- Table of Contents
-
- 13-Security Configuration Guide
- 00-Preface
- 01-DAE proxy configuration
- 02-Password control configuration
- 03-Keychain configuration
- 04-Public key management
- 05-PKI configuration
- 06-IPsec configuration
- 07-SSH configuration
- 08-SSL configuration
- 09-Session management
- 10-Object group configuration
- 11-Attack detection and prevention configuration
- 12-IP-based attack prevention configuration
- 13-IP source guard configuration
- 14-ARP attack protection configuration
- 15-ND attack defense configuration
- 16-uRPF configuration
- 17-SAVA configuration
- 18-Crypto engine configuration
- 19-SMA configuration
- 20-Trust level configuration
- 21-Encryption card user management configuration
- 22-SAVNET configuration
- 23-MACsec configuration
- Related Documents
-
| Title | Size | Download |
|---|---|---|
| 01-DAE proxy configuration | 106.17 KB |
Configuring DAE proxy
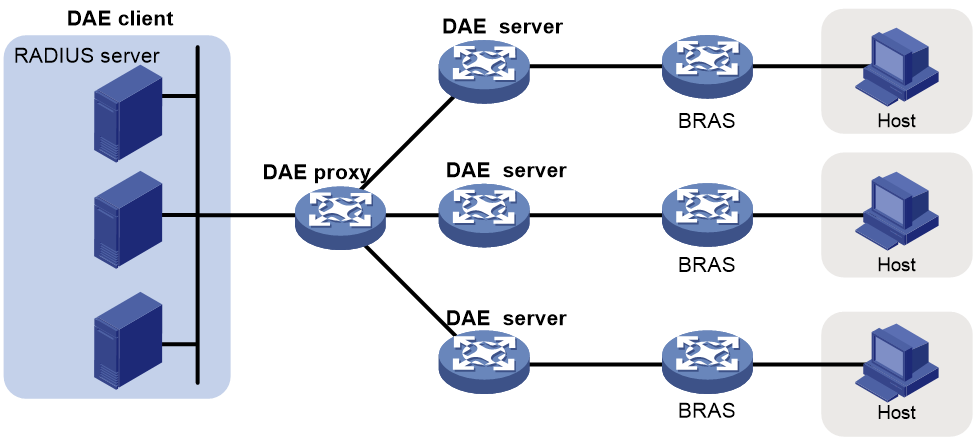
About DAE proxy
The DAE proxy feature enables the device to act as the DAE proxy to forward DAE requests and responses between DAE clients and DAE servers.
DAE
Dynamic Authorization Extensions (DAE) to RADIUS is used to disconnect user sessions or change authorization information for online users.
DAE client/server model
DAE uses the client/server model.
· A DAE client resides on a RADIUS server or a separate host. It initiates DAE requests.
· A DAE server is typically a NAS device. It receives DAE requests from DAE clients and sends DAE responses to DAE clients.
DAE packets
Table 1 describes the categories and types of DAE packets. The device identifies the operation objects by, for example, username and user IP address.
Table 1 DAE packet categories and types
|
Category |
Function |
DAE request |
DAE response |
|
Disconnect Message (DM) |
Disconnects sessions of online users. |
Disconnect-Request (DM_REQ) |
· Disconnect-Acknowledgment (DM_ACK) · Disconnect-Negative Acknowledgment (DM_NAK) |
|
Change of Authorization (CoA) message |
Changes authorization information of online users. |
CoA-Request (COA_REQ) |
· CoA-Acknowledgment (COA_ACK) · CoA-Negative Acknowledgment (COA_NAK) |
Application scenarios
DAE servers process control plane services, including access authentication and user management. BRASs process data plane services, including packet forwarding and traffic control. If you deploy a DAE proxy, the DAE clients need to maintain only the IP address of the DAE proxy, instead of the IP addresses of all DAE server. The configuration and management workload on the DAE clients decreased dramatically.
How DAE proxy works
DAE proxy uses a fixed UDP port to listen for DAE requests from DAE clients and forward DAE responses to DAE clients. At the same time, DAE proxy dynamically enables ephemeral UDP ports to forward DAE requests to DAE servers and receive DAE responses from DAE servers.
The following describes how DAE proxy works:
1. After a user passes authentication and comes online, the DAE client might send a DAE request to the DAE proxy.
2. The DAE proxy searches for the shared key for the source IP address and VPN instance in the request, and uses the key to verify the Authenticator field.
¡ If the shared key is not found or the verification fails, the DAE proxy discards the request.
¡ If the verification succeeds, the DAE proxy creates an ephemeral port to forward the request to the DAE servers in the same VPN as the DAE client.
3. A DAE server resolves the request and deletes user information or changes user authorization information as required. Then, the DAE server encapsulates the processing result in a response and sends the response to the DAE proxy.
4. Upon receiving the response at the ephemeral port, the DAE proxy performs the following tasks:
a. Searches for the shared key by the IP address and VPN instance of the DAE client.
b. Uses the shared key to recalculate and replace the Authenticator field in the response.
c. Sends the response to the DAE client.
DAE proxy waits 10 seconds for the response after it forwards a request. When the timer expires, the DAE proxy ignores the response and does not send any responses to the DAE client.
Protocols and standards
RFC 5176, Dynamic Authorization Extensions to Remote Authentication Dial In User Service (RADIUS)
Prerequisites
Before you configure DAE proxy, perform the following tasks:
· On the interface connected to DAE clients, configure outbound dynamic NAT to translate the source IP address of a RADIUS packet from a DAE server. The translated IP address must be the same as the IP address of the NAS that manages the DAE server on the DAE client. For more information about configuring outbound dynamic NAT, see NAT Configuration Guide.
· Perform the following tasks on the DAE server:
¡ Configure DAE client information. The specified DAE client IP address must be the IP address of the DAE proxy.
¡ (Optional.) Specify the DAE request listening port. This port must be the same as the DAE server listening port configured on the DAE proxy.
¡ (Optional.) Configure a trusted DAE client.
For more information about DAE server configuration, see AAA configuration in BRAS Services Configuration Guide.
Procedure
1. Enter system view.
system-view
2. Enable DAE proxy and enter DAE proxy view.
radius dynamic-author proxy [ listen-port port-number ]
You can specify the DAE proxy listening port number by using this command in system view or using the listen-port port-number command in DAE proxy view. The configurations have the same priority, and the most recent configuration takes effect.
3. Configure a DAE client.
client { ip ipv4-address | ipv6 ipv6-address } [ vpn-instance vpn-instance-name ] [ key { cipher | simple } string ]
By default, no DAE clients are configured.
You can configure multiple DAE clients. The DAE proxy forwards DAE requests from only DAE clients that are configured by using this command.
4. Specify the UDP port for listening for DAE requests from DAE clients.
listen-port port-number
By default, the listening port for DAE requests is 3799.
To prevent loss of DAE requests, disable DAE proxy before you change the listening port.
5. Configure a DAE server.
server { ip ipv4-address | ipv6 ipv6-address } [ vpn-instance vpn-instance-name ]
By default, no DAE servers are configured.
You can configure multiple DAE servers. The DAE proxy forwards DAE requests to and receives DAE responses from only DAE servers that are configured by using this command.
6. Configure the DAE server listening port.
server port dest-port
By default, the DAE server listening port is 3799.
To prevent loss of DAE response packets, disable DAE proxy before you modify this port setting.
Display and maintenance commands for DAE proxy
Execute display commands in any view and reset commands in user view.
|
Task |
Command |
|
Display DAE proxy settings and statistics. |
display radius dynamic-author proxy |
|
Clear DAE proxy statistics. |
reset radius dynamic-author proxy statistics |