthernet1/0/3] quit
# 配置端口Ten-GigabitEthernet1/0/1允许VLAN 100的报文通过,取消允许VLAN 1通过。
[SwitchB] interface ten-gigabitethernet 1/0/1
[SwitchB-Ten-GigabitEthernet1/0/1] port link-type trunk
[SwitchB-Ten-GigabitEthernet1/0/1] port trunk permit vlan 100
[SwitchB-Ten-GigabitEthernet1/0/1] undo port trunk permit vlan 1
[SwitchB-Ten-GigabitEthernet1/0/1] quit
# 配置端口Ten-GigabitEthernet1/0/2允许VLAN 100的报文通过,取消允许VLAN 1通过。
[SwitchB] interface ten-gigabitethernet 1/0/2
[SwitchB-Ten-GigabitEthernet1/0/2] port link-type trunk
[SwitchB-Ten-GigabitEthernet1/0/2] port trunk permit vlan 100
[SwitchB-Ten-GigabitEthernet1/0/2] undo port trunk permit vlan 1
[SwitchB-Ten-GigabitEthernet1/0/2] quit
# 创建映射前外层VLAN 100和映射后外层VLAN 200。
<SwitchC> system-view
[SwitchC] vlan 100
[SwitchC-vlan100] quit
[SwitchC] vlan 200
[SwitchC-vlan200] quit
# 配置端口Ten-GigabitEthernet1/0/1允许VLAN 100和VLAN 200的报文通过,取消允许VLAN 1通过。
[SwitchC] interface ten-gigabitethernet 1/0/1
[SwitchC-Ten-GigabitEthernet1/0/1] port link-type trunk
[SwitchC-Ten-GigabitEthernet1/0/1] port trunk permit vlan 100 200
[SwitchC-Ten-GigabitEthernet1/0/1] undo port trunk permit vlan 1
# 在端口Ten-GigabitEthernet1/0/1上配置2:2 VLAN映射,将外层VLAN为100、内层VLAN为10的报文的VLAN ID转换为外层VLAN为200、内层VLAN为30。
[SwitchC-Ten-GigabitEthernet1/0/1] vlan mapping tunnel 100 10 translated-vlan 200 30
[SwitchC-Ten-GigabitEthernet1/0/1] quit
# 配置端口Ten-GigabitEthernet1/0/2允许VLAN 200的报文通过。
[SwitchC] interface ten-gigabitethernet 1/0/2
[SwitchC-Ten-GigabitEthernet1/0/2] port link-type trunk
[SwitchC-Ten-GigabitEthernet1/0/2] port trunk permit vlan 200
[SwitchC-Ten-GigabitEthernet1/0/2] undo port trunk permit vlan 1
[SwitchC-Ten-GigabitEthernet1/0/2] quit
# 创建VLAN 30和VLAN 200。
<SwitchD> system-view
[SwitchD] vlan 30
[SwitchD-vlan30] quit
[SwitchD] vlan 200
[SwitchD-vlan200] quit
# 配置端口Ten-GigabitEthernet1/0/1允许VLAN 200的报文通过,取消允许VLAN 1通过。
[SwitchD] interface ten-gigabitethernet 1/0/1
[SwitchD-Ten-GigabitEthernet1/0/1] port link-type trunk
[SwitchD-Ten-GigabitEthernet1/0/1] port trunk permit vlan 200
[SwitchD-Ten-GigabitEthernet1/0/1] undo port trunk permit vlan 1
[SwitchD-Ten-GigabitEthernet1/0/1] quit
# 配置Ten-GigabitEthernet1/0/2为Hybrid端口且允许VLAN 30的报文携带VLAN Tag通过、VLAN 200的报文不携带VLAN Tag通过,取消允许VLAN 1通过。
[SwitchD] interface ten-gigabitethernet 1/0/2
[SwitchD-Ten-GigabitEthernet1/0/2] port link-type hybrid
[SwitchD-Ten-GigabitEthernet1/0/2] port hybrid vlan 30 tagged
[SwitchD-Ten-GigabitEthernet1/0/2] port hybrid vlan 200 untagged
[SwitchD-Ten-GigabitEthernet1/0/2] undo port hybrid vlan 1
# 在端口Ten-GigabitEthernet1/0/2上配置1:2 VLAN映射,为VLAN 30报文添加VLAN 200的外层VLAN Tag。
[SwitchD-Ten-GigabitEthernet1/0/2] vlan mapping nest single 30 nested-vlan 200
[SwitchD-Ten-GigabitEthernet1/0/2] quit
# 查看Switch C上的VLAN映射配置信息。
[SwitchC] display vlan mapping
Interface Ten-GigabitEthernet1/0/1:
Outer VLAN Inner VLAN Translated Outer VLAN Translated Inner VLAN
100 10 200 30
显示信息表明2:2 VLAN映射已经正确配置。
· Switch A
#
vlan 10
vlan 100
#
interface Ten-GigabitEthernet1/0/1
port link-type hybrid
port hybrid vlan 10 tagged
port hybrid vlan 100 untagged
vlan mapping nest single 10 nested-vlan 100
#
interface Ten-GigabitEthernet1/0/2
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 100
· Switch B
#
vlan 10
vlan 100
#
interface Ten-GigabitEthernet1/0/1
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 100
#
interface Ten-GigabitEthernet1/0/2
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 100
#
interface Ten-GigabitEthernet1/0/3
port link-type hybrid
port hybrid vlan 10 tagged
port hybrid vlan 100 untagged
vlan mapping nest single 10 nested-vlan 100
#
vlan 100
#
vlan 200
#
interface Ten-GigabitEthernet1/0/1
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 100 200
vlan mapping tunnel 100 10 translated-vlan 200 30
#
interface Ten-GigabitEthernet1/0/2
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 200
#
· Switch D
#
vlan 30
vlan 200
#
interface Ten-GigabitEthernet1/0/1
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 200
#
interface Ten-GigabitEthernet1/0/2
port link-type hybrid
port hybrid vlan 30 tagged
port hybrid vlan 200 untagged
vlan mapping nest single 30 nested-vlan 200
#
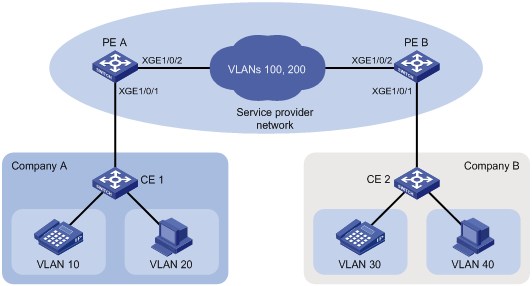
如图8所示,公司A的语音和数据业务分别使用VLAN 10和VLAN 20加以区分,公司B的语音和数据业务则分别使用VLAN 30和VLAN 40加以区分。
现要求通过配置QoS重标记功能,使这两家公司间的语音和数据业务分别利用运营商提供的VLAN 100和VLAN 200实现二层互通。
图8 QoS重标记配置组网图
为了使用户网络的语音和数据报文进入运营商网络后在运营商网络分配的VLAN中传输,在PE A和PE B连接用户网络的端口上配置OoS Nest功能,分别为用户网络的语音和数据报文封装不同的外层VLAN Tag。
因为公司A和公司B为语音和数据报文划分的VLAN不同且需要实现二层通信,所以需要在PE A和PE B的运营商网络侧端口上配置QoS重标记功能修改报文的内层VLAN ID。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
# 创建原始CVLAN 10和CVLAN 20,1:2 VLAN映射封装的外层VLAN 100和VLAN 200以及修改后内层CVLAN 30和CVLAN 40。
<PE_A> system-view
[PE_A] vlan 10
[PE_A-vlan10] quit
[PE_A] vlan 20
[PE_A-vlan20] quit
[PE_A] vlan 100
[PE_A-vlan100] quit
[PE_A] vlan 200
[PE_A-vlan200] quit
[PE_A] vlan 30
[PE_A-vlan30] quit
[PE_A] vlan 40
[PE_A-vlan40] quit
· 配置端口Ten-GigabitEthernet1/0/1
# 配置端口为Hybrid端口。
[PE_A] interface ten-gigabitethernet 1/0/1
[PE_A-Ten-GigabitEthernet1/0/1] port link-type hybrid
# 配置端口允许VLAN 100和VLAN 200的报文不带VLAN Tag通过。
[PE_A-Ten-GigabitEthernet1/0/1] port hybrid vlan 100 200 untagged
# 取消允许VLAN 1通过。
[PE_A-Ten-GigabitEthernet1/0/1] undo port hybrid vlan 1
[PE_A-Ten-GigabitEthernet1/0/1] quit
# 创建流分类规则,将来自VLAN10的报文定义为“A10”类。
[PE_A] traffic classifier A10
[PE_A-classifier-A10] if-match customer-vlan-id 10
[PE_A-classifier-A10] quit
# 定义流行为,为报文封装VLAN100的外层VLAN Tag,流行为命名为“P100”。
[PE_A] traffic behavior P100
[PE_A-behavior-P100] nest top-most vlan 100
[PE_A-behavior-P100] quit
# 与以上配置类似,创建流分类“A20”匹配用户VLAN ID为20的报文,并创建流行为“P200”,为报文封装外层VLAN200的Tag
[PE_A] traffic classifier A20
[PE_A-classifier-A20] if-match customer-vlan-id 20
[PE_A-classifier-A20] quit
[PE_A] traffic behavior P200
[PE_A-behavior-P200] nest top-most vlan 200
[PE_A-behavior-P200] quit
# 创建QoS策略,将流分类“A10”和流行为“P100”进行关联,将流分类“A20”和流行为“P200”关联,策略命名为“qinq”。
[PE_A] qos policy qinq
[PE_A-qospolicy-qinq] classifier A10 behavior P100
[PE_A-qospolicy-qinq] classifier A20 behavior P200
[PE_A-qospolicy-qinq] quit
# 使能端口的基本QinQ功能。
[PE_A-Ten-GigabitEthernet1/0/1] qinq enable
# 在Ten-GigabitEthernet1/0/1端口的接收方向应用“qinq”规则。
[PE_A-Ten-GigabitEthernet1/0/1] qos apply policy qinq inbound
[PE_A-Ten-GigabitEthernet1/0/1] quit
· 配置端口Ten-GigabitEthernet1/0/2
# 配置端口为Trunk端口,且允许VLAN 100和200的报文通过,取消允许VLAN 1通过。
[PE_A] interface ten-gigabitethernet 1/0/2
[PE_A-Ten-GigabitEthernet1/0/2] port link-type trunk
[PE_A-Ten-GigabitEthernet1/0/2] port trunk permit vlan 100 200
[PE_A-Ten-GigabitEthernet1/0/2] undo port trunk permit vlan 1
[PE_A-Ten-GigabitEthernet1/0/2] quit
# 创建流分类规则,将内层VLAN ID是10,外层VLAN ID是100的报文定义为“A100”类。
[PE_A] traffic classifier A100
[PE_A-classifier-A100] if-match customer-vlan-id 10
[PE_A-classifier-A100] if-match service-vlan-id 100
[PE_A-classifier-A100] quit
# 定义流行为,修改报文的内层VLAN ID为30,流行为命名为“T100”。
[PE_A] traffic behavior T100
[PE_A-behavior-T100] remark customer-vlan-id 30
[PE_A-behavior-T100] quit
# 创建流分类规则,将内层VLAN ID是20,外层VLAN ID是200的报文定义为“A200”类。
[PE_A] traffic classifier A200
[PE_A-classifier-A200] if-match customer-vlan-id 20
[PE_A-classifier-A200] if-match service-vlan-id 200
[PE_A-classifier-A200] quit
# 定义流行为,修改报文的内层VLAN ID为40,流行为命名为“T200”。
[PE_A] traffic behavior T200
[PE_A-behavior-T200] remark customer-vlan-id 40
[PE_A-behavior-T200] quit
# 创建QoS策略,将流分类“A100”和流行为“T100”进行关联,流分类“A200”和流行为“T200”进行关联,策略命名为“vlanmapping”。
[PE_A] qos policy vlanmapping
[PE_A-qospolicy-vlanmapping] classifier A100 behavior T100
[PE_A-qospolicy-vlanmapping] classifier A200 behavior T200
[PE_A-qospolicy-vlanmapping] quit
# 在Ten-GigabitEthernet1/0/2端口的发送方向应用“vlanmapping”规则。
[PE_A-Ten-GigabitEthernet1/0/2] qos apply policy vlanmapping outbound
[PE_A-Ten-GigabitEthernet1/0/2] quit
# 创建原始CVLAN 30和CVLAN 40,1:2 VLAN映射封装的外层VLAN 100和VLAN 200以及修改后内层CVLAN 10和CVLAN 20。
<PE_B> system-view
[PE_B] vlan 30
[PE_B-vlan30] quit
[PE_B] vlan 40
[PE_B-vlan40] quit
[PE_B] vlan 100
[PE_B-vlan100] quit
[PE_B] vlan 200
[PE_B-vlan200] quit
[PE_B] vlan 10
[PE_B-vlan10] quit
[PE_B] vlan 20
[PE_B-vlan20] quit
· 配置端口Ten-GigabitEthernet1/0/1
# 配置端口为Hybrid端口。
[PE_B] interface ten-gigabitethernet 1/0/1
[PE_B-Ten-GigabitEthernet1/0/1] port link-type hybrid
# 配置端口允许VLAN 100和VLAN 200的报文不带VLAN Tag通过。
[PE_B-Ten-GigabitEthernet1/0/1] port hybrid vlan 100 200 untagged
# 取消允许VLAN 1通过。
[PE_B-Ten-GigabitEthernet1/0/1] undo port hybrid vlan 1
[PE_B-Ten-GigabitEthernet1/0/1] quit
# 创建流分类规则,将来自VLAN30的报文定义为“A30”类。
[PE_B] traffic classifier A30
[PE_B-classifier-A30] if-match customer-vlan-id 30
[PE_B-classifier-A30] quit
# 定义流行为,为报文封装VLAN100的外层VLAN Tag,流行为命名为“P100”。
[PE_B] traffic behavior P100
[PE_B-behavior-P100] nest top-most vlan 100
[PE_B-behavior-P100] quit
# 与以上配置类似,创建流分类“A40”匹配用户VLAN ID为40的报文,并创建流行为“P200”,为报文封装外层VLAN200的Tag。
[PE_B] traffic classifier A40
[PE_B-classifier-A40] if-match customer-vlan-id 40
[PE_B-classifier-A40] quit
[PE_B] traffic behavior P200
[PE_B-behavior-P200] nest top-most vlan 200
[PE_B-behavior-P200] quit
# 创建QoS策略,将流分类“A30”和流行为“P100”进行关联,将流分类“A40”和流行为“P200”关联,策略命名为“qinq”。
[PE_B] qos policy qinq
[PE_B-qospolicy-qinq] classifier A30 behavior P100
[PE_B-qospolicy-qinq] classifier A40 behavior P200
[PE_B-qospolicy-qinq] quit
# 使能端口的基本QinQ功能。
[PE_B-Ten-GigabitEthernet1/0/1] qinq enable
# 在Ten-GigabitEthernet1/0/1端口的接收方向应用“qinq”规则。
[PE_B-Ten-GigabitEthernet1/0/1] qos apply policy qinq inbound
[PE_B-Ten-GigabitEthernet1/0/1] quit
· 配置端口Ten-GigabitEthernet1/0/2
# 配置端口为Trunk端口,且允许VLAN 100和200的报文通过,取消允许VLAN 1通过。
[PE_B] interface ten-gigabitethernet 1/0/2
[PE_B-Ten-GigabitEthernet1/0/2] port link-type trunk
[PE_B-Ten-GigabitEthernet1/0/2] port trunk permit vlan 100 200
[PE_B-Ten-GigabitEthernet1/0/2] undo port trunk permit vlan 1
[PE_B-Ten-GigabitEthernet1/0/2] quit
# 创建流分类规则,将内层VLAN ID是30,外层VLAN ID是100的报文定义为“A100”类。
[PE_B] traffic classifier A100
[PE_B-classifier-A100] if-match customer-vlan-id 30
[PE_B-classifier-A100] if-match service-vlan-id 100
[PE_B-classifier-A100] quit
# 定义流行为,修改报文的内层VLAN ID为10,流行为命名为“T100”。
[PE_B] traffic behavior T100
[PE_B-behavior-T100] remark customer-vlan-id 10
[PE_B-behavior-T100] quit
# 创建流分类规则,将内层VLAN ID是40,外层VLAN ID是200的报文定义为“A200”类。
[PE_B] traffic classifier A200
[PE_B-classifier-A200] if-match customer-vlan-id 40
[PE_B-classifier-A200] if-match service-vlan-id 200
[PE_B-classifier-A200] quit
# 定义流行为,修改报文的内层VLAN ID为20,流行为命名为“T200”。
[PE_B] traffic behavior T200
[PE_B-behavior-T200] remark customer-vlan-id 20
[PE_B-behavior-T200] quit
# 创建QoS策略,将流分类“A100”和流行为“T100”进行关联,流分类“A200”和流行为“T200”进行关联,策略命名为“vlanmapping”。
[PE_B] qos policy vlanmapping
[PE_B-qospolicy-vlanmapping] classifier A100 behavior T100
[PE_B-qospolicy-vlanmapping] classifier A200 behavior T200
[PE_B-qospolicy-vlanmapping] quit
# 在Ten-GigabitEthernet1/0/2端口的发送方向应用“vlanmapping”规则。
[PE_B] interface ten-gigabitethernet 1/0/2
[PE_B-Ten-GigabitEthernet1/0/2] qos apply policy vlanmapping outbound
[PE_B-Ten-GigabitEthernet1/0/2] quit
配置运营商网络中PE A到PE B之间的路径上的设备端口都允许VLAN 100和VLAN 200的报文携带VLAN Tag通过,且这些端口的MTU值至少为1504字节。
# 显示PE A上端口Ten-GigabitEthernet1/0/1的配置,PE B上的显示信息类似。
[PE_A] interface ten-gigabitethernet 1/0/1
[PE_A-Ten-GigabitEthernet1/0/1] display this
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 100 200 untagged
qinq enable
qos apply policy qinq inbound
#
return
# 显示PE A上Ten-GigabitEthernet1/0/1端口配置的QoS Nest功能,PE B上的显示信息类似。
[PE_A] display qos policy interface ten-gigabitethernet 1/0/1
Interface: Ten-GigabitEthernet1/0/1
Direction: Inbound
Policy: qinq
Classifier: A10
Operator: AND
Rule(s) :
If-match customer-vlan-id 10
Behavior: P100
Nesting:
Nest top-most vlan-id 100
Classifier: A20
Operator: AND
Rule(s) :
If-match customer-vlan-id 20
Behavior: P200
Nesting:
Nest top-most vlan-id 200
# 显示PE A上Ten-GigabitEthernet1/0/2端口配置的QoS重标记功能,PE B上的显示信息类似。
[PE_A] display qos policy interface ten-gigabitethernet 1/0/2
Interface: Ten-GigabitEthernet1/0/2
Direction: Outbound
Policy: vlanmapping
Classifier: A100
Operator: AND
Rule(s) :
If-match customer-vlan-id 10
If-match service-vlan-id 100
Behavior: T100
Marking:
Remark Customer VLAN ID 30
Classifier: A200
Operator: AND
Rule(s) :
If-match customer-vlan-id 20
If-match service-vlan-id 200
Behavior: T200
Marking:
Remark Customer VLAN ID 40
· PE A
#
vlan 10
#
vlan 20
#
vlan 30
#
vlan 40
#
vlan 100
#
vlan 200
#
traffic classifier A10 operator and
if-match customer-vlan-id 10
#
traffic classifier A20 operator and
if-match customer-vlan-id 20
#
traffic classifier A100 operator and
if-match customer-vlan-id 10
if-match service-vlan-id 100
#
traffic classifier A200 operator and
if-match customer-vlan-id 20
if-match service-vlan-id 200
#
traffic behavior P100
nest top-most vlan 100
#
traffic behavior P200
nest top-most vlan 200
#
traffic behavior T100
remark customer-vlan-id 30
#
traffic behavior T200
remark customer-vlan-id 40
#
qos policy qinq
classifier A10 behavior P100
classifier A20 behavior P200
#
qos policy vlanmapping
classifier A100 behavior T100
classifier A200 behavior T200
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 100 200 untagged
qinq enable
qos apply policy qinq inbound
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 100 200
qos apply policy vlanmapping outbound
#
· PE B
#
vlan 10
#
vlan 20
#
vlan 30
#
vlan 40
#
vlan 100
#
vlan 200
#
traffic classifier A30 operator and
if-match customer-vlan-id 30
#
traffic classifier A40 operator and
if-match customer-vlan-id 40
#
traffic classifier A100 operator and
if-match customer-vlan-id 30
if-match service-vlan-id 100
#
traffic classifier A200 operator and
if-match customer-vlan-id 40
if-match service-vlan-id 200
#
traffic behavior P100
nest top-most vlan 100
#
traffic behavior P200
nest top-most vlan 200
#
traffic behavior T100
remark customer-vlan-id 10
#
traffic behavior T200
remark customer-vlan-id 20
#
qos policy qinq
classifier A30 behavior P100
classifier A40 behavior P200
#
qos policy vlanmapping
classifier A100 behavior T100
classifier A200 behavior T200
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port link-type hybrid
undo port hybrid vlan 1
port hybrid vlan 100 200 untagged
qinq enable
qos apply policy qinq inbound
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 100 200
qos apply policy vlanmapping outbound
#
· H3C S6860系列以太网交换机 二层技术-以太网交换配置指导-Release 26xx系列
· H3C S6860系列以太网交换机 二层技术-以太网交换命令参考-Release 26xx系列
· H3C S6860系列以太网交换机 ACL和QoS配置指导-Release 26xx系列
· H3C S6860系列以太网交换机 ACL和QoS命令参考-Release 26xx系列
不同款型规格的资料略有差异, 详细信息请向具体销售和400咨询。H3C保留在没有任何通知或提示的情况下对资料内容进行修改的权利!
