48-BFD典型配置举例
本章节下载: 48-BFD典型配置举例 (497.68 KB)
H3C S6860产品BFD配置举例
Copyright © 2018 新华三技术有限公司 版权所有,保留一切权利。
非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本文档内容的部分或全部,并不得以任何形式传播。
除新华三技术有限公司的商标外,本手册中出现的其它公司的商标、产品标识及商品名称,由各自权利人拥有。
本文档中的信息可能变动,恕不另行通知。
目 录
4.5.4 配置上行设备Device E和Device F到VRRP组虚拟IP的静态路由
9.4.2 在AS 100内配置OSPF功能,保证设备间路由可达
10.4.4 配置BFD功能,并创建和BFD会话关联的Track项11,检测Device B是否可达
本文档介绍了BFD配置举例。
本文档中的配置均是在实验室环境下进行的配置和验证,配置前设备的所有参数均采用出厂时的缺省配置。如果您已经对设备进行了配置,为了保证配置效果,请确认现有配置和以下举例中的配置不冲突。
本文假设您已了解BFD特性、VRRP特性、Track特性以及OSPF、IS-IS等路由协议。
不支持BFD for interface。
如图1所示,区域A和区域B用户所在网络的出口处部署了两台汇聚层设备(Device A和Device B)。
现要求使用VRRP与BFD、Track联动功能,实现以下需求:
· 在Device A和Device B上分别配置两个VRRP备份组,Device A是VRRP备份组1中的Master设备,Device B是VRRP备份组2中的Master设备;
· 在正常情况下,区域A的用户将VRRP备份组1作为缺省网关,通过Device A进行数据转发,区域B用户将VRRP备份组2作为缺省网关,通过Device B进行数据转发。当一台网关设备出现故障时,另一台网关设备能够迅速承担受影响区域内主机流量的转发任务;
· 当网关设备Device A(Device B)自身出现故障,或其上行接口出现故障时,局域网中的主机可以通过另一台设备网关设备Device B(Device A)继续通信,避免通信中断;当Device A(Device B)故障恢复后,继续承担网关功能;
· 当Device A或Device B的下行链路出现故障时,局域网中的主机通过接入设备L2 Switch A 或L2 Switch B的Ten-GigabitEthernet1/0/2端口将数据转发给网关设备继续通信,避免通信中断;当Device A或Device B的下行链路故障恢复后,继续由L2 Switch A 或L2 Switch B的Ten-GigabitEthernet1/0/1端口将数据发送给网关设备。
图1 VRRP与BFD、Track联动配置组网图
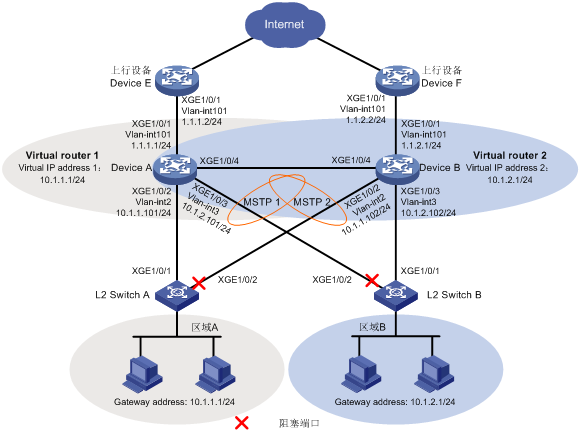
· 为了实现不同区域中用户数据流的负载分担,需要在Device A和Device B上分别创建两个VRRP备份组,并配置区域A内的主机都将VRRP备份组1作为网关,区域B内的主机都将VRRP备份组2作为网关;
· 为使Device A优先被选举为VRRP备份组1的Master设备,需要为其在VRRP备份组1中配置较高的优先级;为使Device B优先被选举为VRRP备份组2的Master设备,需要为其在VRRP备份组2中配置较高的优先级;
· 配置两个VRRP备份组都工作在抢占模式,以保证原Master设备故障恢复后,能再次抢占成为Master;
· 通过Device A与Device B上配置BFD功能监视其上行接口的状态,当监测到其上行接口故障时,Device A或Device B的优先级会自动降低指定的数额,使VRRP备份组1内Device B的优先级高于Device A,或VRRP备份组2内Device A的优先级高于Device B,从而实现主备切换;
· 为了使Device A上不同VLAN的VRRP通告报文和BFD报文能够和Device B相互传输,需要配置Device A与Device B相连的接口均允许VLAN 2和VLAN 3通过;
· 利用MSTP多实例技术避免二层环路。将VLAN 2映射到MSTP实例1中;将VLAN 3映射到MSTP实例2中。保证正常情况下,MSTP实例1中的流量通过L2 Switch A 的Ten-GigabitEthernet1/0/1端口转发,MSTP实例2中的流量通过L2 Switch B的Ten-GigabitEthernet1/0/1端口转发。
· 为了避免MSTP功能阻塞Device A或Device B的上行接口Ten-GigabitEthernet1/0/1,需要关闭此接口的STP功能。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
· 请务必保证备份组中的所有设备上配置的VRRP版本一致,否则备份组无法正常工作。
· 为了避免对端发送大量的ICMP重定向报文造成网络拥塞,建议不要将BFD echo报文的源IP地址配置为属于该设备任何一个接口所在网段。
· 建议将备份组的虚拟IP地址和备份组中设备下行接口的IP地址配置为同一网段,否则可能导致局域网内的主机无法访问外部网络。
(1) 配置Device A各接口的IP地址
<DeviceA> system-view
[DeviceA] vlan 101
[DeviceA-vlan101] port ten-gigabitethernet 1/0/1
[DeviceA-vlan101] quit
[DeviceA] interface vlan-interface 101
[DeviceA-Vlan-interface101] ip address 1.1.1.1 24
[DeviceA-Vlan-interface101] quit
(2) 请参考以上方法配置4.1 图1中其它接口的IP地址,配置步骤这里省略
(1) 配置Device A
# 与Device B直连的Ten-Gigabitethernet 1/0/4配置为trunk端口,不允许VLAN 1的报文通过,允许VLAN 2和VLAN 3的报文通过。
[DeviceA] interface ten-gigabitethernet 1/0/4
[DeviceA-Ten-GigabitEthernet1/0/4] port link-type trunk
[DeviceA-Ten-GigabitEthernet1/0/4] undo port trunk permit vlan 1
[DeviceA-Ten-GigabitEthernet1/0/4] port trunk permit vlan 2 to 3
[DeviceA-Ten-GigabitEthernet1/0/4] port trunk pvid vlan 2
[DeviceA-Ten-GigabitEthernet1/0/4] quit
(2) 配置Device B
# 与Device A直连的Ten-Gigabitethernet1/0/4配置为trunk端口,不允许VLAN 1的报文通过,允许VLAN 2和VLAN 3的报文通过。
[DeviceB] interface ten-gigabitethernet 1/0/4
[DeviceB-Ten-GigabitEthernet1/0/4] port link-type trunk
[DeviceB-Ten-GigabitEthernet1/0/4] undo port trunk permit vlan 1
[DeviceB-Ten-GigabitEthernet1/0/4] port trunk permit vlan 2 to 3
[DeviceB-Ten-GigabitEthernet1/0/4] port trunk pvid vlan 2
[DeviceB-Ten-GigabitEthernet1/0/4] quit
(1) 配置Device A Ten-GigabitEthernet1/0/1端口关闭STP功能
[DeviceA] interface ten-gigabitethernet 1/0/1
[DeviceA-Ten-GigabitEthernet1/0/1] undo stp enable
[DeviceA-Ten-GigabitEthernet1/0/1] quit
(2) 配置Device B Ten-GigabitEthernet1/0/1端口关闭STP功能
[DeviceB] interface ten-gigabitethernet 1/0/1
[DeviceB-Ten-GigabitEthernet1/0/1] undo stp enable
[DeviceB-Ten-GigabitEthernet1/0/1] quit
(1) 配置Device E
# 配置Device E到VRRP备份组1和VRRP备份组2的虚拟IP地址的静态路由。
<DeviceE> system-view
[DeviceE] ip route-static 10.1.1.0 255.255.255.0 1.1.1.1
[DeviceE] ip route-static 10.1.2.0 255.255.255.0 1.1.1.1
(2) 配置Device F
# 配置Device F到VRRP备份组1和VRRP备份组2的虚拟IP地址的静态路由。
<DeviceE> system-view
[DeviceF] ip route-static 10.1.1.0 255.255.255.0 1.1.2.1
[DeviceF] ip route-static 10.1.2.0 255.255.255.0 1.1.2.1
(1) 配置Device A
# 配置VRRP备份组1的虚拟IP地址为10.1.1.1,抢占延时为5s。并且VRRP备份组1中Device A的优先级为110,高于Device B,成为VRRP备份组1的Master。
[DeviceA] interface vlan-interface 2
[DeviceA-Vlan-interface2] vrrp vrid 1 virtual-ip 10.1.1.1
[DeviceA-Vlan-interface2] vrrp vrid 1 priority 110
[DeviceA-Vlan-interface2] vrrp vrid 1 preempt-mode delay 500
[DeviceA-Vlan-interface2] quit
# 配置VRRP备份组2的虚拟IP地址为10.1.2.1,抢占延时为5秒。
[DeviceA] interface vlan-interface 3
[DeviceA-Vlan-interface3] vrrp vrid 2 virtual-ip 10.1.2.1
[DeviceA-Vlan-interface3] vrrp vrid 2 preempt-mode delay 500
[DeviceA–Vlan-interface3] quit
(2) 配置Device B
# 配置VRRP备份组1的虚拟IP地址为10.1.1.1,抢占延时为5秒。
[DeviceB] interface vlan-interface 2
[DeviceB-Vlan-interface2] vrrp vrid 1 virtual-ip 10.1.1.1
[DeviceB-Vlan-interface2] vrrp vrid 1 preempt-mode delay 500
[DeviceB-Vlan-interface2] quit
# 配置VRRP备份组2的虚拟IP地址为10.1.2.1,抢占延时为5s。并且VRRP备份组2中Device B的优先级为110,高于Device A,成为VRRP备份组2的Master。
[DeviceB] interface vlan-interface 3
[DeviceB-Vlan-interface3] vrrp vrid 2 virtual-ip 10.1.2.1
[DeviceB-Vlan-interface3] vrrp vrid 2 priority 110
[DeviceB-Vlan-interface3] vrrp vrid 2 preempt-mode delay 500
[DeviceB–Vlan-interface3] quit
(1) 配置Device A
# 配置BFD echo报文方式的Source IP,IP地址可以任意指定,不要与实际接口地址相同。
[DeviceA] bfd echo-source-ip 10.10.10.10
(2) 配置Device B
# 配置BFD echo报文方式的Source IP,IP地址可以任意指定,不要与实际接口地址相同。
[DeviceB] bfd echo-source-ip 11.11.11.11
(1) 配置Device A
# 创建和BFD会话关联的Track项1,检测上行设备Device E是否可达。
[DeviceA] track 1 bfd echo interface vlan-interface 101 remote ip 1.1.1.2 local ip 1.1.1.1
# 配置备份组1监视Track项1的状态,当Track项状态为Negative时,Device A在VRRP备份组1中的优先级减小20,低于Device B,以便Device B抢占成为Master。
[DeviceA] interface vlan-interface 2
[DeviceA-Vlan-interface2] vrrp vrid 1 track 1 priority reduced 20
[DeviceA-Vlan-interface2] quit
(2) 配置Device B
# 创建和BFD会话关联的Track项1,检测上行设备Device F是否可达。
[DeviceB] track 1 bfd echo interface vlan-interface 101 remote ip 1.1.2.2 local ip 1.1.2.1
# 配置备份组2监视Track项1的状态,当Track项状态为Negative时,Device B在VRRP备份组2中的优先级减小20,低于Device A,以便Device A抢占成为Master。
[DeviceB] interface vlan-interface 3
[DeviceB-Vlan-interface3] vrrp vrid 2 track 1 priority reduced 20
[DeviceB-Vlan-interface3] quit
(1) 配置Device A
[DeviceA] stp region-configuration
[DeviceA-mst-region] region-name vrrp
[DeviceA-mst-region] instance 1 vlan 2
[DeviceA-mst-region] instance 2 vlan 3
[DeviceA-mst-region] active region-configuration
[DeviceA-mst-region] quit
[DeviceA] stp instance 1 root primary
[DeviceA] stp instance 2 root secondary
[DeviceA] stp global enable
(2) 配置Device B
[DeviceB] stp region-configuration
[DeviceB-mst-region] region-name vrrp
[DeviceB-mst-region] instance 1 vlan 2
[DeviceB-mst-region] instance 2 vlan 3
[DeviceB-mst-region] active region-configuration
[DeviceB-mst-region] quit
[DeviceB] stp instance 2 root primary
[DeviceB] stp instance 1 root secondary
[DeviceB] stp global enable
(3) 配置L2 Switch A
<DeviceC> system-view
[SwitchA] stp region-configuration
[SwitchA-mst-region] region-name vrrp
[SwitchA-mst-region] instance 1 vlan 2
[SwitchA-mst-region] active region-configuration
[SwitchA-mst-region] quit
[SwitchA] stp global enable
(4) 配置L2 Switch B
<SwitchB> system-view
[SwitchB] stp region-configuration
[SwitchB-mst-region] region-name vrrp
[SwitchB-mst-region] instance 2 vlan 3
[SwitchB-mst-region] active region-configuration
[SwitchB-mst-region] quit
(1) 网关设备Device A、Device B和链路均正常工作时,验证局域网内主机是否可以与外部网络通信
# 检查区域A的主机到目的端1.1.1.2是否可达。
<host A> ping 1.1.1.2
PING 1.1.1.2 (1.1.1.2): 56 data bytes
56 bytes from 1.1.1.2: seq=0 ttl=128 time=22.43 ms
56 bytes from 1.1.1.2: seq=1 ttl=128 time=7.17 ms
56 bytes from 1.1.1.2: seq=2 ttl=128 time=8.91 ms
56 bytes from 1.1.1.2: seq=3 ttl=128 time=7.45 ms
56 bytes from 1.1.1.2: seq=4 ttl=128 time=9.11 ms
--- 1.1.1.2 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 7.17/11.01/22.43 ms
# 检查区域B的主机到目的端1.1.2.2是否可达。
<host C> ping 1.1.2.2
PING 1.1.2.2 (1.1.2.2): 56 data bytes
56 bytes from 1.1.2.2: seq=0 ttl=128 time=22.43 ms
56 bytes from 1.1.2.2: seq=1 ttl=128 time=7.17 ms
56 bytes from 1.1.2.2: seq=2 ttl=128 time=8.91 ms
56 bytes from 1.1.2.2: seq=3 ttl=128 time=7.45 ms
56 bytes from 1.1.2.2: seq=4 ttl=128 time=9.11 ms
--- 1.1.2.2 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 7.17/11.01/22.43 ms
以上显示信息表示网关设备Device A、Device B和链路均正常工作时,区域A的主机和区域B的主机都可以访问Internet。
# 查看Device A上的BFD会话。
[DeviceA] display bfd session
Total Session Num: 1 Up Session Num: 1 Init Mode: Active
IPv4 session working in control packet mode:
LD/RD SourceAddr DestAddr State Holdtime Interface
257/129 1.1.1.1 1.1.1.2 Up 500ms Vlan101
以上显示信息表示BFD会话已经建立。
# 显示Device A上备份组的详细信息。
[DeviceA] display vrrp verbose
IPv4 Virtual Router Information:
Running mode : Standard
Total number of virtual routers : 2
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 500
Auth Type : None
Virtual IP : 10.1.1.1
Virtual MAC : 0000-5e00-0101
Master IP : 10.1.1.101
VRRP Track Information:
Track Object : 1 State : Positive Pri Reduced : 20
Interface Vlan-interface3
VRID : 2 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 500
Become Master : 3600ms left
Auth Type : None
Virtual IP : 10.1.2.1
Virtual MAC : 0000-5e00-0101
Master IP : 10.1.2.102
# 显示Device B上备份组的详细信息。
[DeviceB] display vrrp verbose
IPv4 Virtual Router Information:
Running mode : Standard
Total number of virtual routers : 2
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 500
Become Master : 3100ms left
Auth Type : None
Virtual IP : 10.1.1.1
Virtual MAC : 0000-5e00-0102
Master IP : 10.1.1.101
Interface Vlan-interface3
VRID : 2 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 500
Auth Type : None
Virtual IP : 10.1.2.1
Virtual MAC : 0000-5e00-0102
Master IP : 10.1.2.102
VRRP Track Information:
Track Object : 1 State : Positive Pri Reduced : 20
以上显示信息表示在备份组1中Device A为Master,Device B为Backup,缺省网关为10.1.1.1/24的主机通过Device A访问Internet;备份组2中Device A为Backup,Device B为Master,缺省网关为10.1.2.1/24的主机通过Device B访问Internet。
(2) 当Device A监视的上行设备或上行链路状态为down时,验证局域网内主机是否可以与外部网络通信
# 检查区域A的主机到目的端1.1.1.2是否可达。
<host A> ping 1.1.1.2
PING 1.1.1.2 (1.1.1.2): 56 data bytes
56 bytes from 1.1.1.2: seq=0 ttl=128 time=22.43 ms
56 bytes from 1.1.1.2: seq=1 ttl=128 time=7.17 ms
56 bytes from 1.1.1.2: seq=2 ttl=128 time=8.91 ms
56 bytes from 1.1.1.2: seq=3 ttl=128 time=7.45 ms
56 bytes from 1.1.1.2: seq=4 ttl=128 time=9.11 ms
--- 1.1.1.2 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 7.17/11.01/22.43 ms
# 检查区域B的主机到目的端1.1.1.2是否可达。
<host C> ping 1.1.2.2
PING 1.1.2.2 (1.1.2.2): 56 data bytes
56 bytes from 1.1.2.2: seq=0 ttl=128 time=22.43 ms
56 bytes from 1.1.2.2: seq=1 ttl=128 time=7.17 ms
56 bytes from 1.1.2.2: seq=2 ttl=128 time=8.91 ms
56 bytes from 1.1.2.2: seq=3 ttl=128 time=7.45 ms
56 bytes from 1.1.2.2: seq=4 ttl=128 time=9.11 ms
--- 1.1.2.2 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 7.17/11.01/22.43 ms
以上显示信息表示当Device A监视的上行设备或上行链路状态为down时,区域A的主机和区域B的主机都可以访问Internet。
# 查看Device A上的BFD会话。
[DeviceA] display bfd session
Total Session Num: 1 Up Session Num: 0 Init Mode: Active
IPv4 session working in control packet mode:
LD/RD SourceAddr DestAddr State Holdtime Interface
257/129 1.1.1.1 1.1.1.2 Down / Vlan101
以上显示信息表示BFD会话已经终止。
# 显示Device B上备份组的详细信息。
[DeviceB] display vrrp verbose
IPv4 Virtual Router Information:
Running mode : Standard
Total number of virtual routers : 2
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 500
Auth Type : None
Virtual IP : 10.1.1.1
Virtual MAC : 0000-5e00-0101
Master IP : 10.1.1.102
Interface Vlan-interface3
VRID : 2 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 500
Auth Type : None
Virtual IP : 10.1.2.1
Virtual MAC : 0000-5e00-0102
Master IP : 10.1.2.102
VRRP Track Information:
Track Object : 1 State : Positive Pri Reduced : 20
以上显示信息表示当Device A监视的上行设备或上行链路状态为down时,Device B抢占成为VRRP备份组1的Master,VLAN 2内的主机通过Device B与外界通信。
# 当上行设备或上行链路状态恢复为UP后,查看Device A上的BFD会话。
[DeviceA] display bfd session
Total Session Num: 1 Up Session Num: 1 Init Mode: Active
IPv4 session working in control packet mode:
LD/RD SourceAddr DestAddr State Holdtime Interface
257/129 1.1.1.1 1.1.1.2 Up 1000ms Vlan101
以上显示信息表示BFD会话已经恢复。
# 当上行设备或上行链路状态恢复为UP后,显示Device A上备份组的详细信息。
[DeviceA] display vrrp verbose
IPv4 Virtual Router Information:
Running mode : Standard
Total number of virtual routers : 2
Interface Vlan-interface2
VRID : 1 Adver Timer : 100
Admin Status : Up State : Master
Config Pri : 110 Running Pri : 110
Preempt Mode : Yes Delay Time : 500
Auth Type : None
Virtual IP : 10.1.1.1
Virtual MAC : 0000-5e00-0101
Master IP : 10.1.1.101
VRRP Track Information:
Track Object : 1 State : Positive Pri Reduced : 20
Interface Vlan-interface3
VRID : 2 Adver Timer : 100
Admin Status : Up State : Backup
Config Pri : 100 Running Pri : 100
Preempt Mode : Yes Delay Time : 500
Become Master : 3550ms left
Auth Type : None
Virtual IP : 10.1.2.1
Virtual MAC : 0000-5e00-0101
Master IP : 10.1.2.102
以上显示信息表示当上行设备或上行链路状态恢复为UP后,Device A在VRRP备份组1中恢复为原来的优先级并抢占成为该备份组的Master,VLAN 2内的主机通过Device A与外界通信。
· Device A:
#
bfd echo-source-ip 10.10.10.10
#
vlan 2 to 3
#
vlan 101
#
stp region-configuration
region-name vrrp
instance 1 vlan 2
instance 2 vlan 3
active region-configuration
#
stp instance 1 root primary
stp instance 2 root secondary
stp global enable
#
interface Vlan-interface2
ip address 10.1.1.101 255.255.255.0
vrrp vrid 1 virtual-ip 10.1.1.1
vrrp vrid 1 priority 110
vrrp vrid 1 preempt-mode delay 500
vrrp vrid 1 track 1 priority reduced 20
#
interface Vlan-interface3
ip address 10.1.2.101 255.255.255.0
vrrp vrid 2 virtual-ip 10.1.2.1
vrrp vrid 2 preempt-mode delay 500
#
interface Vlan-interface101
ip address 1.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 101
undo stp enable
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 2
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 3
#
interface Ten-GigabitEthernet1/0/4
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 2 to 3
port trunk pvid vlan 2
#
track 1 bfd echo interface Vlan-interface101 remote ip 1.1.1.2 local ip 1.1.1.1
· Device B:
#
bfd echo-source-ip 11.11.11.11
#
vlan 2 to 3
#
vlan 101
#
stp region-configuration
region-name vrrp
instance 1 vlan 2
instance 2 vlan 3
active region-configuration
#
stp instance 1 root secondary
stp instance 2 root primary
stp global enable
#
interface Vlan-interface2
ip address 10.1.1.102 255.255.255.0
vrrp vrid 1 virtual-ip 10.1.1.1
vrrp vrid 1 preempt-mode delay 500
#
interface Vlan-interface3
ip address 10.1.2.102 255.255.255.0
vrrp vrid 2 virtual-ip 10.1.2.1
vrrp vrid 2 priority 110
vrrp vrid 2 preempt-mode delay 500
vrrp vrid 2 track 1 priority reduced 20
#
interface Vlan-interface101
ip address 1.1.2.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 101
undo stp enable
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 2
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 3
#
interface Ten-GigabitEthernet1/0/4
port link-mode bridge
port link-type trunk
undo port trunk permit vlan 1
port trunk permit vlan 2 to 3
port trunk pvid vlan 2
#
track 1 bfd echo interface Vlan-interface101 remote ip 1.1.2.2 local ip 1.1.2.1
· L2 Switch A :
#
vlan 2
#
stp region-configuration
region-name vrrp
instance 1 vlan 2
active region-configuration
#
stp global enable
#
interface GigabitEthernet1/0/1
port link-mode bridge
port access vlan 2
#
interface GigabitEthernet1/0/2
port link-mode bridge
port access vlan 2
· L2 Switch B:
#
vlan 3
#
stp region-configuration
region-name vrrp
instance 2 vlan 3
active region-configuration
#
stp global enable
#
interface GigabitEthernet1/0/1
port link-mode bridge
port access vlan 3
#
interface GigabitEthernet1/0/2
port link-mode bridge
port access vlan 3
· Device E:
#
vlan 101
#
interface Vlan-interface101
ip address 1.1.1.2 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 101
#
ip route-static 10.1.1.0 255.255.255.0 1.1.1.1
ip route-static 10.1.2.0 255.255.255.0 1.1.1.1
#
· Device F:
#
vlan 101
#
interface Vlan-interface101
ip address 1.1.2.2 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 101
#
ip route-static 10.1.1.0 255.255.255.0 1.1.2.1
ip route-static 10.1.2.0 255.255.255.0 1.1.2.1
#
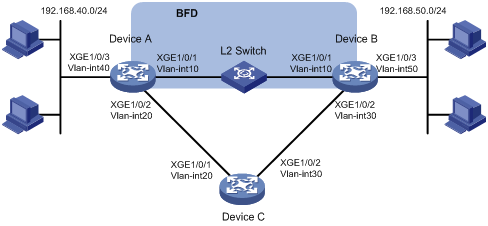
某公司内部网络如图2所示,从Device A到Device B有两条转发路径,下一跳分别为Device B和Device C。由于Device A和Device B之间物理距离较远,通过一个二层交换机L2 Switch作为中继。假设Device B不支持BFD,要求在Device A上使用静态路由与BFD联动技术,实现当Device B与二层交换机L2 Switch之间的链路出现故障(如链路down)时,Device A能快速感知,并将流量切换到Device C的链路上。
图2 静态路由与BFD联动配置组网图
|
设备 |
接口 |
IP地址 |
设备 |
接口 |
IP地址 |
|
Device A |
Vlan-int10 |
192.168.10.101/24 |
Device B |
Vlan-int10 |
192.168.10.102/24 |
|
|
Vlan-int20 |
192.168.20.101/24 |
|
Vlan-int30 |
192.168.30.101/24 |
|
|
Vlan-int40 |
192.168.40.101/24 |
|
Vlan-int50 |
192.168.50.101/24 |
|
Device C |
Vlan-int20 |
192.168.20.102/24 |
|
|
|
|
|
Vlan-int30 |
192.168.30.102/24 |
|
|
|
· 由于需要两端设备均支持BFD,才能够使用控制报文方式,本例中Device B不支持BFD,在Device A上配置的BFD功能仅能使用echo报文方式。
· echo报文方式下必须配置echo报文的源IP地址。IP地址可以任意指定,不需要与实际接口地址对应。建议不要将echo报文的源IP地址配置为属于该设备任何一个接口所在网段,避免对端发送大量的ICMP重定向报文造成网络拥塞。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
(1) 配置Device A各接口的IP地址
<DeviceA> system-view
[DeviceA] vlan 10
[DeviceA-vlan10] port ten-gigabitethernet 1/0/1
[DeviceA-vlan10] quit
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] ip address 192.168.10.101 24
[DeviceA-Vlan-interface10] quit
(2) 请参考以上方法配置5.1 图2中其它接口的IP地址,配置步骤这里省略
(1) 配置Device A
# 配置Device A到192.168.50.0/24网段的静态路由,Device A到Device B的流量优先走Device A –> L2 Switch–> Device B链路,当此链路发生故障时,流量切换到Device A –> Device C–> Device B链路上。
[DeviceA] ip route-static 192.168.50.0 24 vlan-interface 10 192.168.10.102 bfd echo-packet
[DeviceA] ip route-static 192.168.50.0 24 vlan-interface 20 192.168.20.102 preference 65
(2) 配置Device B
# 配置Device B到192.168.40.0/24网段的静态路由,Device B到Device A的流量优先走Device B –> L2 Switch–> Device A链路,当此链路发生故障时,流量切换到Device B –> Device C–> Device A链路上。
[DeviceB] ip route-static 192.168.40.0 24 vlan-interface 10 192.168.10.101
[DeviceB] ip route-static 192.168.40.0 24 vlan-interface 30 192.168.30.102 preference 65
(3) 配置Device C
# 配置Device C到192.168.40.0/24和192.168.50.0/24网段的静态路由。
[DeviceC] ip route-static 192.168.40.0 24 vlan-interface 20 192.168.20.101
[DeviceC] ip route-static 192.168.50.0 24 vlan-interface 30 192.168.30.101
# 静态路由支持的BFD会话方式为echo报文方式,该方式下必须配置BFD echo报文的源IP地址。IP地址可以任意指定,不需要与实际接口地址对应。建议不要将BFD echo报文的源IP地址配置为属于该设备任何一个接口所在网段。
[DeviceA] bfd echo-source-ip 10.10.10.10
# 配置接口接收BFD echo报文的最小时间间隔为100ms,单跳BFD检测时间倍数为3。
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] bfd min-echo-receive-interval 100
[DeviceA-Vlan-interface10] bfd detect-multiplier 3
[DeviceA-Vlan-interface10] quit
(1) Device A和Device B设备及之间的链路均正常工作时
# 在Device A查看静态路由信息。
[DeviceA] display ip routing-table protocol static
Summary Count : 2
Static Routing table Status : <Active>
Summary Count : 2
Destination/Mask Proto Pre Cost NextHop Interface
192.168.50.0/24 Static 60 0 192.168.10.102 Vlan10
Static Routing table Status : <Inactive>
Summary Count : 0
以上显示信息表示Device A经过L2 Switch到达Device B。
# 查看BFD会话。
[DeviceA] display bfd session
Total Session Num: 1 Up Session Num: 1 Init Mode: Active
IPv4 session working in control packet mode:
LD/RD SourceAddr DestAddr State Holdtime Interface
67 192.168.10.101 192.168.10.102 Up 300ms Vlan10
以上显示信息表示BFD会话已经创建。
(2) Device B与L2 Switch之间的链路出现故障时
# 查看静态路由。
[DeviceA] display ip routing-table protocol static
Summary Count : 1
Static Routing table Status : <Active>
Summary Count : 1
Destination/Mask Proto Pre Cost NextHop Interface
192.168.50.0/24 Static 65 0 192.168.20.102 Vlan20
Static Routing table Status : <Inactive>
Summary Count : 0
以上显示信息表示Device A经过Device C到达Device B。
· Device A:
#
bfd echo-source-ip 10.10.10.10
#
vlan 10
#
vlan 20
#
vlan 40
#
interface Vlan-interface10
ip address 192.168.10.101 255.255.255.0
bfd min-echo-receive-interval 100
bfd detect-multiplier 3
#
interface Vlan-interface20
ip address 192.168.20.101 255.255.255.0
#
interface Vlan-interface40
ip address 192.168.40.101 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 20
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 40
#
ip route-static 192.168.50.0 24 Vlan-interface10 192.168.10.102 bfd echo-packet
ip route-static 192.168.50.0 24 Vlan-interface20 192.168.20.102 preference 65
#
· Device B:
#
vlan 10
#
vlan 30
#
vlan 50
#
interface Vlan-interface10
ip address 192.168.10.102 255.255.255.0
#
interface Vlan-interface30
ip address 192.168.30.101 255.255.255.0
#
interface Vlan-interface50
ip address 192.168.50.101 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 50
#
ip route-static 192.168.40.0 24 Vlan-interface10 192.168.10.101
ip route-static 192.168.40.0 24 Vlan-interface30 192.168.30.102 preference 65
#
· Device C:
#
vlan 20
#
vlan 30
#
interface Vlan-interface30
ip address 192.168.20.102 255.255.255.0
#
interface Vlan-interface30
ip address 192.168.30.102 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 20
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
ip route-static 192.168.40.0 24 Vlan-interface20 192.168.20.101
ip route-static 192.168.50.0 24 Vlan-interface30 192.168.30.101
#
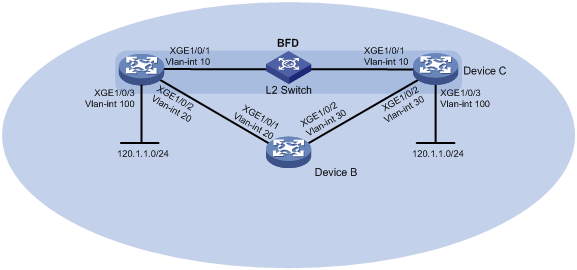
如图3所示,某公司通过一台二层交换机作为中继将两个相距较远的部门连接。Device A、Device B、Device C上运行RIP,建立RIP邻居关系,保证网络层相互可达。
公司希望在Device A上使用RIP与BFD联动技术,实现当Device C与二层交换机之间的链路出现故障(如链路down)时,BFD能够快速感知并通告RIP协议。
已知Device C不支持BFD功能,公司希望使用RIP与BFD联动技术,采用BFD echo报文方式实现当Device A或Device C与二层交换机之间的链路出现故障时,BFD能够快速感知并通告RIP协议。
现要求通过在Device A和Device C上配置RIP与BFD联动功能,实现:
· 监测通过L2 Switch通信的链路;
· 当链路出现故障时设备能够快速感知并通告RIP协议,快速切换到Device B链路进行通信。
图3 RIP与BFD联动配置组网图
|
设备 |
接口 |
IP地址 |
设备 |
接口 |
IP地址 |
|
Device A |
Vlan-int10 |
10.1.0.101/24 |
Device B |
Vlan-int20 |
192.168.0.102/24 |
|
|
Vlan-int20 |
192.168.0.101/24 |
|
Vlan-int30 |
13.1.1.101/24 |
|
|
Vlan-int100 |
120.1.1.1/24 |
|
|
|
|
Device C |
Vlan-int10 |
10.1.0.102/24 |
|
|
|
|
|
Vlan-int30 |
13.1.1.102/24 |
|
|
|
|
|
Vlan-int100 |
121.1.1.1/24 |
|
|
|
· 由于需要两端设备均支持BFD,才能够使用控制报文方式,本例中Device C不支持BFD,在Device A上配置的BFD功能仅能使用echo报文方式。
· echo报文方式下必须配置echo报文的源IP地址。IP地址可以任意指定,不需要与实际接口地址对应。建议不要将echo报文的源IP地址配置为属于该设备任何一个接口所在网段,避免对端发送大量的ICMP重定向报文造成网络拥塞。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
(1) 配置Device A各接口的IP地址
<DeviceA> system-view
[DeviceA] vlan 10
[DeviceA-vlan10] port ten-gigabitethernet 1/0/1
[DeviceA-vlan10] quit
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] ip address 10.1.0.101 24
[DeviceA-Vlan-interface10] quit
(2) 请参考以上方法配置6.1 图3中其它接口的IP地址,配置步骤这里省略
(1) 配置Device A
# 配置Device A的RIP基本功能,引入直连路由,并使能RIP的BFD功能。
<DeviceA> system-view
[DeviceA] rip 1
[DeviceA-rip-1] version 2
[DeviceA-rip-1] undo summary
[DeviceA-rip-1] network 10.1.0.0
[DeviceA-rip-1] network 192.168.0.0
[DeviceA-rip-1] import-route direct
[DeviceA-rip-1] quit
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] rip bfd enable
[DeviceA-Vlan-interface10] quit
(2) 配置Device B
# 配置Device B的RIP基本功能,引入直连路由。
<DeviceB> system-view
[DeviceB] rip 1
[DeviceB-rip-1] version 2
[DeviceB-rip-1] undo summary
[DeviceB-rip-1] network 192.168.0.0
[DeviceB-rip-1] network 13.1.1.0
[DeviceB-rip-1] import-route direct
[DeviceB-rip-1] quit
(3) 配置Device C
# 配置Device C的RIP基本功能,引入直连路由。
<DeviceC> system-view
[DeviceC] rip 1
[DeviceC-rip-1] version 2
[DeviceC-rip-1] undo summary
[DeviceC-rip-1] network 10.1.0.0
[DeviceC-rip-1] network 13.1.1.0
[DeviceC-rip-1] import-route direct
[DeviceC-rip-1] quit
# RIP支持的BFD会话方式为echo报文方式,该方式下必须配置BFD echo报文的源IP地址。IP地址可以任意指定,不需要与实际接口地址对应。建议不要将BFD echo报文的源IP地址配置为属于该设备任何一个接口所在网段。
[DeviceA] bfd echo-source-ip 11.11.11.11
# 配置接口接收BFD echo报文的最小时间间隔为100ms,单跳BFD检测时间倍数为3。
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] bfd min-echo-receive-interval 100
[DeviceA-Vlan-interface10] bfd detect-multiplier 3
[DeviceA-Vlan-interface10] quit
# 查看Device A上BFD会话信息,显示BFD会话已被创建,且状态为Up。
[DeviceA] display bfd session verbose
Total Session Num: 1 Up Session Num: 1 Init Mode: Active
IPv4 session working in control packet mode:
Local Discr: 2049
Source IP: 10.1.0.101 Destination IP: 10.1.0.102
Session State: Up Interface: Vlan-interface10
Hold Time: 300ms Act Tx Inter: 100ms
Min Rx Inter: 100ms Detect Inter: 300ms
Rx Count: 0 Tx Count: 910
Connect Type: Direct Running Up for: 00:00:46
Detect Mode: Async Slot: 0
Protocol: RIP
Version: 1
Diag Info: No Diagnostic
# 查看Device A上学到的路由121.1.1.0/24,可以看到Device A经过L2 Switch到达Device C。
<DeviceA> display ip routing-table 121.1.1.0 24 verbose
Summary Count : 1
Destination: 121.1.1.0/24
Protocol: RIP Process ID: 1
SubProtID: 0x1 Age: 04h20m37s
Cost: 1 Preference: 100
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NBRID: 0x26000002 LastAs: 0
AttrID: 0xffffffff Neighbor: 10.1.0.102
Flags: 0x1008c OrigNextHop: 10.1.0.102
Label: NULL RealNextHop: 10.1.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface10
BkTunnel ID: Invalid BkInterface: N/A
# 当Device C和二层交换机之间的链路发生故障,BFD快速检测到链路发生变化并立刻通告RIP。
%Oct 9 18:42:17:650 2013 Device A BFD/5/BFD_CHANGE_FSM: -MDC=1;Sess[10.1.0.101/10.1.0.102, LD/RD:2049/2049, Interface:Vlan10, SessType:Echo, LinkType:INET] , Sta: UP-> DOWN, Diag:1
# 查看Device A上学到的路由121.1.1.0/24,可以看到Device A经过Device B到达Device C。
<DeviceA> display ip routing-table 121.1.1.0 24 verbose
Summary Count : 1
Destination: 121.1.1.0/24
Protocol: RIP Process ID: 2
SubProtID: 0x1 Age: 04h20m37s
Cost: 2 Preference: 100
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NBRID: 0x26000002 LastAs: 0
AttrID: 0xffffffff Neighbor: 192.168.0.102
Flags: 0x1008c OrigNextHop: 192.168.0.102
Label: NULL RealNextHop: 192.168.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface20
BkTunnel ID: Invalid BkInterface: N/A
· Device A:
#
bfd echo-source-ip 11.11.11.11
#
rip 1
undo summary
version 2
network 10.0.0.0
network 192.168.0.0
import-route direct
#
vlan 10
#
vlan 20
#
vlan 100
#
interface Vlan-interface10
ip address 10.1.0.101 255.255.255.0
bfd min-transmit-interval 100
bfd min-receive-interval 100
bfd detect-multiplier 3
#
interface Vlan-interface20
ip address 192.168.0.101 255.255.255.0
#
interface Vlan-interface100
ip address 120.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 20
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 100
#
· Device B:
#
rip 1
undo summary
version 2
network 192.168.0.0
network 13.1.1.0
import-route direct
#
vlan 20
#
vlan 30
#
interface Vlan-interface20
ip address 192.168.0.102 255.255.255.0
#
interface Vlan-interface30
ip address 13.1.1.101 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 20
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
· Device C:
#
rip 1
undo summary
version 2
network 10.1.0.0
network 13.1.1.0
import-route direct
#
vlan 10
#
vlan 30
#
vlan 100
#
interface Vlan-interface10
ip address 10.1.0.102 255.255.255.0
#
interface Vlan-interface30
ip address 13.1.1.102 255.255.255.0
#
interface Vlan-interface100
ip address 121.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 100
#
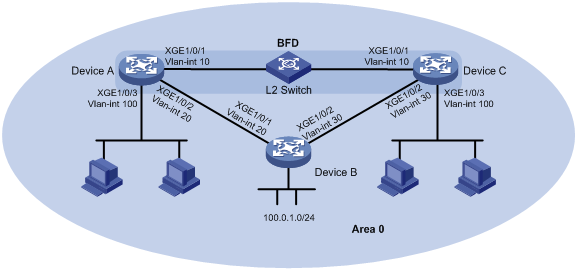
如图4所示,某公司通过一台二层交换机作为中继将两个相距较远的部门连接。Device A、Device B、Device C上运行OSPF,建立OSPF邻居关系,保证网络层相互可达。
已知Device A和Device C都支持BFD功能,要求使用OSPF与BFD联动技术,采用BFD控制报文方式实现当Device A或Device C与二层交换机之间的链路出现故障(如链路down)时,BFD能够快速感知并通告OSPF协议。
现要求通过在Device A和Device C上配置OSPF与BFD联动功能,实现:
· 监测通过L2 Switch通信的链路;
· 当链路出现故障时设备能够快速感知并通告OSPF协议,快速切换到Device B链路进行通信。
图4 OSPF与BFD联动配置组网图
|
设备 |
接口 |
IP地址 |
设备 |
接口 |
IP地址 |
|
Device A |
Vlan-int10 |
10.1.0.101/24 |
Device B |
Vlan-int20 |
192.168.0.102/24 |
|
|
Vlan-int20 |
192.168.0.101/24 |
|
Vlan-int30 |
13.1.1.101/24 |
|
|
Vlan-int100 |
120.1.1.1/24 |
|
|
|
|
Device C |
Vlan-int10 |
10.1.0.102/24 |
|
|
|
|
|
Vlan-int30 |
13.1.1.102/24 |
|
|
|
|
|
Vlan-int100 |
121.1.1.1/24 |
|
|
|
Device A和Device C都支持BFD,可以使用BFD控制报文方式,通信双方至少要有一方运行在主动模式才能成功建立起BFD会话。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
(1) 配置Device A各接口的IP地址
<DeviceA> system-view
[DeviceA] vlan 10
[DeviceA-vlan10] port ten-gigabitethernet 1/0/1
[DeviceA-vlan10] quit
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] ip address 10.1.0.101 24
[DeviceA-Vlan-interface10] quit
(2) 请参考以上方法配置7.1 图4中其它接口的IP地址,具体配置步骤略
(1) 配置Device A
# 配置Device A的OSPF基本功能,并使能OSPF的BFD功能。
[DeviceA] ospf
[DeviceA-ospf-1] area 0
[DeviceA-ospf-1-area-0.0.0.0] network 10.1.0.0 0.0.0.255
[DeviceA-ospf-1-area-0.0.0.0] network 192.168.0.0 0.0.0.255
[DeviceA-ospf-1-area-0.0.0.0] network 120.1.1.0 0.0.0.255
[DeviceA-ospf-1-area-0.0.0.0] quit
[DeviceA-ospf-1] quit
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] ospf bfd enable
[DeviceA-Vlan-interface10] quit
(2) 配置Device B
# 配置Device B的OSPF基本功能。
[DeviceB] ospf
[DeviceB-ospf-1] area 0
[DeviceB-ospf-1-area-0.0.0.0] network 192.168.0.0 0.0.0.255
[DeviceB-ospf-1-area-0.0.0.0] network 13.1.1.0 0.0.0.255
[DeviceB-ospf-1-area-0.0.0.0] quit
[DeviceB-ospf-1] quit
(3) 配置Device C
# 配置Device C的OSPF基本功能,并使能OSPF的BFD功能。
[DeviceC] ospf
[DeviceC-ospf-1] area 0
[DeviceC-ospf-1-area-0.0.0.0] network 10.1.0.0 0.0.0.255
[DeviceC-ospf-1-area-0.0.0.0] network 13.1.1.0 0.0.0.255
[DeviceC-ospf-1-area-0.0.0.0] network 121.1.1.0 0.0.0.255
[DeviceC-ospf-1-area-0.0.0.0] quit
[DeviceC-ospf-1] quit
[DeviceC] interface vlan-interface 10
[DeviceC-Vlan-interface10] ospf bfd enable
[DeviceC-Vlan-interface10] quit
# 配置BFD会话建立前的运行模式为主动模式(缺省为主动模式)。
[DeviceA] bfd session init-mode active
# 配置发送和接收单跳BFD控制报文的最小时间间隔都为100ms,单跳BFD检测时间倍数为3。
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] bfd min-transmit-interval 100
[DeviceA-Vlan-interface10] bfd min-receive-interval 100
[DeviceA-Vlan-interface10] bfd detect-multiplier 3
[DeviceA-Vlan-interface10] quit
(2) 配置Device C
# 配置BFD会话建立前的运行模式为主动模式(缺省为主动模式)。
[DeviceC] bfd session init-mode active
# 配置发送和接收单跳BFD控制报文的最小时间间隔都为100ms,单跳BFD检测时间倍数为3。
[DeviceC] interface vlan-interface 10
[DeviceC-Vlan-interface10] bfd min-transmit-interval 100
[DeviceC-Vlan-interface10] bfd min-receive-interval 100
[DeviceC-Vlan-interface10] bfd detect-multiplier 3
[DeviceC-Vlan-interface10] quit
# 检查Device A连接的主机host A(120.1.1.2)到Device C连接的主机host C(121.1.1.2)是否可达。
<host A> ping 121.1.1.2
PING 121.1.1.2 (121.1.1.2): 56 data bytes
56 bytes from 121.1.1.2: seq=0 ttl=128 time=22.43 ms
56 bytes from 121.1.1.2: seq=1 ttl=128 time=7.17 ms
56 bytes from 121.1.1.2: seq=2 ttl=128 time=8.91 ms
56 bytes from 121.1.1.2: seq=3 ttl=128 time=7.45 ms
56 bytes from 121.1.1.2: seq=4 ttl=128 time=9.11 ms
--- 121.1.1.2 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 7.17/11.01/22.43 ms
# 查看Device A 上OSPF邻居信息,显示Device A和Device C已建立OSPF邻居关系。
[DeviceA] display ospf peer verbose
OSPF Process 1 with Router ID 2.2.2.2
Neighbors
Area 0.0.0.0 interface 10.1.0.101(Vlan-interface10)'s neighbors
Router ID: 1.1.1.1 Address: 10.1.0.102 GR State: Normal
State: Full Mode: Nbr is slave Priority: 1
DR: 10.1.0.101 BDR: 10.1.0.102 MTU: 0
Options is 0x42 (-|O|-|-|-|-|E|-)
Dead timer due in 39 sec
Neighbor is up for 00:09:01
Authentication Sequence: [ 0 ]
Neighbor state change count: 5
BFD status: Enabled(Control mode)
# 查看 Device A和Device C上BFD会话信息,显示BFD会话已被创建,且状态为Up。
[DeviceA] display bfd session verbose
Total Session Num: 1 Up Session Num: 1 Init Mode: Active
IPv4 session working in control packet mode:
Local Discr: 2049 Remote Discr: 2049
Source IP: 10.1.0.101 Destination IP: 10.1.0.102
Session State: Up Interface: Vlan-interface10
Min Tx Inter: 100ms Act Tx Inter: 100ms
Min Rx Inter: 100ms Detect Inter: 300ms
Rx Count: 536 Tx Count: 536
Connect Type: Direct Running Up for: 00:04:48
Hold Time: 300ms Auth mode: None
Detect Mode: Async Slot: 0
Protocol: OSPF
Version: 1
Diag Info: No Diagnostic
[DeviceC] display bfd session verbose
Total Session Num: 1 Up Session Num: 1 Init Mode: Active
IPv4 session working in control packet mode:
Local Discr: 2049 Remote Discr: 2049
Source IP: 10.1.0.102 Destination IP: 10.1.0.101
Session State: Up Interface: Vlan-interface10
Min Tx Inter: 100ms Act Tx Inter: 100ms
Min Rx Inter: 100ms Detect Inter: 300ms
Rx Count: 3971 Tx Count: 3776
Connect Type: Direct Running Up for: 00:06:52
Hold Time: 300ms Auth mode: None
Detect Mode: Async Slot: 0
Protocol: OSPF
Version: 1
Diag Info: No Diagnostic
# 在Device A上查看121.1.1.0/24的路由信息,可以看出Device A和Device C是通过L2 Switch进行通信的。
<DeviceA> display ip routing-table 121.1.1.0 verbose
Summary Count : 1
Destination: 121.1.1.0/24
Protocol: OSPF
Process ID: 1
SubProtID: 0x1 Age: 04h20m37s
Cost: 1 Preference: 10
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x26000002 LastAs: 0
AttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x1008c OrigNextHop: 10.1.0.102
Label: NULL RealNextHop: 10.1.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface10
BkTunnel ID: Invalid BkInterface: N/A
FtnIndex: 0x0 TrafficIndex: N/A
Connector: N/A PathID: 0x0
# 当Device C和二层交换机之间的链路状态变为Down,BFD快速检测到链路发生变化并立刻通告OSPF。
%Oct 9 15:22:23:154 2013 DeviceC BFD/5/BFD_CHANGE_FSM: -MDC=1; Sess[10.1.0.1
02/10.1.0.101, LD/RD:2049/2049, Interface:Vlan10, SessType:Ctrl, LinkType:INET] ,
Sta: UP-> DOWN, Diag: 1
%Oct 9 15:22:23:155 2013 DeviceC OSPF/5/OSPF_NBR_CHG: -MDC=1; OSPF 1 Neighbor 10.1
.0.101(Vlan-interface10) from FULL to DOWN.
# 在Device A上查看121.1.1.0/24的路由信息,可以看出Device A和Device C已经切换到Device B进行通信。
<DeviceA> display ip routing-table 121.1.1.0 verbose
Summary Count : 1
Destination: 121.1.1.0/24
Protocol: OSPF
Process ID: 1
SubProtID: 0x1 Age: 04h20m37s
Cost: 2 Preference: 10
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x26000002 LastAs: 0
AttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x1008c OrigNextHop: 192.168.0.102
Label: NULL RealNextHop: 192.168.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface20
BkTunnel ID: Invalid BkInterface: N/A
FtnIndex: 0x0 TrafficIndex: N/A
Connector: N/A PathID: 0x0
· Device A:
#
ospf 1
area 0.0.0.0
network 10.1.0.0 0.0.0.255
network 120.1.1.0 0.0.0.255
network 192.168.0.0 0.0.0.255
#
vlan 10
#
vlan 20
#
vlan 100
#
interface Vlan-interface10
ip address 10.1.0.101 255.255.255.0
ospf bfd enable
bfd min-transmit-interval 100
bfd min-receive-interval 100
bfd detect-multiplier 3
#
interface Vlan-interface20
ip address 192.168.0.101 255.255.255.0
#
interface Vlan-interface100
ip address 120.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 20
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 100
#
· Device B:
#
ospf 1
area 0.0.0.0
network 13.1.1.0 0.0.0.255
network 192.168.0.0 0.0.0.255
#
vlan 20
#
vlan 30
#
interface Vlan-interface20
ip address 192.168.0.102 255.255.255.0
#
interface Vlan-interface30
ip address 13.1.1.101 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 20
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
· Device C:
#
ospf 1
area 0.0.0.0
network 10.1.0.0 0.0.0.255
network 13.1.1.0 0.0.0.255
network 121.1.1.0 0.0.0.255
#
vlan 10
#
vlan 30
#
vlan 100
#
interface Vlan-interface10
ip address 10.1.0.102 255.255.255.0
ospf bfd enable
bfd min-transmit-interval 100
bfd min-receive-interval 100
bfd detect-multiplier 3
#
interface Vlan-interface30
ip address 13.1.1.102 255.255.255.0
#
interface Vlan-interface100
ip address 121.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 100
#
如图5所示,某公司通过一台二层交换机作为中继将两个相距较远的部门连接。Device A、Device B、Device C上运行IS-IS,建立IS-IS邻居关系,保证网络层相互可达。
已知Device A和Device C都支持BFD功能,公司希望使用IS-IS与BFD联动技术,采用BFD控制报文方式实现当Device A或Device C与二层交换机之间的链路出现故障(如链路down)时,BFD能够快速感知并通告IS-IS协议。
现要求通过在Device A和Device C上配置IS-IS与BFD联动功能,实现:
· 监测通过L2 Switch通信的链路;
· 当链路出现故障时设备能够快速感知并通告IS-IS协议,快速切换到Device B链路进行通信。
图5 IS-IS与BFD联动配置组网图
|
设备 |
接口 |
IP地址 |
设备 |
接口 |
IP地址 |
|
Device A |
Vlan-int10 |
10.1.0.101/24 |
Device B |
Vlan-int20 |
192.168.0.102/24 |
|
|
Vlan-int20 |
192.168.0.101/24 |
|
Vlan-int30 |
13.1.1.101/24 |
|
|
Vlan-int100 |
120.1.1.1/24 |
|
|
|
|
Device C |
Vlan-int10 |
10.1.0.102/24 |
|
|
|
|
|
Vlan-int30 |
13.1.1.102/24 |
|
|
|
|
|
Vlan-int100 |
121.1.1.1/24 |
|
|
|
Device A和Device C都支持BFD,可以使用BFD控制报文方式,通信双方至少要有一方运行在主动模式才能成功建立起BFD会话。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
(1) 配置Device A各接口的IP地址
<DeviceA> system-view
[DeviceA] vlan 10
[DeviceA-vlan10] port ten-gigabitethernet 1/0/1
[DeviceA-vlan10] quit
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] ip address 10.1.0.101 24
[DeviceA-Vlan-interface10] quit
(2) 请参考以上方法配置图5中其它接口的IP地址,配置步骤这里省略
(1) 配置Device A
# 配置Device A的IS-IS基本功能,并使能IS-IS的BFD功能。
[DeviceA] isis
[DeviceA-isis-1] network-entity 10.0000.0000.0001.00
[DeviceA-isis-1] quit
[DeviceA] interface vlan-interface 20
[DeviceA-Vlan-interface20] isis enable
[DeviceA-Vlan-interface20] quit
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] isis enable
[DeviceA-Vlan-interface10] isis bfd enable
[DeviceA-Vlan-interface10] quit
(2) 配置Device B
# 配置Device B的IS-IS基本功能。
[DeviceB] isis
[DeviceB-isis-1] network-entity 10.0000.0000.0003.00
[DeviceB-isis-1] quit
[DeviceB] interface vlan-interface 20
[DeviceB-Vlan-interface20] isis enable
[DeviceB-Vlan-interface20] quit
[DeviceB] interface vlan-interface 30
[DeviceB-Vlan-interface30] isis enable
[DeviceB-Vlan-interface30] quit
(3) 配置Device C
# 配置Device C的IS-IS基本功能,并使能IS-IS的BFD功能。
[DeviceC] isis
[DeviceC-isis-1] network-entity 10.0000.0000.0002.00
[DeviceC-isis-1] quit
[DeviceC] interface vlan-interface 10
[DeviceC-Vlan-interface10] isis enable
[DeviceC-Vlan-interface10] isis bfd enable
[DeviceC-Vlan-interface10] quit
[DeviceC] interface vlan 30
[DeviceC-Vlan-interface30] isis enable
[DeviceC-Vlan-interface30] quit
# 配置BFD会话建立前的运行模式为主动模式(缺省为主动模式)。
[DeviceA] bfd session init-mode active
# 配置发送和接收单跳BFD控制报文的最小时间间隔都为100ms,单跳BFD检测时间倍数为3。
[DeviceA] interface vlan-interface 10
[DeviceA-Vlan-interface10] bfd min-transmit-interval 100
[DeviceA-Vlan-interface10] bfd min-receive-interval 100
[DeviceA-Vlan-interface10] bfd detect-multiplier 3
[DeviceA-Vlan-interface10] quit
(2) 配置Device C
# 配置BFD会话建立前的运行模式为主动模式(缺省为主动模式)。
[DeviceC] bfd session init-mode active
# 配置发送和接收单跳BFD控制报文的最小时间间隔都为100ms,单跳BFD检测时间倍数为3。
[DeviceC] interface vlan 10
[DeviceC-Vlan-interface10] bfd min-transmit-interval 100
[DeviceC-Vlan-interface10] bfd min-receive-interval 100
[DeviceC-Vlan-interface10] bfd detect-multiplier 3
[DeviceC-Vlan-interface10] quit
# 查看Device A上IS-IS邻居信息,显示Device A和Device C已建立IS-IS邻居关系。
[DeviceA] display isis peer verbose
Peer information for IS-IS(1)
-----------------------------
System ID: 0000.0000.0002
Interface: Vlan10 Circuit Id: 0000.0000.0002.01
State: Up HoldTime: 6s Type: L1(L1L2) PRI: 64
Area address(es): 00
Peer IP address(es): 10.1.0.102
Peer local circuit ID: 1
Peer circuit SNPA address: ce9d-d91d-d100
Uptime: 00:01:19
Adj protocol: IPv4
Graceful Restart capable
Restarting signal: No
Suppress adjacency advertisement: No
Local topology:
0
Remote topology:
0
# 查看Device A和Device C上BFD会话信息,显示BFD会话已被创建,且状态为Up。
[DeviceA] display bfd session verbose
Total Session Num: 1 Up Session Num: 1 Init Mode: Active
IPv4 session working in control packet mode:
Local Discr: 2049 Remote Discr: 2049
Source IP: 10.1.0.101 Destination IP: 10.1.0.102
Session State: Up Interface: Vlan-interface10
Min Tx Inter: 100ms Act Tx Inter: 100ms
Min Rx Inter: 100ms Detect Inter: 300ms
Rx Count: 3 Tx Count: 3
Connect Type: Direct Running Up for: 00:06:09
Hold Time: 300ms Auth mode: None
Detect Mode: Async Slot: 0
Protocol: ISIS_BR_L1/ISIS_BR_L2
Version: 1
Diag Info: No Diagnostic
[DeviceC] display bfd session verbose
Total Session Num: 1 Up Session Num: 1 Init Mode: Active
IPv4 session working in control packet mode:
Local Discr: 2049 Remote Discr: 2049
Source IP: 10.1.0.102 Destination IP: 10.1.0.101
Session State: Up Interface: Vlan-interface10
Min Tx Inter: 100ms Act Tx Inter: 100ms
Min Rx Inter: 100ms Detect Inter: 300ms
Rx Count: 3 Tx Count: 3
Connect Type: Direct Running Up for: 00:07:10
Hold Time: 300ms Auth mode: None
Detect Mode: Async Slot: 0
Protocol: ISIS_BR_L1/ISIS_BR_L2
Version: 1
Diag Info: No Diagnostic
# 在Device A上查看121.1.1.0/24的路由信息,可以看出Device A和Device C是通过L2 Switch进行通信的。
<DeviceA> display ip routing-table 121.1.1.0 verbose
Summary Count : 1
Destination: 121.1.1.0/24
Protocol: isis
Process ID: 1
SubProtID: 0x1 Age: 04h20m37s
Cost: 20 Preference: 15
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x2 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x26000002 LastAs: 0
AttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x1008c OrigNextHop: 10.1.0.102
Label: NULL RealNextHop: 10.1.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface10
BkTunnel ID: Invalid BkInterface: N/A
FtnIndex: 0x0 TrafficIndex: N/A
Connector: N/A PathID: 0x0
# 当Device C和二层交换机之间的链路Down了,BFD快速检测到链路发生变化并立刻通告IS-IS。
%Oct 9 16:11:24:163 2013 DeviceC BFD/5/BFD_CHANGE_FSM: -MDC=1; Sess[10.1.0.102/10.1.0.101, LD/RD:2049/2049, Interface:Vlan10, SessType:Ctrl, LinkType:INET] , S
ta: UP-> DOWN, Diag: 1
%Oct 9 16:11:24:164 2013 DeviceC ISIS/5/ISIS_NBR_CHG: -MDC=1; IS-IS 1, Level-1 adj
acency 0000.0000.0001 (Vlan-interface10), state change to: DOWN.
%Oct 9 16:11:24:164 2013 DeviceC ISIS/5/ISIS_NBR_CHG: -MDC=1; IS-IS 1, Level-2 adj
acency 0000.0000.0001 (Vlan-interface10), state change to: DOWN.
# 在Device A上查看121.1.1.0/24的路由信息,可以看出Device A和Device C已经切换到Device B进行通信。
<DeviceA> display ip routing-table 121.1.1.0 verbose
Summary Count : 1
Destination: 121.1.1.0/24
Protocol: OSPF
Process ID: 1
SubProtID: 0x1 Age: 04h20m37s
Cost: 2 Preference: 10
IpPre: N/A QosLocalID: N/A
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x26000002 LastAs: 0
AttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x1008c OrigNextHop: 192.168.0.102
Label: NULL RealNextHop: 192.168.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface20
BkTunnel ID: Invalid BkInterface: N/A
FtnIndex: 0x0 TrafficIndex: N/A
Connector: N/A PathID: 0x0
· Device A:
#
isis 1
network-entity 10.0000.0000.0001.00
#
vlan 10
#
vlan 20
#
vlan 100
#
interface Vlan-interface10
ip address 10.1.0.101 255.255.255.0
isis enable 1
isis bfd enable
bfd min-transmit-interval 100
bfd min-receive-interval 100
bfd detect-multiplier 3
#
interface Vlan-interface20
ip address 192.168.0.101 255.255.255.0
isis enable 1
#
interface Vlan-interface100
ip address 120.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 20
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 100
#
· Device B:
#
isis 1
network-entity 10.0000.0000.0003.00
#
vlan 20
#
vlan 30
#
interface Vlan-interface20
ip address 192.168.0.102 255.255.255.0
isis enable 1
#
interface Vlan-interface30
ip address 13.1.1.101 255.255.255.0
isis enable 1
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 20
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
· Device C:
#
isis 1
network-entity 10.0000.0000.0002.00
#
vlan 10
#
vlan 30
#
vlan 100
#
interface Vlan-interface10
ip address 10.1.0.102 255.255.255.0
isis enable 1
isis bfd enable
bfd min-transmit-interval 100
bfd min-receive-interval 100
bfd detect-multiplier 3
#
interface Vlan-interface30
ip address 13.1.1.102 255.255.255.0
isis enable 1
#
interface Vlan-interface100
ip address 121.1.1.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 10
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 30
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 100
#
如图6所示,某公司的两个部门相距较远,Device A和Device F分别作为这两个部门的出口设备,现通过部署BGP,使两个部门可以进行业务通信。已知Device B和Device D都支持BFD功能,公司希望使用BGP与BFD联动技术,采用BFD控制报文方式检测AS 200与AS 300之间通信的主链路状态,实现当Device B或Device D之间的链路出现故障(如链路down)时,BFD能够快速感知并通告BGP协议。具体要求如下:
· 在AS 100内使用OSPF作为IGP;
· 配置Device B<->Device C<->Device D链路作为主链路,负责转发Device A和Device F之间的流量,并采用BFD控制报文的方式检测主链路;
· 当主链路发生故障时,BFD能够快速检测并通告BGP协议,使得迅速切换到Device B<->Device E<->Device D这条路径进行通信。
图6 BGP与BFD联动配置组网图
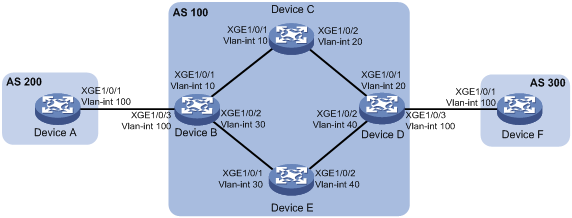
|
设备 |
接口 |
IP地址 |
设备 |
接口 |
IP地址 |
|
Device A |
Vlan-int100 |
120.1.0.1/24 |
Device D |
Vlan-int20 |
10.2.0.101/24 |
|
Device B |
Vlan-int10 |
10.1.0.101/24 |
|
Vlan-int40 |
13.1.1.101/24 |
|
|
Vlan-int30 |
192.168.0.101/24 |
|
Vlan-int100 |
120.2.0.2/24 |
|
|
Vlan-int100 |
120.1.0.2/24 |
Device E |
Vlan-int30 |
192.168.0.102/24 |
|
Device C |
Vlan-int10 |
10.1.0.102/24 |
|
Vlan-int40 |
13.1.1.102/24 |
|
|
Vlan-int20 |
10.2.0.102/24 |
Device F |
Vlan-int100 |
120.2.0.1/24 |
· Device B和Device D都支持BFD,可以使用BFD控制报文方式,通信双方至少要有一方运行在主动模式才能成功建立起BFD会话。
· 为了使Device B<->Device C<->Device D成为主链路,需要通过路由策略配置其路由开销低于链路Device B<->Device E<->Device D的路由开销。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
设备上各接口IP地址的配置步骤这里省略。
(1) 配置Device B
[DeviceB] ospf
[DeviceB-ospf-1] import-route direct
[DeviceB-ospf-1] area 0
[DeviceB-ospf-1-area-0.0.0.0] network 10.1.0.0 0.0.0.255
[DeviceB-ospf-1-area-0.0.0.0] network 192.168.0.0 0.0.0.255
[DeviceB-ospf-1-area-0.0.0.0] quit
[DeviceB-ospf-1] quit
(2) 配置Device C
[DeviceC] ospf
[DeviceC-ospf-1] area 0
[DeviceC-ospf-1-area-0.0.0.0] network 10.1.0.0 0.0.0.255
[DeviceC-ospf-1-area-0.0.0.0] network 10.2.0.0 0.0.0.255
[DeviceC-ospf-1-area-0.0.0.0] quit
[DeviceC-ospf-1] quit
(3) 配置Device D
[DeviceD] ospf
[DeviceD-ospf-1] import-route direct
[DeviceD-ospf-1] area 0
[DeviceD-ospf-1-area-0.0.0.0] network 10.2.0.0 0.0.0.255
[DeviceD-ospf-1-area-0.0.0.0] network 13.1.1.0 0.0.0.255
[DeviceD-ospf-1-area-0.0.0.0] quit
[DeviceD-ospf-1] quit
(4) 配置Device E
[DeviceE] ospf
[DeviceE-ospf-1] area 0
[DeviceE-ospf-1-area-0.0.0.0] network 13.1.1.0 0.0.0.255
[DeviceE-ospf-1-area-0.0.0.0] network 192.168.0.0 0.0.0.255
[DeviceE-ospf-1-area-0.0.0.0] quit
[DeviceE-ospf-1] quit
(1) 配置Device A
# 启动BGP,指定本地AS号为200。
[DeviceA] bgp 200
[DeviceA-bgp-default] router-id 1.1.1.1
# 配置Device A和Device B建立EBGP连接。
[DeviceA-bgp-default] peer 120.1.0.2 as-number 100
# 创建BGP IPv4单播地址族,并进入BGP IPv4单播地址族视图。
[DeviceA-bgp-default] address-family ipv4 unicast
# 在BGP IPv4单播地址族视图下,将本地路由表中到达120.1.0.0/24网段的路由添加到BGP路由表中。
[DeviceA-bgp-default-ipv4] network 120.1.0.0 255.255.255.0
# 使能Device A与对等体120.1.0.2交换IPv4单播路由信息的能力。
[DeviceA-bgp-default-ipv4] peer 120.1.0.2 enable
[DeviceA-bgp-default-ipv4] quit
(2) 配置Device B
# 启动BGP,指定本地AS号为100。
[DeviceB] bgp 100
[DeviceB-bgp-default] router-id 2.2.2.2
# 配置Device B和Device A建立EBGP连接。
[DeviceB-bgp-default] peer 120.1.0.1 as-number 200
# 配置Device B和Device D建立IBGP连接。
[DeviceB-bgp-default] peer 10.2.0.101 as-number 100
[DeviceB-bgp-default] peer 13.1.1.101 as-number 100
# 创建BGP IPv4单播地址族,并进入BGP IPv4单播地址族视图。
[DeviceB-bgp-default] address-family ipv4 unicast
# 使能Device B与对等体10.2.0.101交换IPv4单播路由信息的能力。
[DeviceB-bgp-default-ipv4] peer 10.2.0.101 enable
# 在BGP IPv4单播地址族视图下,配置向对等体10.2.0.101发布BGP路由时,将下一跳属性修改为自身的地址。
[DeviceB-bgp-default-ipv4] peer 10.2.0.101 next-hop-local
# 使能Device B与对等体13.1.1.101交换IPv4单播路由信息的能力。
[DeviceB-bgp-default-ipv4] peer 13.1.1.101 enable
# 在BGP IPv4单播地址族视图下,配置向对等体13.1.1.101发布BGP路由时,将下一跳属性修改为自身的地址。
[DeviceB-bgp-default-ipv4] peer 13.1.1.101 next-hop-local
# 使能Device B与对等体120.1.0.1交换IPv4单播路由信息的能力。
[DeviceB-bgp-default-ipv4] peer 120.1.0.1 enable
[DeviceB-bgp-default-ipv4] quit
(3) 配置Device D
# 启动BGP,指定本地AS号为100。
[DeviceD] bgp 100
[DeviceD-bgp-default] router-id 4.4.4.4
# 配置Device D和Device B建立IBGP连接。
[DeviceD-bgp-default] peer 10.1.0.101 as-number 100
[DeviceD-bgp-default] peer 192.168.0.101 as-number 100
# 配置Device D和Device F建立EBGP连接。
[DeviceD-bgp-default] peer 120.2.0.1 as-number 300
# 创建BGP IPv4单播地址族,并进入BGP IPv4单播地址族视图。
[DeviceD-bgp-default] address-family ipv4 unicast
# 使能Device D与对等体10.1.0.101交换IPv4单播路由信息的能力。
[DeviceD-bgp-default-ipv4] peer 10.1.0.101 enable
# 在BGP IPv4单播地址族视图下,配置向对等体10.1.0.101发布BGP路由时,将下一跳属性修改为自身的地址。
[DeviceD-bgp-default-ipv4] peer 10.1.0.101 next-hop-local
# 使能Device D与对等体192.168.0.101交换IPv4单播路由信息的能力。
[DeviceD-bgp-default-ipv4] peer 192.168.0.101 enable
# 在BGP IPv4单播地址族视图下,配置向对等体192.168.0.101发布BGP路由时,将下一跳属性修改为自身的地址。
[DeviceD-bgp-default-ipv4] peer 192.168.0.101 next-hop-local
# 使能Device D与对等体120.2.0.1交换IPv4单播路由信息的能力。
[DeviceD-bgp-default-ipv4] peer 120.2.0.1 enable
[DeviceD-bgp-default-ipv4] quit
(4) 配置Device F
#启动BGP,指定本地AS号为300。
[DeviceF] bgp 300
[DeviceF-bgp-default] router-id 6.6.6.6
# 配置Device F和Device D建立EBGP连接。
[DeviceF-bgp-default] peer 120.2.0.2 as-number 100
# 创建BGP IPv4单播地址族,并进入BGP IPv4单播地址族视图。
[DeviceF-bgp-default] address-family ipv4 unicast
# 在BGP IPv4单播地址族视图下,将本地路由表中到达120.2.0.0/24网段的路由添加到BGP路由表中。
[DeviceF-bgp-default-ipv4] network 120.2.0.0 255.255.255.0
# 使能Device F与对等体120.2.0.2交换IPv4单播路由信息的能力。
[DeviceF-bgp-default-ipv4] peer 120.2.0.2 enable
[DeviceF-bgp-default-ipv4] quit
(1) 配置Device B
# 创建ACL 2000,允许源IP地址为120.1.0.0/24的报文通过。
[DeviceB] acl basic 2000
[DeviceB-acl-ipv4-basic-2000] rule permit source 120.1.0.0 0.0.0.255
[DeviceB-acl-ipv4-basic-2000] quit
# 配置向对等体10.2.0.101发布的路由设置本地优先级为200,并配置IBGP路由优先级为100。
[DeviceB] route-policy local-pre permit node 10
[DeviceB-route-policy-local-pre] if-match ip address acl 2000
[DeviceB-route-policy-local-pre] apply local-preference 200
[DeviceB-route-policy-local-pre] quit
[DeviceB] bgp 100
[DeviceB-bgp-default] address-family ipv4 unicast
[DeviceB-bgp-default-ipv4] peer 10.2.0.101 route-policy local-pre export
[DeviceB-bgp-default-ipv4] preference 255 100 130
[DeviceB-bgp-default-ipv4] quit
(2) 配置Device D
# 创建ACL 2000,允许源IP地址为120.2.0.0/24的报文通过。
[DeviceD] acl basic 2000
[DeviceD-acl-ipv4-basic-2000] rule permit source 120.2.0.0 0.0.0.255
[DeviceD-acl-ipv4-basic-2000] quit
# 配置向对等体10.1.0.101发布的路由设置本地优先级为200,并配置IBGP路由优先级为100。
[DeviceD] route-policy local-pre permit node 10
[DeviceD-route-policy-local-pre] if-match ip address acl 2000
[DeviceD-route-policy-local-pre] apply local-preference 200
[DeviceD-route-policy-local-pre] quit
[DeviceD] bgp 100
[DeviceD-bgp-default] address-family ipv4 unicast
[DeviceD-bgp-default-ipv4] peer 10.1.0.101 route-policy local-pre export
[DeviceD-bgp-default-ipv4] preference 255 100 130
[DeviceD-bgp-default-ipv4] quit
(1) 配置Device B
[DeviceB] bgp 100
[DeviceB-bgp-default] peer 10.2.0.101 bfd
[DeviceB-bgp-default] quit
(2) 配置Device D
[DeviceD] bgp 100
[DeviceD-bgp-default] peer 10.1.0.101 bfd
[DeviceD-bgp-default] quit
# 从Device A上ping Device F的IP地址,可以互通。
[DeviceA] ping 120.2.0.1
Ping 120.2.0.1 (120.2.0.1): 56 data bytes, press CTRL_C to break
56 bytes from 120.2.0.1: icmp_seq=0 ttl=252 time=1.189 ms
56 bytes from 120.2.0.1: icmp_seq=1 ttl=252 time=1.095 ms
56 bytes from 120.2.0.1: icmp_seq=2 ttl=252 time=1.086 ms
56 bytes from 120.2.0.1: icmp_seq=3 ttl=252 time=1.097 ms
56 bytes from 120.2.0.1: icmp_seq=4 ttl=252 time=1.089 ms
--- Ping statistics for 120.2.0.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.086/1.111/1.189/0.039 ms
# 在Device B上通过命令display bgp peer查看BGP对等体信息,可以看到Device B与Device D建立IBGP连接,Device B与Device A建立EBGP连接,且均处于Established状态。
[DeviceB] display bgp peer ipv4
BGP local router ID: 2.2.2.2
Local AS number: 100
Total number of peers: 3 Peers in established state: 3
Peer AS MsgRcvd MsgSent OutQ PrefRcv Up/Down State
10.2.0.101 100 6 4 0 1 00:00:56 Established
13.1.1.101 100 6 5 0 1 00:00:56 Established
120.1.0.1 200 6 5 0 1 00:00:56 Established
# 查看Device B上BFD会话信息,显示BFD会话已被创建,且状态为Up。
[DeviceB] display bfd session verbose
Total Session Num: 1 Up Session Num: 0 Init Mode: Active
IPv4 session working in control packet mode:
Local Discr: 2049 Remote Discr: 0
Source IP: 10.1.0.101 Destination IP: 10.2.0.101
Session State: UP Interface: N/A
Min Tx Inter: 400ms Act Tx Inter: 400ms
Min Rx Inter: 400ms Detect Inter: 2000ms
Rx Count: 0 Tx Count: 910
Connect Type: Indirect Running Up for: 00:00:00
Hold Time: 0ms Auth mode: None
Detect Mode: Async Slot: 0
Protocol: BGP
Version: 1
Diag Info: No Diagnostic
# 在Device B上查看120.2.0.0/24的路由信息,可以看出Device B通过Device B<->Device C<->Device D这条路径与120.2.0.0/24网段通信。
[DeviceB] display ip routing-table 120.2.0.0 24 verbose
Summary Count : 3
Destination: 120.2.0.0/24
Protocol: BGP Process ID: 0
SubProtID: 0x1 Age: 00h24m48s
Cost: 0 Preference: 100
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 300
NibID: 0x15000001 LastAs: 300
AttrID: 0x1 Neighbor: 10.2.0.101
Flags: 0x10060 OrigNextHop: 10.2.0.101
Label: NULL RealNextHop: 10.1.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface10
BkTunnel ID: Invalid BkInterface: N/A
FtnIndex: 0x0 TrafficIndex: N/A
Connector: N/A PathID: 0x0
Destination: 120.2.0.0/24
Protocol: OSPF Process ID: 1
SubProtID: 0x8 Age: 00h26m19s
Cost: 1 Preference: 150
Tag: 1 State: Inactive Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x13000005 LastAs: 0
AttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x41 OrigNextHop: 10.1.0.102
Label: NULL RealNextHop: 10.1.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface10
BkTunnel ID: Invalid BkInterface: N/A
FtnIndex: 0x0 TrafficIndex: N/A
Connector: N/A PathID: 0x0
Destination: 120.2.0.0/24
Protocol: OSPF Process ID: 1
SubProtID: 0x8 Age: 00h26m19s
Cost: 1 Preference: 150
Tag: 1 State: Inactive Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x13000003 LastAs: 0
AttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x41 OrigNextHop: 192.168.0.102
Label: NULL RealNextHop: 192.168.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface30
BkTunnel ID: Invalid BkInterface: N/A
FtnIndex: 0x0 TrafficIndex: N/A
Connector: N/A PathID: 0x0
# 在Device B<->Device C<->Device D链路发生故障后,从Device A上ping Device F的IP地址,可以互通。
[DeviceA] ping 120.2.0.1
Ping 120.1.0.1 (120.2.0.1): 56 data bytes, press CTRL_C to break
56 bytes from 120.2.0.1: icmp_seq=0 ttl=252 time=0.680 ms
56 bytes from 120.2.0.1: icmp_seq=1 ttl=252 time=0.295 ms
56 bytes from 120.2.0.1: icmp_seq=2 ttl=252 time=0.423 ms
56 bytes from 120.2.0.1: icmp_seq=3 ttl=252 time=0.464 ms
56 bytes from 120.2.0.1: icmp_seq=4 ttl=252 time=0.445 ms
--- Ping statistics for 120.2.0.1 ---
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.295/0.461/0.680/0.124 ms
# 在Device B上查看120.2.0.0/24的路由信息,可以看出Device B通过Device B<->Device E<->Device D这条路径与120.2.0.0/24网段通信。
[DeviceB] display ip routing-table 120.2.0.0 24 verbose
Summary Count : 2
Destination: 120.2.0.0/24
Protocol: BGP Process ID: 0
SubProtID: 0x1 Age: 00h00m18s
Cost: 0 Preference: 100
Tag: 0 State: Active Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 300
NibID: 0x15000001 LastAs: 300
AttrID: 0x1 Neighbor: 10.2.0.101
Flags: 0x10060 OrigNextHop: 10.2.0.101
Label: NULL RealNextHop: 192.168.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface30
BkTunnel ID: Invalid BkInterface: N/A
FtnIndex: 0x0 TrafficIndex: N/A
Connector: N/A PathID: 0x0
Destination: 120.2.0.0/24
Protocol: OSPF Process ID: 1
SubProtID: 0x8 Age: 00h00m18s
Cost: 1 Preference: 150
Tag: 1 State: Inactive Adv
OrigTblID: 0x0 OrigVrf: default-vrf
TableID: 0x2 OrigAs: 0
NibID: 0x13000001 LastAs: 0
AttrID: 0xffffffff Neighbor: 0.0.0.0
Flags: 0x41 OrigNextHop: 192.168.0.102
Label: NULL RealNextHop: 192.168.0.102
BkLabel: NULL BkNextHop: N/A
Tunnel ID: Invalid Interface: Vlan-interface30
BkTunnel ID: Invalid BkInterface: N/A
FtnIndex: 0x0 TrafficIndex: N/A
Connector: N/A PathID: 0x0
· Device A:
#
vlan 100
#
interface Vlan-interface100
ip address 120.1.0.1 255.255.255.0
#
bgp 200
router-id 1.1.1.1
peer 120.1.0.2 as-number 100
#
address-family ipv4 unicast
network 120.1.0.0 255.255.255.0
peer 120.1.0.2 enable
#
· Device B:
#
ospf 1
import-route direct
area 0.0.0.0
network 10.1.0.0 0.0.0.255
network 192.168.0.0 0.0.0.255
#
vlan 10
#
vlan 30
#
vlan 100
#
interface Vlan-interface10
ip address 10.1.0.101 255.255.255.0
#
interface Vlan-interface30
ip address 192.168.0.101 255.255.255.0
#
interface Vlan-interface100
ip address 120.1.0.2 255.255.255.0
#
bgp 100
router-id 2.2.2.2
peer 10.2.0.101 as-number 100
peer 10.2.0.101 bfd
peer 13.1.1.101 as-number 100
peer 120.1.0.1 as-number 200
#
address-family ipv4 unicast
preference 255 100 130
peer 10.2.0.101 enable
peer 10.2.0.101 next-hop-local
peer 10.2.0.101 route-policy local-pre export
peer 13.1.1.101 enable
peer 13.1.1.101 next-hop-local
peer 120.1.0.1 enable
#
route-policy local-pre permit node 10
if-match ip address acl 2000
apply local-preference 200
#
acl basic 2000
rule 0 permit source 120.1.0.0 0.0.0.255
#
· Device C:
#
ospf 1
area 0.0.0.0
network 10.1.0.0 0.0.0.255
network 10.2.0.0 0.0.0.255
#
vlan 10
#
vlan 20
#
interface Vlan-interface10
ip address 10.1.0.102 255.255.255.0
#
interface Vlan-interface20
ip address 10.2.0.102 255.255.255.0
#
· Device D
#
ospf 1
import-route direct
area 0.0.0.0
network 10.2.0.0 0.0.0.255
network 13.1.1.0 0.0.0.255
#
vlan 20
#
vlan 40
#
vlan 100
#
interface Vlan-interface20
ip address 10.2.0.101 255.255.255.0
#
interface Vlan-interface40
ip address 13.1.1.101 255.255.255.0
#
interface Vlan-interface100
ip address 120.1.0.2 255.255.255.0
#
bgp 100
router-id 4.4.4.4
peer 10.1.0.101 as-number 100
peer 10.1.0.101 bfd
peer 120.2.0.1 as-number 300
peer 192.168.0.101 as-number 100
#
address-family ipv4 unicast
preference 255 100 130
peer 10.1.0.101 enable
peer 10.1.0.101 next-hop-local
peer 10.1.0.101 route-policy local-pre export
peer 192.168.0.101 enable
peer 192.168.0.101 next-hop-local
peer 120.2.0.1 enable
#
acl basic 2000
rule 0 permit source 120.2.0.0 0.0.0.255
#
· Device E:
#
ospf 1
area 0.0.0.0
network 13.1.1.0 0.0.0.255
network 192.168.0.0 0.0.0.255
#
vlan 30
#
vlan 40
#
interface Vlan-interface30
ip address 192.168.0.102 255.255.255.0
#
interface Vlan-interface40
ip address 13.1.1.102 255.255.255.0
#
· Device F:
#
vlan 100
#
interface Vlan-interface100
ip address 120.2.0.1 255.255.255.0
#
bgp 300
router-id 6.6.6.6
peer 120.2.0.2 as-number 100
#
address-family ipv4 unicast
network 120.2.0.0 255.255.255.0
peer 120.2.0.2 enable
#
某公司内部网络如图7所示,从Device A到Device C有两条转发路径:Link A和Link B。下一跳分别为Device B和Device C。Link A为直连链路,Link B为非直连链路。已知Device C不支持BFD功能,公司希望使用策略路由与BFD联动技术,实现源IP为40.0.0.2的报文优先选择Link B,当Device A和Device B的链路出现故障(如链路down)时,Device A能快速感知,并将流量切换到Link A的链路上。
图7 策略路由与BFD联动配置组网图
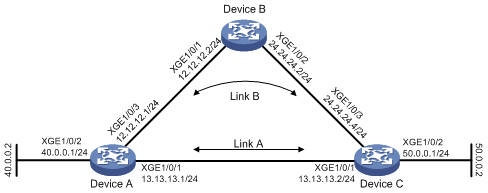
· 由于需要两端设备均支持BFD,才能够使用控制报文方式,本例中Device C不支持BFD,在Device A上配置的BFD功能仅能使用echo报文方式。
· echo报文方式下必须配置echo报文的源IP地址。IP地址可以任意指定,不需要与实际接口地址对应。建议不要将echo报文的源IP地址配置为属于该设备任何一个接口所在网段,避免对端发送大量的ICMP重定向报文造成网络拥塞。
本举例是在S6860-CMW710-R2612版本上进行配置和验证的。
(1) 配置Device A各接口的IP地址
<DeviceA> system-view
[DeviceA] vlan 40
[DeviceA-vlan40] port ten-gigabitethernet 1/0/2
[DeviceA-vlan40] quit
[DeviceA] interface vlan-interface 40
[DeviceA-Vlan-interface40] ip address 40.0.0.1 24
[DeviceA-Vlan-interface40] quit
请参考以上方法配置10.1 图7中其它接口的IP地址,配置步骤这里省略.
(1) 配置Device A
# 配置Device A到Device C 50.0.0.0网段的静态路由。
[DeviceA] ip route-static 50.0.0.0 24 vlan-interface 200 13.13.13.2
(2) 配置Device B
# 配置Device B到Device C 50.0.0.0网段的静态路由。
[DeviceB] ip route-static 50.0.0.0 24 vlan-interface 101 24.24.24.4
# 配置匹配源IP地址为40.0.0.2的IP报文的ACL规则。
[DeviceA] acl number 3010
[DeviceA-acl-adv-3010] rule 0 permit ip source 40.0.0.2 0
[DeviceA-acl-adv-3010] quit
# 配置策略路由aaa,使满足ACL规则报文的下一跳为12.12.12.2,并与track 11绑定。
[DeviceA] policy-based-route aaa permit node 5
[DeviceA-pbr-aaa-5] if-match acl 3010
[DeviceA-pbr-aaa-5] apply next-hop 12.12.12.2 track 11
[DeviceA-pbr-aaa-5] quit
# 在接口上应用路由策略aaa。
[DeviceA] interface vlan-interface 40
[DeviceA-Vlan-interface40] ip policy-based-route aaa
[DeviceA-Vlan-interface40] quit
(1) 配置Device A
# 策略路由支持的BFD会话方式为echo报文方式,该方式下必须配置BFD echo报文的源IP地址。IP地址可以任意指定,不需要与实际接口地址对应。建议不要将BFD echo报文的源IP地址配置为属于该设备任何一个接口所在网段。
[DeviceA] bfd echo-source-ip 3.3.3.3
# 配置发送和接收单跳BFD控制报文的最小时间间隔都为100ms,单跳BFD检测时间倍数为3。
[DeviceA] interface vlan-interface 100
[DeviceA-Vlan-interface100] bfd min-echo-receive-interval 100
[DeviceA-Vlan-interface100] bfd detect-multiplier 3
[DeviceA-Vlan-interface100] quit
[DeviceA] track 11 bfd echo interface vlan-interface 100 remote ip 12.12.12.2 local ip 12.12.12.1
# 查看Device A上源地址为40.0.0.0网段的流量,可以看到该网段当前流量优先从VLAN接口100(即Link B)转发出去。
<DeviceA> reset counters interface
<DeviceA> display counters outbound interface
Interface Total (pkts) Broadcast (pkts) Multicast (pkts) Err (pkts)
XGE1/0/1 0 0 0 0
XGE1/0/2 0 0 0 0
XGE1/0/3 585414 0 0 0
XGE1/0/4 0 0 0 0
XGE1/0/5 0 0 0 0
XGE1/0/6 0 0 0 0
# 查看BFD会话信息,显示BFD会话已被创建,且状态为Up。
[DeviceA] display bfd session verbose
Total Session Num: 1 Up Session Num: 1 Init Mode: Active
IPv4 Session Working Under Echo Mode:
Local Discr: 2049
Source IP: 12.12.12.1 Destination IP: 12.12.12.2
Session State: Up Interface: Vlan-interface100
Min Tx Inter: 100ms Act Tx Inter: 100ms
Min Rx Inter: 100ms Detect Inter: 300ms
Rx Count: 128234 Tx Count: 371950
Connect Type: Direct Running Up for: 00:01:04
Detect Mode: Async Chassis/Slot: 1/0
Protocol: TRACK
Diag Info: No Diagnostic
# 当Device A和Device B间链路故障后,BFD会话Down。
%Dec 10 16:39:46:210 2013 DeviceA BFD/5/BFD_CHANGE_FSM: -MDC=1; Sess[12.12.12.1/
12.12.12.2, LD/RD:2049/2049, Interface:Vlan100, SessType:Echo, LinkType:INET] , S
ta: UP-> DOWN, Diag: 1
%Dec 10 16:39:47:342 2013 DeviceA IFNET/3/PHY_UPDOWN: -MDC=1; Ten-GigabitEtherne
t6/0/5 link status is down.
%Dec 10 16:39:47:343 2013 DeviceA IFNET/5/LINK_UPDOWN: -MDC=1; Line protocol on
the interface Ten-GigabitEthernet1/0/3 is down.
%Dec 10 16:39:47:343 2013 DeviceA IFNET/3/PHY_UPDOWN: -MDC=1; Vlan-interface100
link status is down.
# 清除流量后重新查看Device A上源地址为40.0.0.0网段的流量,可以看到当前流量从VLAN接口200(即Link A)转发出去。
<DeviceA> reset counters interface
<DeviceA> display counters outbound interface
Interface Total (pkts) Broadcast (pkts) Multicast (pkts) Err (pkts)
XGE1/0/1 863764 0 0 0
XGE1/0/2 0 0 0 0
XGE1/0/3 0 0 0 0
XGE1/0/4 0 0 0 0
XGE1/0/5 0 0 0 0
XGE1/0/6 0 0 0 0
· Device A
#
bfd echo-source-ip 3.3.3.3
#
vlan 40
#
vlan 100
#
vlan 200
#
policy-based-route aaa permit node 5
if-match acl 3010
apply next-hop 12.12.12.2 track 11
#
interface Vlan-interface40
ip address 40.0.0.1 255.255.255.0
ip policy-based-route aaa
#
interface Vlan-interface100
ip address 12.12.12.1 255.255.255.0
bfd min-echo-receive-interval 10
bfd detect-multiplier 3
#
interface Vlan-interface200
ip address 13.13.13.1 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 200
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 40
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 100
#
ip route-static 50.0.0.0 24 Vlan-interface200 13.13.13.2
#
ip local policy-based-route aaa
#
acl number 3010
rule 0 permit ip source 40.0.0.2 0
#
track 11 bfd echo interface Vlan-interface100 remote ip 12.12.12.2 local ip 12.
12.12.1
#
· Device B
#
vlan 100 to 101
#
interface NULL0
#
interface Vlan-interface100
ip address 12.12.12.2 255.255.255.0
#
interface Vlan-interface101
ip address 24.24.24.2 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 100
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 101
#
ip route-static 50.0.0.0 24 Vlan-interface101 24.24.24.4
· Device C
#
vlan 50
#
vlan 101
#
vlan 200
#
interface NULL0
#
interface Vlan-interface50
ip address 50.0.0.1 255.255.255.0
#
interface Vlan-interface101
ip address 24.24.24.4 255.255.255.0
#
interface Vlan-interface200
ip address 13.13.13.2 255.255.255.0
#
interface Ten-GigabitEthernet1/0/1
port link-mode bridge
port access vlan 200
#
interface Ten-GigabitEthernet1/0/2
port link-mode bridge
port access vlan 50
#
interface Ten-GigabitEthernet1/0/3
port link-mode bridge
port access vlan 101
#
· H3C S6860系列以太网交换机 三层技术-IP路由配置指导-Release 26xx系列
· H3C S6860系列以太网交换机 三层技术-IP路由命令参考-Release 26xx系列
· H3C S6860系列以太网交换机 可靠性配置指导-Release 26xx系列
· H3C S6860系列以太网交换机 可靠性命令参考-Release 26xx系列
不同款型规格的资料略有差异, 详细信息请向具体销售和400咨询。H3C保留在没有任何通知或提示的情况下对资料内容进行修改的权利!
